Which scenario describes an effect of cyberbullying? Isaac begins to perform poorly in school because he is addicted to video games. Nicole has trouble sleeping at night because she stays up late texting with her friend. Lucas becomes sad because he doesn't have as many online followers as his friends. Mariana thinks about hurting herself after classmates threaten to reveal a secret online. PLEASE HURRY
Answers
Answer:
Mariana thinks about hurting herself after classmates threaten to reveal a secret online.
Explanation:
Answer:
Proof that the person above me is correct ^-^
Explanation:

Related Questions
Given an array arr of strings, the task is to remove the strings that are an anagram of an earlier string, then print the remaining array in sorted order.
Answers
code removes strings from the given array that are anagrams of earlier strings and prints the remaining strings in sorted order.
```python
arr = ["cat", "dog", "act", "god", "tac"]
# Remove the strings that are an anagram of an earlier string
unique_strings = []
seen_anagrams = set()
for string in arr:
sorted_string = ''.join(sorted(string))
if sorted_string not in seen_anagrams:
unique_strings.append(string)
seen_anagrams.add(sorted_string)
# Sort the remaining array
unique_strings.sort()
# Print the remaining array in sorted order
print(unique_strings)
```
We initialize an empty list `unique_strings` to store the unique strings that are not anagrams of any earlier string. We also create a set `seen_anagrams` to keep track of the sorted versions of strings we have encountered so far. We iterate through each string in the given array `arr`. For each string, we sort its characters and check if the sorted version exists in `seen_anagrams`. If it does not exist, it means that the string is not an anagram of any earlier string. We add the string to `unique_strings` and add its sorted version to `seen_anagrams`. Finally, we sort `unique_strings` and print the resulting array.
code removes strings from the given array that are anagrams of earlier strings and prints the remaining strings in sorted order. This ensures that only unique strings are included in the final array.
To know more about array follow the link:
https://brainly.com/question/19634243
#SPJ11
Using a single 8-bit adder, add extra logic to create a circuit that outputs the absolute value of an 8-bit 2 's complement input X. For example, if X =−112
10
, the output should show 112
10
. The 8 -bit adder has the following ports: A
7
,A
0
,B
7
..B
0
,C
in
to the LSB stage, S7.. S
0
,C
0ut
from the MSB stage. Show the block diagram with the 8-bit adder as a black-box.
Answers
If the MSB of X is 0 (indicating a positive number), the outputs S0 to S7 also represent the absolute value of X.
To create a circuit that outputs the absolute value of an 8-bit 2's complement input using a single 8-bit adder, you can follow these steps:
1. Take the 8-bit 2's complement input, X, and pass it through the 8-bit adder as A0 to A7 inputs.
2. Set the B inputs of the adder to a constant value of 0.
3. Connect the C_in input of the adder to a constant value of 1, which represents a carry-in of 1 to the least significant bit (LSB) stage.
4. The S0 to S7 outputs of the adder will give you the sum of X and 0.
5. The C_out output of the adder will indicate whether there is a carry-out from the most significant bit (MSB) stage.
6. Take the outputs S0 to S7 and pass them through some additional logic to generate the absolute value of X.
7. If the MSB of X is 1 (indicating a negative number), and there is a carry-out from the MSB stage (C_out = 1), invert the outputs S0 to S7 using a bitwise NOT operation. This will give you the two's complement of X.
8. If the MSB of X is 1 (indicating a negative number) and there is no carry-out from the MSB stage (C_out = 0), then the outputs S0 to S7 already represent the absolute value of X.
9. If the MSB of X is 0 (indicating a positive number), the outputs S0 to S7 also represent the absolute value of X.
Here is a simplified block diagram of the circuit:
```
+-------+
X --------> | |
A | 8-bit |
0 --------> | Adder | ------------> Absolute Value
B | |
7 --------> | |
+-------+
```
To know more about complement input, visit:
https://brainly.com/question/33340174
#SPJ11
your users are young children
Answers
The program that solves the problem given is indicated below. This is solved using Python.
