what is the output of this line of code?
print("hello"+"goodbye")
-"hello"+"goodbye"
-hello + goodbye
-hello goodbye
-hellogoodbye
Answers
“hello” + “goodbye”
Answer:
“hello” + “goodbye”
Explanation:
Related Questions
Can someone please tell me what I’m doing wrong ? Please and it’s due on Thursday!!

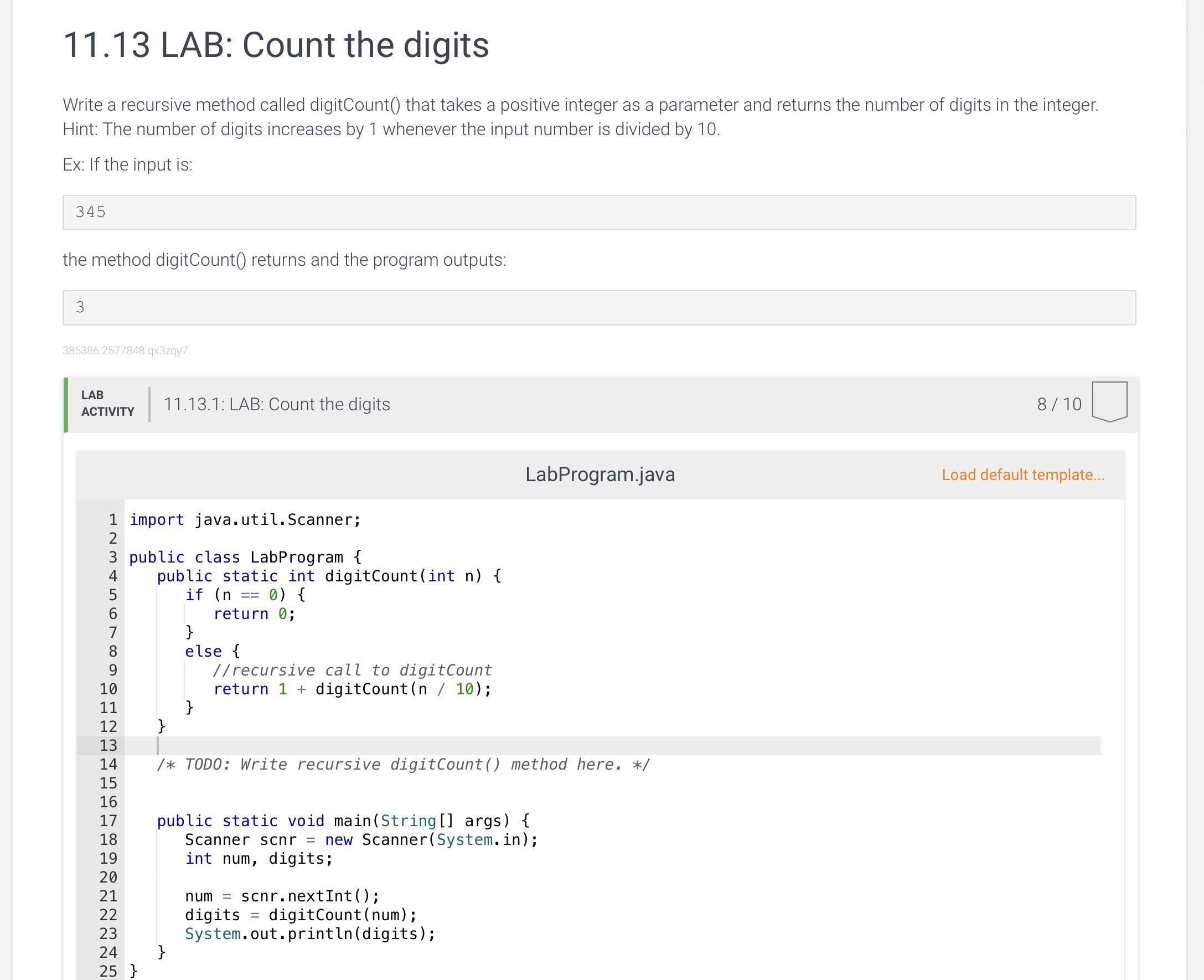
Answers
Answer:
Sure. In Unit test 5, it's looking for 1 instead of 0. You are returning 0 instead of 1.
