Which of the following are types of containers that can be used in Windows Server 2016?
Answers
Answer:
Windows Server Container and Hyper-V Container. They differ mainly in the degree of isolation they provide. Windows Server Container uses process and namespace isolation technology to isolate applications.
Explanation:
window server 2016 support two types of container nearly
Related Questions
Write a command that will list the names of all executable files in the working directory, sorted by file size.
Answers
Answer:
The answer is "ls command".
Explanation:
The Is command is often used in Linux to sort the system files according to their size:
#ls – F | grep ‘*$’ -s
And the other regulation they can use is
#ls -Fla | grep ‘^\S*x\S*’
Its name collections of all non-executable files throughout the working directory could be accomplished with the command as follows:
find ! -term+|||-type s-t |find ! - term + ||| - type f-tr
Anna bought a box of blueberries for £7. She used 700 grams for a cheesecake and she has 450 grams left. How much did the blueberries cost per 100 grams?
Answers
0.61 (rounded up)
Explanation:
You add both 700 and 450 which will give you 1150g
You then divide 1150 by 100 which gives you 11.5
Then divide 7 by 11.5 which will give you 0.61 as cost of every 100 grams
Click/press _______ to remove the most recently typed text.
Answers
Answer:
ctrl Z
Explanation:
ctrl Z is the shortcut for undo it will reverse the last thing you did ctrl Y is redo if i accidently did ctrl Z i can do ctrl Y. Hope this helps!
Please send code for both index and style.

Answers
please be more specific about what index and style. sorry i wasn't much help.
MULTI-SELECT
Which of the following is a current development in networking?
need for thicker cables
FDDI
need for better data storage
Ethernet
Answers
Answer:
Need for better data storage
Explanation:
Just got is right on edg
Answer:
C. needs better data storage
Explanation:
What kind of files are automatically blocked in outlook?
A: .doc and .vbs files
B: .xls and .doc files
C: .vbs and .exe files
D: .rtf and .exe files
Answers
Answer:
Guy above is right
Explanation:
Edge 2022
Pat is asked to automate critical security functions like responding to detected threat patterns in an enterprise network. Which of the following should be done by Pat?
a. Use virtual desktop infrastructure
b. Use software-device visibility
c. Implement subnetting
d. Use a software-device network
Answers
The option to be done by Pat is to Use a software-device network.
What is Software-device networking?Software device networking is known to be a kind of technology approach to a network management.
It is one that helps to have a dynamic, programmatically efficient type of network configuration so that one can have a better network performance and monitoring.
Learn more about software-device network from
https://brainly.com/question/4171513
______ is defined as the level of power and control that an individual has over their learning.
A.
Student agency
B.
E-Learning
C.
Educational agency
D.
Independence
Answers
Answer:
B, E-Learning
Explanation:
program a macro on excel with the values: c=0 is equivalent to A=0 but if b is different from C , A takes these values
Answers
The followng program is capable or configuring a macro in excel
Sub MacroExample()
Dim A As Integer
Dim B As Integer
Dim C As Integer
' Set initial values
C = 0
A = 0
' Check if B is different from C
If B <> C Then
' Assign values to A
A = B
End If
' Display the values of A and C in the immediate window
Debug.Print "A = " & A
Debug.Print "C = " & C
End Sub
How does this work ?In this macro, we declare three integer variables: A, B, and C. We set the initial value of C to 0 and A to 0.Then, we check if B is different from C using the <> operator.
If B is indeed different from C, we assign the value of B to A. Finally, the values of A and C are displayed in the immediate window using the Debug.Print statements.