What is the program that solves the above-mentioned problem?The code is given as follows:
numA = [4, 1, 6, 10, 2, 3, 7, 9, 11, 12, 5, 8]
numB = [2, 12, 10, 11, 1, 3, 7, 9, 4, 8, 5, 6]
while True:
i = 0
userChoice = input("Adding or Multiplying? (a/m) ")
if userChoice == "a":
while i < len(numA):
answer = int(input("What is {} + {} ".format(numA[i],numB[i])))
if answer == numA[i] + numB[i]:
print("Correct!")
else:
print("That's incorrect. The right answer is {}".format(numA[i] + numB[i]))
i += 1
elif userChoice == "m":
while i < len(numA):
answer = int(input("What is {} * {} ".format(numA[i], numB[i])))
if answer == numA[i] * numB[i]:
print("Correct!")
else:
print("that's incorrect. The right answer is {}".format(numA[i] * numB[i]))
i += 1
Learn more about Python:
https://brainly.com/question/25774782
#SPJ1
Full Question:
Your users are young children learning their arithmetic facts. The program will give them a choice of practicing adding or multiplying. You will use two lists of numbers. numA = [4, 1, 6, 10, 2, 3, 7, 9, 11, 12, 5, 8]. numB = [2, 12, 10, 11, 1, 3, 7, 9, 4, 8, 5, 6].
If the user chooses adding, you will ask them to add the first number from each list. Tell them if they are right or wrong. If they are wrong, tell them the correct answer. Then ask them to add the second number in each list and so on. If the user chooses multiplying, then do similar steps but with multiplying.
Whichever operation the user chooses, they will answer 12 questions. Write your program and test it on a sibling, friend, or fellow student.
Explain media streaming and buffering process (Include the buffering diagram)
Answers
If your company increases its market penetration, what is happening?
A.
The target market is growing.
B.
More people in the target market are buying the company's product.
C.
The market saturation of the target market has decreased.
D.
Competitors who offer similar products are entering the market.
D.
Your company collects credit card information from customers.
Answers
Answer: (A, B, E)
A. ) The target market is growing.
B. ) More people in the target market are buying the company's product.
E. ) Your company collects credit card information from customers.
Explanation: Simply what was on the assignment. Correct on Edge.
I hope this helped!
Good luck <3
Answer:
a,b,e like the top one said
Explanation:
this is late but thats okay
automatic processing and effortful processing refer to two types of
Answers
Automatic processing and effortful processing are two types of cognitive processing, with automatic processing being unconscious and effortless, while effortful processing requires conscious effort and attention.
What are the two types of cognitive processing known as automatic processing and effortful processing?Automatic processing and effortful processing refer to two types of cognitive processing or information processing in the field of psychology.
1) Automatic processing: This type of processing refers to the mental processes that occur effortlessly and without conscious awareness. It involves the automatic and involuntary processing of information, such as recognizing familiar faces, understanding simple and familiar words, or performing well-practiced tasks. Automatic processing is fast, efficient, and requires minimal cognitive resources.
2) Effortful processing: In contrast, effortful processing involves the deliberate and conscious allocation of cognitive resources to process information. It requires mental effort, attention, and conscious awareness. Effortful processing is used when encountering new or complex tasks, learning unfamiliar information, solving problems, or engaging in critical thinking. It typically takes longer than automatic processing and requires more cognitive resources.
These two types of processing operate on a continuum, and individuals switch between them depending on the task at hand. Simple and well-learned tasks tend to rely on automatic processing, while complex and novel tasks require effortful processing. Understanding these types of processing helps in comprehending how individuals perceive, process, and respond to information in various cognitive tasks.
Learn more about effortful processing
brainly.com/question/16062609
#SPJ11
Which symbol is used to indicate that a formula may contain an error?
A. green triangle in upper-left corner of cell
B. an orange circle below the formula result
C. green triangle with question mark inside
D. a wavy purple arrow above the formula result
Answers
Answer:A.
Explanation:
Just had this question if is A
Answer:
its A they right
Explanation:
OPERATION SHEET 6.2.2 Given the Neccesary tools materials and equipment identify the common faults and errors of computer when you detached the following Keyboard-PS/2 Mouse-PS/2 Hard disk- IDE cable Floppy disk drive-IDE cable Room disk-IDE CABLE

Answers
Answer: NO MORE TYPING! NO MORE CLICKING! NO MORE MEMORY! NO MORE OPERATING!