0 requires 1 digit to express it and should therefore return 1.
In line 6, change the 0 to a 1.
Can we update App Store in any apple device. (because my device is kinda old and if want to download the recent apps it aint showing them). So is it possible to update???
Please help
Answers
Answer:
For me yes i guess you can update an app store in any deviceI'm not sure×_× mello ×_×Using the guidelines below, prepare a spreadsheet to determine if you owe the Federal government or the Federal government owes you. Open a spreadsheet and in cell A1 enter Income Tax Return. In cell A3, enter Wages, Salaries, and Tips and in cell B3, enter $16200.89. In cell A4, enter Taxable Interest and in cell B4, enter 111.90. In cell A5, enter Unemployment Compensation and in cell B5, enter 0. In cell A6, enter Adjusted Gross Income and in cell B6, enter a formula to find the total of B3, B4, and B5. In cell A7, enter Single and in cell B7 enter $8750. In cell A8, enter Taxable Income and in cell B8, enter a formula to subtract the amount in cell B7 from the Adjusted Gross Income. In cell A9, enter Federal Income Tax Withheld and in cell B9, enter $1567.94. In cell A10, enter Earned Income Credit and in cell B10, enter 0 In cell A11, enter Total Payments and in cell B11, enter a formula to add Federal Income Tax Withheld and Earned Income Credit. Next you would use the tax table in the tax booklet to look up the corresponding value for your taxable income. The value from the tax table is $758. In cell A12, enter Tax and in cell B12, enter $758. Since the total payments in cell B11 are greater than the tax in cell B12, you will be receiving a refund. In cell A13, enter Refund and in cell B13, enter a formula to subtract the tax from the total payments. Let's check your answer. In cell B13, you should have $809.94.
Answers
Answer:
Open the Pdf :)
Explanation:
hopefully i got it right
what are the components of computer system??
Answers
Answer:
1. A motherboard.
2. A Central Processing Unit (CPU)
3. A Graphics Processing Unit (GPU), also known as a video card.
4. Random Access Memory (RAM), also known as volatile memory.
5. Storage: Solid State Drive (SSD) or Hard Disk Drive (HDD)
(Please give me brainliest)
How would I set up the code in c++ to read a txt file and store the data? I have the math and the array set up, just not that bit.

Answers
In C++, we use the ifstream class to open the file "example.txt". We then use a while loop to read each line of the file into the line variable. Finally, we print each line using the cout statement.
How can C++ be used to read a txt file and store the data?To read a text file and store the data in C++, you can use the following steps:
Include the necessary libraries: #include <iostream> and #include <fstream>Declare a file stream object: std::ifstream file;Open the file: file.open("filename.txt");Check if the file is open: if (!file.is_open()) { //handle error }Declare variables to store the data from the file: int number; or std::string word;Read the data from the file using a loop: while (file >> number) { //store data } or while (std::getline(file, word)) { //store data }Close the file: file.close();Learn more about C++ at: https://brainly.com/question/28959658
#SPJ1
What is the formula for total current in a series circuit?
Answers
Answer:
Series Circuit Diagram and Formula
This means you can calculate current using V = I/R in which R is 18 Ω and V is 9 V to get a current I of 162 A (amps)
Explanation:
Date:
Difference between Chemical Equivalent and Electroche-
mical equivalent.
Answers
Answer:
chemical equivalent of an element is the value obtained by dividing the atomic weigh of the given element by valency
define a python functions that draw a pinwheel using the pinwheel function that has input paramiters that allows you to change the number of branches and size
then make on that does not use the pinwheel function to draw it
Answers
Start with your draw_pinwheel() function
During each iteration of the loop decide which color to set the turtle to using the color() function
On even iterations, use color1
On odd iterations, use color2
Use an if/else statement to do the decision making
After deciding the color, surround a call to draw_triangle() with begin_fill() and end_fill() so that drawing the triangle creates a colored triangle.