Learn more about Excel:
https://brainly.com/question/24749457
#SPJ1
complete the concept map on computer as outlined below
Answers
Answer:
Here is your answer.
have a great day

Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
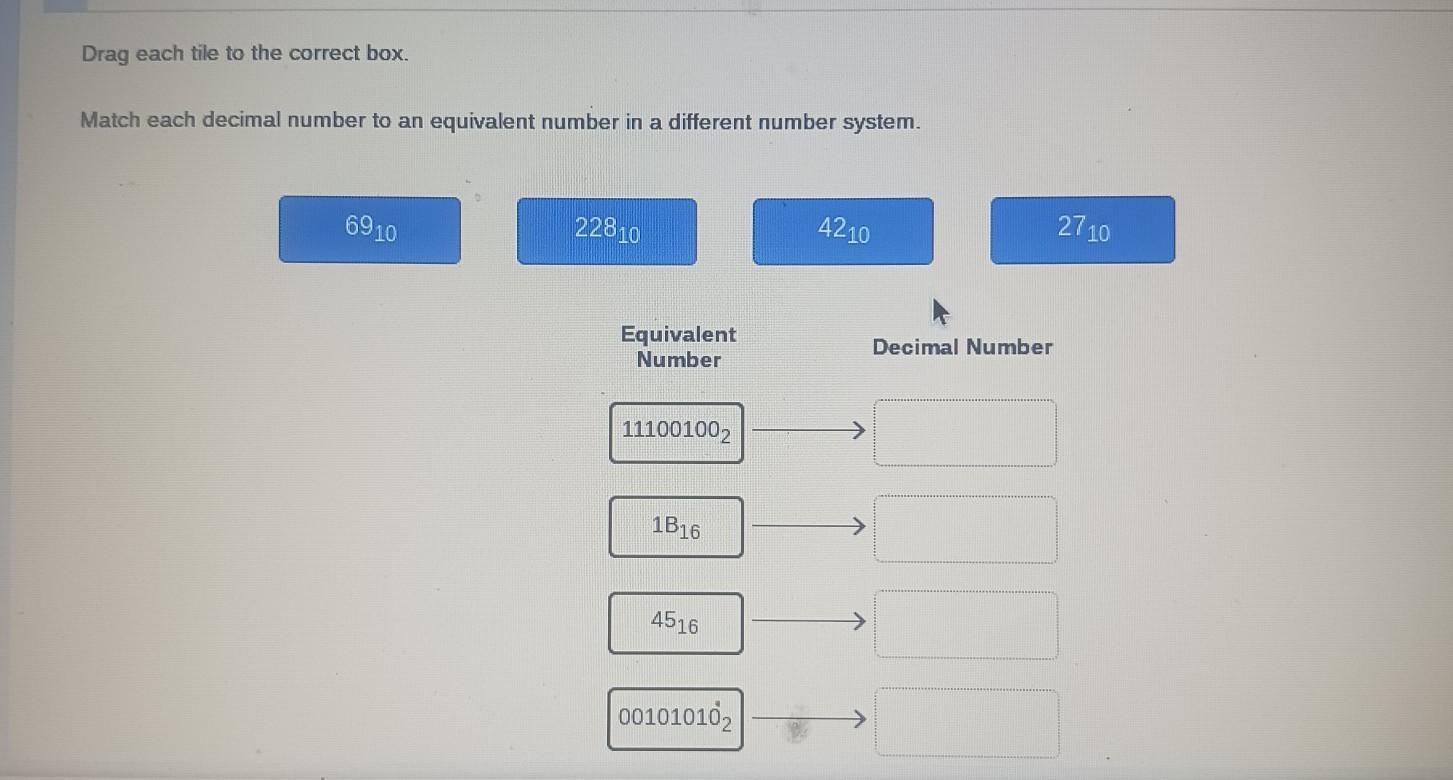
Answers
Explanation:
you can do that with calculator only

Hello! What can I study if I like electronics and programming? please
Answers
Answer:
I want to both code the program and design the electronic component, what major should I study?
It seems, you like Embedded systems. I Suggest you study Electronics and Communication Engineering.