The redirection of legitimate user web traffic to illegitimate web sites with the intent to collect personal information is known as
Answers
The redirection of legitimate user web traffic to illegitimate web sites with the intent to collect personal information is known as pharming.
What is pharming?Pharming is known as the act of taking over or hijacking a user's browser settings or when a person runs a background act that rightly redirects users to any kind of malicious site.
Therefore, The redirection of legitimate user web traffic to illegitimate web sites with the intent to collect personal information is known as pharming.
Learn more about pharming from
https://brainly.com/question/14037522
#SPJ1
I
What is a Watermark?
Answers
Can you please help me

Answers
Answer
More info?
Explanation:
Why is it important to look for key details in an article?
Answers
It is important to look for key details in an article because meant to give you the evidence for a wider idea.
Why is it important to identify key details?The main topic or key idea of a text is known to be that which tells you or give you the key details that can be used to describe a text.
Note that Supporting details help us to know better the main idea and as such, It is important to look for key details in an article because meant to give you the evidence for a wider idea.
Learn more about article from
https://brainly.com/question/1070116
#SPJ1
selecting peap as the authentication method does not involve using a client certificate; instead, it uses ms-chap v2 for client authentication.
T/f
Answers
The given statement "Selecting peap as the authentication method does not involve using a client certificate; instead, it uses ms-chap v2 for client authentication" is True because When selecting PEAP (Protected Extensible Authentication Protocol) as the authentication method, the client certificate is not used for authentication. Instead, it utilizes MS-CHAP v2 (Microsoft Challenge Handshake Authentication Protocol version 2) for client authentication.
MS-CHAP v2 is a widely used authentication protocol that provides mutual authentication between a client and a server. It uses a username and password combination for authentication, which is encrypted and sent to the server. The server then compares the encrypted password with its stored copy, and if they match, grants access to the client.
PEAP provides an extra layer of security by creating a secure TLS (Transport Layer Security) tunnel between the client and the server. This ensures that the authentication process is encrypted and protected from eavesdropping or other security threats.
Overall, by using PEAP with MS-CHAP v2, organizations can enhance the security of their wireless networks and ensure that only authorized clients are able to access their resources.
You can learn more about authentication at: brainly.com/question/31525598
#SPJ11
Abdul wants to create a header for a webpage and enters this line: Welcome to Abdul’s webpage! , but the title is smaller than was expected. What is the problem? There is too much text for HTML to treat it as a header. Headers need to begin with the tag. The first tag should not have a slash. Headers cannot contain exclamation points.
Answers
Answer:
I think H1
Explanation:
because h1 can make the letters begger
Answer: The first tag should not have a slash.
Explanation:
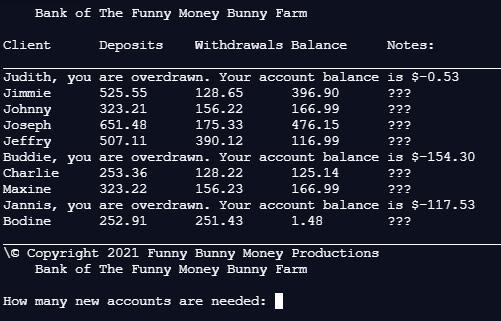
Can someone help me figure out why my else statment is not working?
----------------------------------------------------------------------------------------------------------------------------
print("\tBank of The Funny Money Bunny Farm\n")
print("Client\t\tDeposits\tWithdrawals\tBalance\t\tNotes:")
print("__________________________________________________________________________________________________________________________")
names = ['Judith', 'Jimmie', 'Johnny', 'Joseph', 'Jeffry', 'Buddie', 'Charlie', 'Maxine', 'Jannis', 'Bodine']
deposists = [255.23, 525.55, 323.21, 651.48, 507.11, 101.11, 253.36, 323.22, 611.45, 252.91]
withdrawals = [255.76, 128.65, 156.22, 175.33, 390.12, 255.41, 128.22, 156.23, 728.98, 251.43]
balance = []
notes = []
for i in range(len(names)):
balance.appened(deposits[i] - withdrawals[i])
if(balance < 0):
print((names[i] + ", you are overdrawn. Your account balance is " + "$%.2f"%(balance[i]))
else:
print("" + names[i] + "\t\t" + "%.2f"%(deposits[i]) + "\t\t" + "%.2f"%(withdrawals[i]) + "\t\t" + "%.2f"%(balance[i]) + "\t\t" + notes[i])
print("__________________________________________________________________________________________________________________________")
print("\© Copyright 2021 Funny Bunny Money Productions")
#Main
print("\tBank of The Funny Money Bunny Farm\n")
account = int(input("How many new accounts are needed: "))
for i in range(account):
input("Enter the name of the client: ")
input("Enter the deposist of the client: ")
input("Enter the withdraral of the client: ")
Answers
Answer:
below is a version of your code that runs.