If you have have forgotten, you can use an if/else to check for even/oddness in python as follows.
my_number = 3
if(my_number % 2 == 0): # the remainder of dividing by 2 is 0
print("The number is "+str(my_number))
print("The number is EVEN")
else: # the remainder must be 1
print("The number is "+str(my_number))
print("The number is ODD")
Good luck <3
You decide to test the voltages across several of the components. The measured voltages are:
V1 = 0 Volts
V2 = 12 Volts
V3 = 0 Volts
V4 = 12 Volts
These voltages do not correspond with what should be happening if there is current flowing through each device.
Which statement below describes what is happening?
Zero voltage across the fuse indicates that the fuse is the problem.
12 volts across the resistor and no current indicates that the resistor is blown.
Zero volts across the lamp indicates that the light is bad.
The fuse is bad because there is no current.
Answers
Zero volts across the lamp indicates that the light is bad. The correct option is C.
What is resistor?A resistor is a passive two-terminal electrical component used in circuits to implement electrical resistance.
Resistors have a variety of purposes in electronic circuits, including lowering current flow, adjusting signal levels, dividing voltages, biassing active components, and terminating transmission lines.
After the light bulb, a test of 0 volts shows that there is no resistance in the ground circuit.
At that time, the battery is receiving all of the circuit's voltage (by the path of least resistance), and no voltage is passing through the metre (0 volt reading).
Thus, the correct option is C.
For more details regarding resistor, visit:
https://brainly.com/question/24297401
#SPJ1
Discuss at least 1 Miscrosoft Windows security features that could protect data.
Answers
Answer:
Virus & threat protection.
Explanation:
Monitor threats to your device, run scans, and get updates to help detect the latest threats.
Answer:
User account control.
Explanation:
prevents malware damage. Helps organizations deploy a better-managed desktop.
(PYTHON)
The instructions will be shown down below, along with an example of how the program should come out when finished. Please send a screenshot or a file of the program once finished as the answer.


Answers
Using the knowledge in computational language in JAVA it is possible program should come out when finished.
Writting the code:package numberofcharacters;
import java.util.ArrayList;
public class App {
public static void main(String[] args) {
String toCalculate = "123+98-79÷2*5";
int operator_count = 0;
ArrayList<Character> operators = new ArrayList<>();
for (int i=0; i < toCalculate.length(); i++){
if (toCalculate.charAt(i) == '+' || toCalculate.charAt(i) == '-' ||
toCalculate.charAt(i) == '*' || toCalculate.charAt(i) == '÷' ) {
operator_count++; /*Calculating
number of operators in a String toCalculate
*/
operators.add(toCalculate.charAt(i)); /* Adding that operator to
ArrayList*/
}
}
System.out.println("");
System.out.println("Return Value :" );
String[] retval = toCalculate.split("\\+|\\-|\\*|\\÷", operator_count + 1);
int num1 = Integer.parseInt(retval[0]);
int num2 = 0;
int j = 0;
for (int i = 1; i < retval.length; i++) {
num2 = Integer.parseInt(retval[i]);
char operator = operators.get(j);
if (operator == '+') {
num1 = num1 + num2;
}else if(operator == '-'){
num1 = num1 - num2;
}else if(operator == '÷'){
num1 = num1 / num2;
}else{
num1 = num1 * num2;
}
j++;
}
System.out.println(num1); // Prints the result value
}
}
See more about JAVA at brainly.com/question/29897053
#SPJ1

A security analyst is investigating a call from a user regarding one of the websites receiving a 503: Service unavailable error. The analyst runs a netstat -an command to discover if the webserver is up and listening. The analyst receives the following output:
TCP 10.1.5.2:80 192.168.2.112:60973 TIME_WAIT
TCP 10.1.5.2:80 192.168.2.112:60974 TIME_WAIT
TCP 10.1.5.2:80 192.168.2.112:60975 TIME_WAIT
TCP 10.1.5.2:80 192.168.2.112:60976 TIME_WAIT
TCP 10.1.5.2:80 192.168.2.112:60977 TIME_WAIT
TCP 10.1.5.2:80 192.168.2.112:60978 TIME_WAIT
Which of the following types of attack is the analyst seeing?