Electronics Engineering courses such as Microprocessors, Embedded systems, Object oriented programming, Digital Signal Analysis, Digital signal processing, etc. will help you learn Hardware programming. Courses such as Electronic Devices and circuits, Electrical Engineering Materials, Advanced Electronics, Control Systems, Instrumentation systems, etc. will help you in hardware design.
The course name varies with the university. you may find the following:
Electronics and Communication Engineering
Electronics and Electrical Engineering
Electrical and Computer Engineering
Electronics and Communication Engineering, etc.
Humans are constantly creating new and innovative technologies designed to simplify difficult processes. Why do you think this is? What might this mean for the future of 3D modeling? Explain.
Answers
Humans are constantly creating new and innovative technologies to simplify difficult processes because it is in our nature to seek ways to make our lives easier and more efficient. We have a strong desire to solve problems and improve upon existing methods.
What is the 3D modeling?In terms of 3D modeling, this means that as technology continues to advance, the process of creating 3D models will become increasingly simpler and more intuitive. This will likely lead to a wider adoption of 3D modeling across various industries, as well as an increase in the complexity and realism of models created.
Additionally, new technologies like virtual reality and augmented reality will allow for more immersive and interactive experiences with 3D models. This will open new possibilities for fields such as architecture, product design, and gaming.
Learn more about 3D modeling from
https://brainly.com/question/27512139
#SPJ1
In this week's lecture, you learned that PowerPoint allows you a great deal of creativity when it comes to developing your presentation. With that in mind, in this week's discussion, we will be investigating more of what PowerPoint offers users as far as creativity goes. Please go to the link below:
Templates for PowerPoint
In your initial post, highlight at least two PowerPoint templates. You will download the templates from the website and attach the blank PowerPoint files to your post. You will address the following prompts as you write your post:
Explain how each template you chose could be used in a specific professional setting. Be detailed.
Describe, in detail, how these templates provide a presenter an advantage that a basic slide design (or no design at all) could not.
Address the potential danger in focusing too much on templates and slide designs. Can a user go too far?
Answers
The template you chose could be used in a specific professional setting.
Form templates can be used in making course forms, school forms and others.Content builder element templates can be used in business presentation, marketing and others. How these templates provide a presenter an advantageTemplates is known to be one that makes the creation of documents to be simply and very easy.
A form template is known to be a kind of a single file that is made up of a lot of supporting files, such as files that tells a person how controls on the form template should look like and others.
A content builder template is one that can make you to be specific in terms of your content and buttress on key points in regards to what you are presenting.
What are the potential danger in focusing too much on templates and slide designs?The dangers are;
Wordiness.A case of information overload for the target audience. Unable to capture the audience attention.Too much information can overwhelm the target audience and also distract them from getting the message that is been passed. Can a user go too far?Yes they can.
Note that Templates can relief human workload and make us to have little stressed, and, also at the same time, they help to boast efficiency. Templates brings up the attention of the audience as well as saves time and money.
Hence, The template you chose could be used in a specific professional setting.
Form templates.Content builder element templates.Learn more about template from
https://brainly.com/question/27326303
#SPJ1


Windows explorer shows the
Answers
Answer:
Windows Explorer is a web browser that displays information from the Internet . The information displayed is from various users organisations,etc
Explanation:
the formality or informality of the information depends on the ones who posts them and the targetted audience.
Which of the following parts apply when delivering an indirect bad news message? Select all that apply.
Question 2 options:
Opening with a buffer statement
Being direct with news
Explaining the situation
Inserting stories and important anecdotes
Keeping details to a minimum
Providing alternatives
Answers
The parts that apply when delivering an indirect bad news message are:
Opening with a buffer statement
Explaining the situation
Keeping details to a minimum
Providing alternatives.