I'm not sure if it does what you expect it to do.

In dance, who is responsible for setting up auditions?
Answers
Answer:
The director
Explanation:
the director is in charge so that is who would do it.
Answer:
dance Instuctors
Explanation:
Instructors are searching for the ideal candidate to fill a spot or create a team/group. By having an audition, students are introduced to the audition process early and are able to become accustomed to everything it entails.
Consider a computer with a 32-bit processor, which uses pages of 4MB and a single-level page table (the simplest one).
a) How many bits will be used for the offset?
b) How many bits will be used for the page number?
c) What is the maximum amount of memory the computer can have? Explain in 1 sentence.
d) How many entries will be in the page table? Explain in 1 sentence.
Answers
The maximum amount of memory the computer can have is determined by the number of bits used to address memory, which in this case is 32 bits
How does the page table help the processor locate data in memory?a) Since the page size is 4MB, the offset will require 22 bits to address all the bytes within a page (2^22 = 4,194,304 bytes).
b) To address all possible pages, the page number will require 32 - 22 = 10 bits (2^10 = 1024 pages).
c) The maximum amount of memory the computer can have is determined by the number of bits used to address memory, which in this case is 32 bits. Thus, the computer can address up to 2^32 = 4GB of memory.
d) The page table will have one entry for each page in the system, which is 1024 in this case, since we are using a single-level page table.
The page table will have 1024 entries, with each entry containing the physical address of the corresponding page in memory.
Learn more about Memory
brainly.com/question/31962912
#SPJ11
Are technological advances in the computer industry good for people in that industry? HUGE HINT: All questions are relevant, and grading will be based on the pros AND cons listed.
Answers
Technological advances in the computer industry offer numerous benefits, including increased efficiency, expanded job opportunities, and streamlined processes. However, they also present challenges such as skill obsolescence, job displacement, and heightened competition.
Technological advances in the computer industry have both positive and negative implications for people working in that industry. Let's explore the pros and cons:
Pros:Increased efficiency and productivity: Technological advancements lead to improved hardware and software, enabling computer professionals to work more efficiently and accomplish tasks faster. This can result in higher productivity and output.Expanded job opportunities: New technologies often create new job roles and specializations. As the computer industry evolves, professionals with skills in emerging technologies have opportunities for career growth and advancement.Automation and streamlining: Technological advancements, such as automation tools and artificial intelligence, can automate repetitive tasks, reducing manual effort and allowing professionals to focus on more complex and strategic work.Cons:Skill obsolescence: Rapid technological advancements may render certain skills obsolete. Professionals must continually update their knowledge and acquire new skills to remain relevant and competitive in the industry.Job displacement: Automation and advancements in artificial intelligence can potentially replace certain job roles. While new opportunities may arise, some individuals may face challenges in adapting to the changing job market.Increased competition: Technological advancements attract more individuals to the computer industry, leading to increased competition for jobs. Professionals need to continually enhance their skills and expertise to stay ahead in a competitive environment.To know more about Technological advances
brainly.com/question/4717909
#SPJ11
When/ where do we need project governance?
Answers
Project governance is needed in various stages and contexts throughout the lifecycle of a project:
1. Project Initiation: During the initial phase, project governance is needed to ensure that the project aligns with the organization's strategic objectives and to establish a clear governance structure. This includes defining roles, responsibilities, and decision-making processes.
2. Planning and Execution: Project governance is essential throughout the planning and execution stages. It helps in defining project objectives, setting up project controls, monitoring progress, managing risks, and making important decisions. It ensures that the project remains on track and aligns with the defined goals.