A. Buffer overflow
B. Domain hijacking
C. Denial of service
D. Arp poisoning
Answers
Answer:
C. Denial of Service
Explanation:
Denial of service error occurs when the legitimate users are unable to access the system. They are then unable to access the information contained in the system. This can also be a cyber attack on the system in which user are stopped from accessing their personal and important information and then ransom is claimed to retrieve the attack. In such case system resources and information are temporarily unavailable to the users which disrupts the services.
Why do people create web pages?
Answers
Answer:
To grab peoples attention
Explanation:
Answer:
People create web pages to share their passion for whatever they do. People create them to sell buisness products too.
Explanation:
I hoped this helped.
Write a console application that takes an integer input from the user and calculates the factorial of it. Note: factorial of Example Input: 5 Example Output: 1^ * 2^ * 3^ * 4^ * 5=120
Answers
Answer:
The program in Python is as follows:
n = int(input("Integer: "))
product = 1
for i in range(1,n+1):
product*=i
if(i!=n):
print(str(i)+" *",end =" ")
else:
print(i,end =" ")
print(" = ",product)
Explanation:
This prompts the user for integer input
n = int(input("Integer: "))
This initializes the product to 1
product = 1
This iterates through n
for i in range(1,n+1):
This multiplies each digit from 1 to n
product*=i
This generates the output string
if(i!=n):
print(str(i)+" *",end =" ")
else:
print(i,end =" ")
This prints the calculated product (i.e. factorial)
print(" = ",product)
give one word • pressure exerted by a stationary liquid _______. • force in a direction perpendicular to a given surface area _______. • a pair of forces whose resultant is zero _______.
Answers
Answer:
1. Hydrostatic pressure.
2. Pressure.
3. Equilibrium forces.
Explanation:
1. Hydrostatic pressure: pressure exerted by a stationary liquid. It is simply the pressure in a liquid such as water at a specific depth.
Mathematically, hydrostatic pressure is given by the formula;
\( H.P = rho * g * d \)
Where:
H.P is the hydrostatic pressure of a liquid.rho represents the density of a liquid.g is the acceleration due to gravity.d is the depth (height) of a liquid.2. Pressure: it is the force in a direction perpendicular to a given surface area. Thus, it's typically measured in Newton per meters (N/m²).
Mathematically, pressure is given by the formula;
\( Pressure = \frac {Force}{area} \)
3. Equilibrium forces: a pair of forces whose resultant is zero. It is also referred to as balanced forces because the resultant of all the pair of forces acting on a body or system is at equilibrium (balanced).
HELP
When purchasing software or downloading music and games online, how can you make legal choices? Use details to support your answer.
Answers
Answer:
When purchasing software or downloading music and games online, the ways that you make legal choices are to make sure that depending on the place you're downloading the music from. Make sure that the service has obtained permission to be distribution of the music and as such it's legal. Otherwise, it is said to be illegal.
Explanation:
Which of the following tactics can reduce the likihood of injury
Answers
The tactics that can reduce the likelihood of injury in persons whether at work, at home or wherever:
The Tactics to reduce injury risksWearing protective gear such as helmets, knee pads, and safety goggles.
Maintaining proper body mechanics and using correct lifting techniques.
Regularly participating in physical exercise and strength training to improve overall fitness and coordination.
Following traffic rules and wearing seatbelts while driving or using a bicycle.
Ensuring a safe and well-lit environment to minimize the risk of falls or accidents.
Using safety equipment and following guidelines in sports and recreational activities.