When delivering an indirect bad news message, the following parts apply:
Opening with a buffer statement: Start the message with a neutral or positive statement that prepares the recipient for the upcoming news. This helps soften the impact and reduces defensiveness.Explaining the situation: Provide a clear and concise explanation of the circumstances or reasons behind the bad news. This helps the recipient understand the context and rationale.Keeping details to a minimum: While it is important to provide necessary information, it is also crucial to avoid overwhelming the recipient with excessive details. Focus on the key points to maintain clarity and avoid confusion.Providing alternatives: Offer alternative solutions or options to mitigate the impact of the bad news. This shows empathy and provides the recipient with potential avenues for resolution or improvement.The parts that do not apply in delivering an indirect bad news message are:
Being direct with news: Indirect bad news messages typically involve delivering the news subtly rather than being direct.Inserting stories and important anecdotes: Including stories or anecdotes may not be suitable for an indirect bad news message as it can distract from the main message and dilute its impact.Therefore, the applicable parts for delivering an indirect bad news message are opening with a buffer statement, explaining the situation, keeping details to a minimum, and providing alternatives.
For more such question on bad news message
https://brainly.com/question/22473511
#SPJ8
how to find tax rate using VLOOKUP function in microsoft excel?
Answers
Answer: below
Explanation:
To find a tax rate using the VLOOKUP function in Microsoft Excel, follow these steps:
Set up a table that contains the tax rates. The table should have two columns: one column for the income levels or thresholds and another column for the corresponding tax rates. Make sure the income levels are sorted in ascending order.
For example, your table might look like this:
Income Level Tax Rate
0 0%
10000 10%
20000 15%
30000 20%
In a cell where you want to calculate the tax rate, enter the VLOOKUP formula. The formula syntax for VLOOKUP is as follows:
=VLOOKUP(lookup_value, table_array, col_index_num, [range_lookup])
lookup_value: This is the value you want to lookup, in this case, the income for which you want to find the tax rate.
table_array: This is the range of cells that contains your table, including both the income levels and tax rates.
col_index_num: This is the column number that contains the tax rates within the table. In this case, it would be 2 since the tax rates are in the second column.
[range_lookup]: This is an optional argument. If set to TRUE or omitted, it performs an approximate match. If set to FALSE, it performs an exact match.
For example, if you want to find the tax rate for an income of $25,000 and your table is in cells A1:B5, you can use the following formula:
=VLOOKUP(25000, A1:B5, 2, TRUE)
Press Enter to calculate the formula. The VLOOKUP function will search for the income level closest to $25,000 in the table and return the corresponding tax rate.
Note: Make sure the values you're looking up and the table range are of the same data type (e.g., numbers). Also, ensure that the income levels in the table are sorted in ascending order for the VLOOKUP function to work correctly.
why it is important to follow the procedures and techniques inmaking paper mache?
pleaseee help i needed it right now
Answers
Answer:
otherwise it will go wrong
how do i write a program inputs are two integers, and whose output is the smallest of the two values.
Ex: If the input is:
7
15
the output is:
7
Answers
The program that selects the smaller value of two inputs is:
# Reading two integers from the user
num1 = int(input("Enter the first integer: "))
num2 = int(input("Enter the second integer: "))
# Comparing the two integers and finding the smallest value
if num1 < num2:
smallest = num1
else:
smallest = num2
# Displaying the smallest value
print("The smallest value is:", smallest)
How to write the program?To write a program that takes two integers as input and outputs the smallest of the two values, you can use a simple conditional statement in Python. Here's an example program:
# Reading two integers from the user
num1 = int(input("Enter the first integer: "))
num2 = int(input("Enter the second integer: "))
# Comparing the two integers and finding the smallest value
if num1 < num2:
smallest = num1
else:
smallest = num2
# Displaying the smallest value
print("The smallest value is:", smallest)
In this program, we use the input() function to read two integers from the user and store them in the variables num1 and num2.
Then, we compare the values of num1 and num2 using an if-else statement. If num1 is less than num2, we assign the value of num1 to the variable smallest. Otherwise, if num2 is less than or equal to num1, we assign the value of num2 to smallest.