3. Stakeholder Management: Project governance is needed to engage and manage stakeholders effectively. This involves identifying and involving key stakeholders, ensuring their participation and support, and addressing any conflicts or issues that may arise during the project.
4. Quality Assurance: Project governance plays a crucial role in ensuring quality throughout the project. It involves setting up quality management processes, conducting regular reviews and audits, and enforcing compliance with standards and best practices.
5. Change Management: In case of any changes or deviations from the original project plan, project governance helps in assessing the impact, making necessary adjustments, and obtaining approvals. It ensures that changes are properly managed and controlled.
6. Project Closure: Lastly, project governance is required during the project closure phase. It involves conducting a final review, documenting lessons learned, and ensuring the successful handover of deliverables to the relevant stakeholders.
Project governance provides oversight, accountability, and decision-making frameworks to ensure the successful completion of a project. It helps in maintaining transparency, managing risks, and delivering the desired outcomes.
To know more about Project governance refer to
https://brainly.com/question/30703274
#SPJ11
the owner of a web-based business might want to check to see how many customers are currently visiting her online store or placing orders. what tool allows her to see this activity on the computer in real time?
Answers
A marketing Dashboard, can be used to see how many customers are currently visiting her online store or placing orders. what tool allows her to see this activity on the computer in real time.
What is a marketing dashboard?This refers to the visual display of the most relevant information necessary to keep track of key marketing metrics and to achieve some more marketing objectives.These dashboards can be used to track the performance of your business's online marketing activities and they lets one monitor campaigns and other digital marketing efforts in real-time.In conclusion, it means the visual display of the essential information related to achieving a marketing objective.Hence,To check how many people are currently browsing or making purchases from her online store, she can use a marketing dashboard. How does she use this tool to view this action on the computer in real time.
Read more about marketing dashboard:
brainly.com/question/17354284
#SPJ4
Consider the principles of web server hardening and determine which actions a system administrator should take when deploying a new server. (Select all that apply.)
Secure a guest zone
Use SSH for uploading files
Use the configuration templates provided
Answers
The guidelines are Secure a visitor area Upload files via SSH. Utilize the available configuration templates.
How is the provided used?We'll buy anything you produce, providing the price is reasonable of course. used to describe what must occur or be done to enable something else to occur. You are allowed to take up to $100 every day, providing that there are the funds in your account.
Must a provided be given?conjunction. When you state something will happen if only or provided that another event occurs, you are implying that the first event will only occur if the second event also occurs. As long as no one goes mad in the concept, everything should go smoothly.
To know more about provided visit:
https://brainly.com/question/28463819
#SPJ4
c programming question
Given n, take the sum of the digits of n. If that value has more than one digit, continue reducing in this way until a single-digit number is produced. The input will be a non-negative integer.
Answers
Answer:
int digitSum(int n) {
int sum = 0;
while (n) {
sum += n % 10;
n /= 10;
}
return sum < 10 ? sum : digitSum(sum);
}
int main()
{
int n = 12345;
printf("Digit sum of %d is %d\n", n, digitSum(n));
}
Explanation:
The recursion takes care of the repeated summing in case the sum has more than 1 digit.
Fill is the inside color of a shape.
O
a. True
B. False
Answers
Answer:
True.
Explanation:
Fill describes the color of the area inside a designated shape. This statement is true.
A method of changing unproductive thoughts into constructive ones is called
meditation.
visualization.
positive self-talk.
deep breathing.
Answers
A method of changing unproductive thoughts into constructive ones is called meditation. Hence, option A is correct.
What is unproductive thoughts?An inclination or habit is a mindset that doesn't offer any benefits, effects, or results. Such a mindset pulls the client's focus away from his goals, fulfillment, and empowerment. Negative thoughts may be part of an unproductive mindset.
Overthinking, sometimes referred to as rumination, is when you keep returning to the same idea or event in your mind until it starts to interfere with your life. The two primary forms of overthinking are worrying about the future and brooding on the past.
People who have previously faced difficulty for which they were unprepared may get into the habit of catastrophizing.
Thus, option A is correct.