Being aware of potential hazards and taking necessary precautions in the workplace or at home.
Read more about injuries here:
https://brainly.com/question/19573072
#SPJ1
what is the difference between hydra and hadoop?
Answers
Hadoop is batch oriented whereas Hydra supports both real-time as well as batch orientation.
The Hadoop library is a framework that allows the distribution of the processing of large data maps across clusters of computers using simple as well as complex programming models. batch-oriented analytics tool to an ecosystem full of multiple sellers in its own orientation, applications, tools, devices, and services has coincided with the rise of the big data market.
What is Hydra?
It’s a distributing multi - task-processing management system that supports batch operations as well as streaming in one go. It uses the help of a tree-based data structure and log algorithms to store data as well as process them across clusters with thousands of individual nodes and vertexes.
Hydra features a Linux-based file system In addition to a job/client management component that automatically allocates new jobs to the cluster and re-schedules the jobs.Know more about Big Data: https://brainly.com/question/28333051
Convert the following to CNF: S→SS|AB|B A→aAAa B→ bBb|bb|Ꜫ C→ CC|a D→ aC|bb
Answers
To convert the given grammar into Chomsky Normal Form (CNF), we need to rewrite the rules and ensure that each production has only two non-terminals or one terminal on the right-hand side. Here is the converted CNF grammar:
1. S → SS | AB | B
2. A → AA
3. A → a
4. B → bBb | bb | ε
5. C → CC | a
6. D → aC | bb
Explanation:
1. The production S → SS has been retained as it is.
2. The production A → aAAa has been split into A → AA and A → a.
3. The production B → bBb has been split into B → bB and B → b.
4. The production B → bb has been kept as it is.
5. The production B → ε (empty string) has been denoted as B → ε.
6. The production C → CC has been retained as it is.
7. The production C → a has been kept as it is.
8. The production D → aC has been kept as it is.
9. The production D → bb has been kept as it is.
In summary, the given grammar has been converted into Chomsky Normal Form (CNF), where each production has either two non-terminals or one terminal on the right-hand side. This form is useful in various parsing and analysis algorithms.
For more questions on parsing, click on:
https://brainly.com/question/13211785
#SPJ8
Answer:
Explanation:
To convert the given grammar to Chomsky Normal Form (CNF), we need to follow a few steps:
Step 1: Eliminate ε-productions (productions that derive the empty string).
Step 2: Eliminate unit productions (productions of the form A → B).
Step 3: Convert long productions (productions with more than two non-terminals) into multiple productions.
Step 4: Convert terminals in remaining productions to new non-terminals.
Step 5: Ensure all productions are in the form A → BC (binary productions).
Applying these steps to the given grammar:
Step 1: Eliminate ε-productions
The given grammar doesn't have any ε-productions.
Step 2: Eliminate unit productions
The given grammar doesn't have any unit productions.
Step 3: Convert long productions
S → SS (Remains the same)
S → AB
A → aAAa
B → bBb
B → bb
C → CC
C → a
D → aC
D → bb
Step 4: Convert terminals
No changes are needed in this step as all terminals are already in the grammar.
Step 5: Ensure binary productions
The given grammar already consists of binary productions.
The converted grammar in Chomsky Normal Form (CNF) is:
S → SS | AB
A → aAAa
B → bBb | bb
C → CC | a
D → aC | bb
Note: The original grammar didn't include the production rules for the non-terminals 'S', 'C', and 'D'. I assumed the missing production rules based on the provided information.
create a view named to10paidinvoices that returns three columns for each vendors
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that create a view named to10paidinvoices that returns three columns for each vendors.