Finally, we display the smallest value using the print() function.
Learn more about programs at:
https://brainly.com/question/23275071
#SPJ1
Some browsers allow you to open windows in _____ mode, which means the browser will not save your browsing history. incognito.
Answers
While in incognito, a browser may record sessions, but your Ip is neither hidden nor banned.
Why do people utilize incognito?Why do users utilize incognito mode. They use incognito browsing when users don't want their inquiry or browser history recorded to their computer
Is Incognito a VPN substitute?VPNs and Stealth Mode rank as two of the most widely used internet privacy methods. The only thing they both do to hide your browsing history is that. Incognito mode protects your privacy from several other users of the device, however a VPN keeps you invisible and safe from all of the internet.
To know more about browsing history visit:
https://brainly.com/question/26498013
#SPJ4
You completed your 10 for your qualifications in Technology modules last year. In one of the schools around your area there is a shortage of teachers for the Technology subject. The parents want you to explain the importance of the subject because there is a lot of confusion about the subject. You have been chosen to address the parents on the issue relating to the two concepts. Entertain the parents how their children will benefit from doing the subject in schools. 3.1 Briefly explain in 10 main points to the parents how you will teach the subject. [20]
Answers
The presentation to parents about the given concepts and how their children will benefit from doing the subject in schools.
The PresentationGood evening parents,
I appreciate the opportunity to address your concerns about the importance of the Technology subject and how it benefits your children.
I have outlined ten key strategies to effectively instruct the topic:
As part of their Technology education, pupils will acquire practical expertise in areas like coding, analytical thinking, and troubleshooting. The aptitude to master these competencies is crucial in the modern era, and such proficiencies would enable your offspring to effortlessly maneuver and thrive in a world highly influenced by technology.
Technology education cultivates inventiveness and originality by promoting unconventional thinking in students. They will participate in practical activities, constructing and developing solutions to actual dilemmas. This fosters their aptitude for generating distinctive thoughts and putting them into action with efficacy.
Equip your children with future-ready skills by incorporating Technology education into their studies, setting them up for promising career paths. Proficiency in technology-related fields is highly sought-after, paving the way for numerous career paths such as software development, engineering, robotics, and beyond.
By employing captivating teachings, real-life situations, and a focus on essential abilities, studying Technology will undoubtedly yield significant advantages for your kids. I appreciate your focus and believe that by working together, we can offer your children the most exceptional learning adventure.
Practical Skills: Teaching the subject of Technology will equip students with practical skills that they can apply in real-life situations, such as problem-solving, critical thinking, and hands-on technical abilities.
Technological Literacy: The subject will enhance students' technological literacy, enabling them to understand and navigate the increasingly digital world we live in.
Creativity and Innovation: Technology education encourages creativity and innovation by providing students with opportunities to design, create, and invent using various tools and technologies.
Career Opportunities: By studying Technology, students will gain a solid foundation for pursuing careers in fields such as engineering, computer science, robotics, and design, which are in high demand in today's job market.
Digital Citizenship: The subject teaches students about responsible and ethical use of technology, promoting digital citizenship and fostering a safe and respectful online environment.
Problem-Solving: Technology education emphasizes problem-solving skills, empowering students to analyze complex issues, identify solutions, and implement them effectively.
Collaboration and Communication: Students will learn how to work collaboratively on projects, fostering teamwork, communication skills, and the ability to effectively share ideas and knowledge.
Read more about technology education here:
https://brainly.com/question/25110079
#SPJ1
What is the problem with paying only your minimum credit card balance each month?
A. It lowers your credit score
B. You have to pay interest
C. The bank will cancel your credit card
D. All of the above
Answers
Answer:b
Explanation:
Answer: The answer is B.
Explanation: While yes it is important to make at least the minimum payment, its not ideal to carry a balance from month to month (You'll rack up interest charges). And risk falling into debt. Therefore, the answer is B.