For more information about unproductive thoughts, click here
https://brainly.com/question/16875515
#SPJ6
Answer:positive self talk
Explanation:
To create a new document using a template, navigate to the _____ tab.
File
Home
New
Page Layout
Answers
Answer:
uhh...
Explanation:
i think it might be the new tab.
write a function solution that, given a string S of N lowercase english letters, returns a string with no instances of three identical consecutive letters
Answers
The following is the solution function that receives a string S of N lowercase English letters and returns a string with no instances of three identical consecutive letters.
The function first checks if the string S is empty or has a single character, in which case it returns the original string. Otherwise, it initializes the new string with the first character of S and a count variable to store the number of consecutive identical characters.
Then, it loops through the remaining characters of S and compares each one with the previous one. If the current character is the same as the previous one, it increments the count and checks if it is less than three. If it is, it appends the current character to the new string. If not, it skips the current character and continues with the next one of the current character different from the previous one, it resets the count to 1 and appends the current character to the new string.
To know more about string visit:
https://brainly.com/question/946868
#SPJ11
You have instructed all administrators to disable all nonessential ports on servers at their sites. why are nonessential protocols a security issue that you should be concerned about?
Answers
The reason nonessential protocols are a security issue that you should be concerned about is that: A. nonessential ports provide additional areas of attack.
What is information security?Information security can be defined as a preventive practice which is typically used to protect an information system (IS) that use, store or transmit information, from potential theft, attack, damage, or unauthorized access, especially through the use of a body of technologies, encryption, frameworks, processes and network engineers.
In Cyber security, the reason nonessential protocols are a security issue that an end user should be concerned about is that nonessential ports would provide additional areas of attack because all protocols have weaknesses based on the principle of least privilege.
Read more on information security here: brainly.com/question/14286078
#SPJ1
Complete Question:
You have instructed all administrators to disable all nonessential ports on servers at their sites. Why are nonessential protocols a security issue that you should be concerned about?
Nonessential ports provide additional areas of attack.
Nonessential ports can't be secured.
Nonessential ports require more administrative effort to secure.
Consider a game that is searched using random restart hill climbing strategy. Assume that the success rate for the game is 25%. What is the maximum number of restarts needed?
Answers
Consider a game in which the hill climbing strategy is randomly restarted. Assume that the game has a 25% success rate. The maximum number of restarts is four.
How do you find the minimum and maximum values?Algebra, a branch of mathematics, aids in the representation of situations or problems as mathematical expressions. To generate a meaningful mathematical expression, variables such as x, y, and z are combined with mathematical operations such as addition, subtraction, multiplication, and division.
Algebra is one of many branches of mathematics. Algebra, which runs through almost all of mathematics, is defined broadly as the study of mathematical symbols and the rules for manipulating these symbols in formulas.
4 because 1/4 = Number of Restarts
So, 1/25% = 1/.25 = 4
When the derivative equals zero, rearrange the function using basic algebraic principles to determine the value of x. This answer includes the x-coordinate of the function's vertex, which is where the maximum or minimum will occur. Returning the solution to the original function to determine the minimum or maximum
Consider a game in which the hill climbing strategy is randomly restarted. Assume that the game has a 25% success rate. The maximum number of restarts is four.
To learn more about algebra, refer to:
https://brainly.com/question/6143254
#SPJ4
8.4.11 code hs help me please
Answers
Code HS is an online platform that provides resources for learning how to code and developing computer science skills. It offers courses and exercises in a variety of programming languages, including Java, Python, and JavaScript.
To better assist you with your question, could you please provide more information about what specifically you need help with related to 8.4.11 code HS. To complete CodeHS 8.4.11, you need to write a program that reads a list of integers, stores them in an ArrayList, and then prints the sum of the integers.
Here is a step-by-step explanation to solve this problem.
1. Import the required libraries:
java
import java.util.ArrayList;
import java.util.Scanner;
2. Create a Scanner object to read the input:
java
Scanner scanner = new Scanner(System.in);
3. Create an ArrayList to store the integers:
java
ArrayList numbers = new ArrayList<>();
To know more about programming visit:
https://brainly.com/question/11023419
#SPJ11
PLEASE ANSWER THESE TWOO❤️❤️

Answers
1 - c
2 - d
Thank you