Writting tge code:CREATE OR REPLACE VIEW customer_addresses AS
SELECT
c.customer_id,
email_address,
last_name,
first_name,
ba.line1 AS bill_line1,
ba.line2 AS bill_line2,
ba.city AS bill_city,
ba.state AS bill_state,
ba.zip_code AS bill_zip,
sa.line1 AS ship_line1,
sa.line2 AS ship_line2,
sa.city AS ship_city,
sa.state AS ship_state,
sa.zip_code AS ship_zip
FROM
customers c
JOIN
addresses ba ON c.customer_id = ba.customer_id
AND c.billing_address_id = ba.address_id
JOIN
addresses sa ON c.customer_id = sa.customer_id
AND c.shipping_address_id = sa.address_id;
/*
2
Write a SELECT statement that returns these columns from the customer_addresses
view that you created in exercise 1: customer_id, last_name, first_name, bill_line1.*/
SELECT
customer_id, last_name, first_name, bill_line1
FROM
customer_addresses;
See more about JAVA at brainly.com/question/18502436
#SPJ1

Database systems are exposed to many attacks, including dictionary attack, show with implantation how dictionary attack is launched?(Java or Python) ?
Answers
A type of brute-force attack in which an intruder uses a "dictionary list" of common words and phrases used by businesses and individuals to attempt to crack password-protected databases.
What is a dictionary attack?
A Dictionary Attack is an attack vector used by an attacker to break into a password-protected system by using every word in a dictionary as a password for that system. This type of attack vector is a Brute Force Attack.
The dictionary can contain words from an English dictionary as well as a leaked list of commonly used passwords, which, when combined with common character replacement with numbers, can be very effective and fast at times.
To know more about the dictionary attack, visit: https://brainly.com/question/14313052
#SPJ1
What is the difference between Information Technology and Communication Technology?
Answers
Answer:
Explanation:
information tech is technology that teaches you information, and communication tech is tech that lets you talk to family and friends and meet new people.
Answer:
The main difference between information technology and communication technology is that Information technology is a subject that is use of computers to store, retrieve, transmit and manipulate data, or information, often in the context of business or other enterpise whereas a Communication technology is the use of computers to communicate with family and friends.
which of the following protocols would secure a tunnel for credential exchange using port 636.
A. FTPES
B. SFTP
C. LDAPS
D. DNSSEC
Answers
The protocols would secure a tunnel for credential exchange using port 636 is LDAPS. The correct option is C.
What is LDAPS?In order to secure LDAP connections across the network, the Lightweight Directory Access Protocol Secure (LDAPS) protocol is known to employ a PKI certificate and frequently uses TCP port 636.
TCP 3269 is used for LDAPS connection with a global catalog server. SSL/TLS is negotiated when connecting to ports 636 or 3269 before any LDAP traffic is transmitted.
Therefore, the correct option is C. LDAPS protocols would protect a tunnel for the exchange of credentials utilizing port 636.
To learn more about LDAPS, refer to the link:
https://brainly.com/question/17119741
#SPJ1
Your friend Alicia says to you, “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I don’t think I’m going to do that.” How would you respond to Alicia? Explain.
Answers
Since my friend said “It took me so long to just write my resume. I can’t imagine tailoring it each time I apply for a job. I will respond to Alicia that it is very easy that it does not have to be hard and there are a lot of resume template that are online that can help her to create a task free resume.
What is a resume builder?A resume builder is seen as a form of online app or kind of software that helps to provides a lot of people with interactive forms as well as templates for creating a resume quickly and very easily.
There is the use of Zety Resume Maker as an example that helps to offers tips as well as suggestions to help you make each resume section fast.
Note that the Resume Builder often helps to formats your documents in an automatic way every time you make any change.
Learn more about resume template from
https://brainly.com/question/14218463
#SPJ1
Write a Python program that asks the user for a positive, odd value. Once the value is validated determine if the number is Prime (i.e., divisible only by itself and 1.)
Answers
Answer:
val = int(input("Enter a positive odd value "))
flag = True # let the number entered is alreay prime
if(val > 2 and val%2 == 1): # prime numbers start from 2
half = int(val/2);
for div in range(2,half): # dividing the number from 2 to half of its number
if(val % div == 0): # if completely divisible
print("Not prime")
flag = False # Changing the status of prime number as false
break
if(flag == True):
print(val, "is a prime number")
else:
print("Invalid input, Please Enter a valid positive odd number")
Explanation:
Steps:
1. Let us take input from the user using input() method.
2. Initially, let the number is prime.
3. If the number is negative or even, the go to else part and ask the user for a valid input and terminate the program by giving a message to user.