Hope this helps!
what is the mean of debugging
Answers
Answer:
the process of identifying and removing errors from computer hardware or software
Explanation:
Essentially just fixing programming errors, mainly in coding or software
a file server with data is consider which of the following asset types? answer tangible neither tangible nor intangible both tangible and intangible intangible
Answers
A file server with data is considered both tangible and intangible.
A file server with data is a type of server that is used to store and manage files and data. It typically includes file storage, sharing, and backup capabilities. It is often used in corporate environments to store and manage large amounts of data, as well as to provide secure access to that data.
A file server is a tangible asset, meaning it is a physical asset that can be touched and seen. It is also an intangible asset because it holds valuable data that can be accessed and used.
This data includes intellectual property, customer information, and other sensitive information that can be used to benefit the business. Therefore, a file server with data is considered both a tangible and intangible asset.
Therefore, the correct answer is c) both tangible and intangible.
For more questions like File server click the link below:
https://brainly.com/question/14522563
#SPJ4
Differentiate between computer engineering and software engineering
Answers
Answer:
Computer engineering is the field in tech that actually involves computers themselves. Software engineering is coding/designing software that runs on computers
Explanation:
state five uses of building
Answers
Hope this helped, but I doubt it(╹◡╹)
1) Housing
2) Power generation (factories and nuclear reactors)
3) Agriculture (greenhouse)
4) Research (Infectious Diseases Research, isolating different viruses to study them in laboratory conditions)
5) Entertainment and leisure (cinemas, shopping centres)
6) Law and governmental buildings
in most operating systems what is running application called?
Answers
Answer:
I believe it is just a task. Since there exists(on windows) the Task Manager application, where you can stop any running task, I think that they are called tasks
Explanation:
In most operating systems, a running application is typically referred to as a process. A process is an instance of a program that is being executed by the operating system. It represents the execution of a set of instructions and includes the program code, data, and resources required for its execution.
Each process has its own virtual address space, which contains the program's code, variables, and dynamically allocated memory. The operating system manages and schedules these processes, allocating system resources such as CPU time, memory, and input/output devices to ensure their proper execution.
The operating system provides various mechanisms to manage processes, such as process creation, termination, scheduling, and inter-process communication.
Learn more about operating systems here:
brainly.com/question/33924668
#SPJ6
Complete the function best_club, which takes the names of three clubs along with their GBM attendance throughout the semester. The function takes two arguments. The first is a list containing three strings that provide the names of the three clubs, and interleaved with the club names is the attendance figures. We will assume that all clubs given in the list have the same number of meetings. For example, consider the following list:
['SBCS', 29, 16, 11, 15, 32, 'WiCS', 11, 51, 42, 33, 20, 'SBGD', 8, 19, 30, 22, 19]
The three club names are SBCS, WiCS and GDC. Each club had five meetings. SBCS's attendance was 29, 16, 11, 15, 32; WiCS attendance was 11, 51, 42, 33, 20; and SBGD's attendance was 8, 19, 30, 22, 19.
The second argument to the function is simply the number of meetings each club held during the semester. For the example above, this argument would be 5.
Example #1:
gbm_attendance = ['SBCS', 29, 16, 11, 15, 32, 'WiCS', 11, 51, 42, 33, 20, 'SBGD', 8, 19, 30, 22, 19]`
num_meetings = 5
Return value: WiCS
Example #2:
gbm_attendance = ['Chess Club', 56, 11, 15, 32, 'Cuddle Club', 11, 21, 42, 20, 'Yogurt Club', 48, 30, 22, 19]
num_meetings = 4
Return value: Yogurt Club
Example #3:
gbm_attendance = ['Running Club', 56, 41, 90, 11, 15, 32, 'Sitting Club', 11, 21, 42, 20, 11, 19, 'Standing Club', 12, 38, 30, 22, 9, 19]
num_meetings = 6
Return value: Running Club
Example #4:
gbm_attendance = ['Lazy Club', 1, 4, 2, 'Hyperactive Club', 100, 98, 102, 'Mathematical Society', 3, 14, 15]
num_meetings = 3
Answers
The function illustrates the use of loops.