(We actually check for values greater than 2 because 1 is not considered as a prime number)
4. If the number is positive and odd, then we keep on dividing the number from 2 to half of its number.
(We actually check for values greater than 2 because 1 is not considered as a prime number)
5. If the number is divisible, we change the status to False and break the loop.
6. If the flag is still True, we print that it is a Prime number else we print that it is not a prime number.
Please refer to the comments section as well and the attached image for proper indentation of the program.

Software piracy is acceptable as it helps us obtain software cheaper or sometimes even for free.
true or false
Software licences usually allow you to run a certain number of computers with the same software,
true or false
Answers
Answer:
1: false because it's just scams
2: true
Explanation:
Perfrom traceroute of an ip address in Australia
Answers
How to perform a typical traceroute on an IP address using CMD command is given below:
The StepsIn case you're striving to perform a traceroute operation on an IP address, either using Windows or Mac computer systems, the following guidelines will provide assistance.
Windows users may select the Windows key and R simultaneously, enter "cmd," hit Enter. In comparison, users operating with the Mac OS should navigate through Finder by visiting Applications -> Utilities and double-clicking Terminal.
To get started with the procedure, insert the word "traceroute," and proceed by entering the specific IP address that you desire to locate. Even if searching for information on 203.0.113.1, simply input "traceroute 203.0.113.1." At this stage, submit and wait until the validation is done.
This method ascertains the path taken by packets across the network. It indicates the number of jumps made, along with their response time at every stage. One aspect to bear in mind is some routers/firewalls may block access thereby leading to incomplete outcomes.
Read more about Ip addresses here:
https://brainly.com/question/14219853
#SPJ1
Write a program in c++ to read two integers, calculate and print the smallest
Answers
Answer:
#include<iostream>
using namespace std;
int main (){
int n1, n2;
cout<<"Enter 1st number";
cin>>n1;
cout<<"Enter 2nd number";
cin>>n2;
if(n1<n2){
cout<<"The 1st number is the smallest"<<endl<<" is= "<<n1;
}
else{
cout<<"The 2nd number is the smallest"<<endl<<" is= "<<n2;
}
}
return 0;
discuss MIS as a technology based solution must address all the requirements across any
structure of the organization. This means particularly there are information to be
shared along the organization
Answers
MIS stands for Management Information System, which is a technology-based solution that assists organizations in making strategic decisions. It aids in the efficient organization of information, making it easier to locate, track, and manage. MIS is an essential tool that assists in the streamlining of an organization's operations, resulting in increased productivity and reduced costs.
It is critical for an MIS system to address the needs of any organization's structure. This implies that the information gathered through the MIS should be easily accessible to all levels of the organization. It must be capable of handling a wide range of activities and functions, including financial and accounting data, human resources, production, and inventory management.MIS systems must be scalable to meet the needs of a company as it expands.
The information stored in an MIS should be able to be shared across the organization, from the highest to the lowest level. This feature allows for smooth communication and collaboration among departments and employees, which leads to better decision-making and increased productivity.
Furthermore, MIS systems must provide a comprehensive overview of a company's operations. This implies that it must be capable of tracking and recording all relevant information. It should provide a real-time picture of the company's performance by gathering and analyzing data from a variety of sources. As a result, businesses can take quick action to resolve problems and capitalize on opportunities.
For more such questions on Management Information System, click on:
https://brainly.com/question/14688347
#SPJ8
The process of generating an image from a 2D or 3D model using computer programs is called ........
Answers
Answer:
endering or image synthesis is the process of generating a photorealistic or non-photorealistic image from a 2D or 3D model by means of a computer program. ... The term "rendering" is analogous to the concept of an artist's impression of a scene.