Loops are used for repetitive operations.
The function in Python is as follows, where comments are used to explain each line.
#This defines the function
def best_club(gbm_attendance,num_meetings):
#This initializes the club and attendance lists
club = [0]*3; attendance = [0]*3
#This initializes a count variable to 0
count = 0
#This following iteration gets the names of the clubs from gbm_attendance
for i in range(3):
club[i] = gbm_attendance[count]
count+=num_meetings+1
#This initializes a count variable and the total attendance of each club to 0
total = 0; count = 0
#The following iteration calculates the attendance of the first two clubs
for i in range(1,len(gbm_attendance)):
if(isinstance(gbm_attendance[i], int)):
total+=gbm_attendance[i]
else:
attendance[count] = total
count+=1
total = 0
#The following iteration calculates the attendance of the last club
for j in range(2+num_meetings*2+1,len(gbm_attendance)):
attendance[2] += gbm_attendance[j]
#This initializes the largest attendance to 0
maxAttendance = 0; maxIndex = 0
#This iterates through the attendance list
for i in range(3):
#The following if condition calculates the maximum attendance
if attendance[i] > maxAttendance:
maxIndex = i
maxAttendance =attendance[i]
#This prints the club with the maximum attendance
print(club[maxIndex])
At the end of the function, the club with the highest attendance is printed.
See attachment for the complete program
Read more about Python programs at:
https://brainly.com/question/22841107

What characteristics are common among operating systems
Answers
The characteristics are common among operating systems are User Interface,Memory Management,File System,Process Management,Device Management,Security and Networking.
Operating systems share several common characteristics regardless of their specific implementation or purpose. These characteristics are fundamental to their functionality and enable them to manage computer hardware and software effectively.
1. User Interface: Operating systems provide a user interface that allows users to interact with the computer system. This can be in the form of a command line interface (CLI) or a graphical user interface (GUI).
2. Memory Management: Operating systems handle memory allocation and deallocation to ensure efficient utilization of system resources. They manage virtual memory, cache, and provide memory protection to prevent unauthorized access.
3. File System: Operating systems organize and manage files and directories on storage devices. They provide methods for file creation, deletion, and manipulation, as well as file access control and security.
4. Process Management: Operating systems handle the execution and scheduling of processes or tasks. They allocate system resources, such as CPU time and memory, and ensure fair and efficient utilization among different processes.
5. Device Management: Operating systems control and manage peripheral devices such as printers, keyboards, and network interfaces. They provide device drivers and protocols for communication between the hardware and software.
6. Security: Operating systems implement security measures to protect the system and user data from unauthorized access, viruses, and other threats.
This includes user authentication, access control mechanisms, and encryption.
7. Networking: Operating systems facilitate network communication by providing networking protocols and services. They enable applications to connect and exchange data over local and wide-area networks.
These characteristics form the foundation of operating systems and enable them to provide a stable and efficient environment for users and applications to run on a computer system.
For more such questions characteristics,click on
https://brainly.com/question/30995425
#SPJ8
Technician A says the ecm closes the intake air control valve at low speeds .
Technician B says the ACIS adjusts intake manifold length to maximize emissions
Answers
The first technician is the one that is not correct
What would happen with the air control valveTechnician A's statement is incorrect. The ECM (engine control module) does not control the intake air control valve. Instead, it controls the throttle body to regulate the amount of air entering the engine. Technician B's statement is also incorrect. The ACIS (acoustic control induction system) adjusts the length of the intake manifold to optimize power and torque, not to maximize emissions.
Read more on air control valve here:https://brainly.com/question/30106449
#SPJ1