The order by clause can reference columns by their name and what other alternative method?
Answers
The alternative method to referencing columns by their name in the order by clause is by using column positions.
When using the order by clause, you can specify the columns you want to order the results by. The usual way to do this is by referencing the columns by their names, such as "ORDER BY column_name". However, an alternative method is to reference the columns by their positions in the select statement, using the column index number. For example, "ORDER BY 1" will order the results by the first column in the select statement.
In addition to referencing columns by their name, you can also order the results by using column positions in the order by clause.
Learn more about clause visit:
https://brainly.com/question/13440306
#SPJ11
Related Questions
i’m failing this class and i’m stuck on this one, this is the code from the last lesson:
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a":4, "b":3, "c":2, "d":1, "f":0}
if weighted == 1 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
return "Your GPA score is: " + str(dictionary[grade])
else:
return"Invalid"
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes, 0 = no) "))))
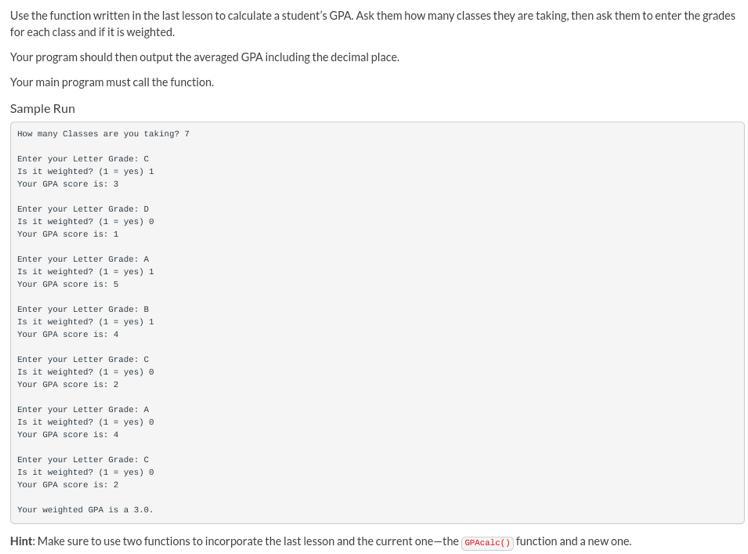
Answers
lst=([])
def avgGPA(lst1):
total = 0
count = 0
for x in lst:
if type(x) == int:
total += x
count += 1
return total/count
def GPAcalc(grade, weighted):
grade = grade.lower()
dictionary = {"a": 4, "b": 3, "c": 2, "d": 1, "f": 0}
if weighted == 1 and grade in dictionary:
lst.append(dictionary[grade]+1)
return "Your GPA score is: " + str(dictionary[grade] + 1)
elif weighted == 0 and grade in dictionary:
lst.append(dictionary[grade])
return "Your GPA score is: " + str(dictionary[grade])
else:
lst.append("Invalid")
return "Invalid"
classes = int(input("How many Classes are you taking? "))
i = 0
while i < classes:
print(GPAcalc(input("Enter your Letter Grade: "), int(input("Is it weighted? (1 = yes) "))))
i += 1
print("Your weighted GPA is a "+str(avgGPA(lst)))
If you need me to change any code, I'll do my best. I hope this helps!
PLS HELP ON THIS ACSL QUESTION. ASAP!!! HELP NEEDED. WILL GIVE BRAINLIEST TO CORRECT RESPONSE. Pls answer only if you are sure it's correct!! Check IMAGE FOR THE PROBLEM!! ASAP.

Answers
The given program takes input values from the user and performs several operations on a 4x4 array "a".
What is the program about?Here are the operations performed by the program step-by-step:
Initialize a variable "d" to 0.
Take input values for the 4x4 array "a" using nested for loops.
For each element in the array, check if dividing the element by 1 gives a non-integer result. If yes, replace the element with 1, else replace it with the integer value of the quotient of the element divided by 1.
For each element in the array, check if it is greater than 99. If yes, replace it with the remainder when divided by 100. Then replace the element with the remainder when divided by 3.
Add the diagonal elements and anti-diagonal elements of the array to the variable "d".
Learn more about program on
https://brainly.com/question/26134656
#SPJ1
Amber, a network administrator, is conducting VoIP training for other IT team members. Melanie, a new team member, is confused about the difference between latency and jitter. What is the BEST way to explain the difference
Answers
The best way to explain the difference is option A: Jitter is the up and down variation in latency.
What are VoIP services?Voice over Internet Protocol (VoIP), is known to be a form of a technology that gives one room to be able to make voice calls via the use of a broadband Internet connection.
In the case above, The best way to explain the difference is option A: Jitter is the up and down variation in latency as it is the only best option.
See options below
Jitter is the up and down variation in latency.
Latency is the up and down variation in jitter.
Jitter is caused by an inadequate codec.
Latency is caused by sampling; jitter is not.
Learn more about latency from
https://brainly.com/question/27013190
#SPJ1
which action best demostrates the transermation of energy
Answers
The transformation of energy occurs in various ways, including chemical, mechanical, electrical, radiant, and nuclear energy. However, the most efficient action that best demonstrates the transformation of energy is through the process of photosynthesis.
The process of photosynthesis is the most efficient way of demonstrating the transformation of energy because it involves the conversion of light energy into chemical energy by the chlorophyll pigments present in the leaves of plants. In photosynthesis, plants absorb energy from sunlight and use carbon dioxide and water to produce glucose, a type of sugar that is used as an energy source for the plant.
The chemical energy produced is then used to fuel all other processes in the plant's life cycle.In the process of photosynthesis, light energy is transformed into chemical energy. The light energy is converted into chemical energy that is used to fuel other processes in the plant, such as growth and reproduction. Therefore, photosynthesis demonstrates the transformation of energy in a very efficient way that is both important and fundamental to the growth and development of plants and other living organisms.
Additionally, photosynthesis is essential to the Earth's ecosystem because it produces oxygen and reduces the amount of carbon dioxide in the atmosphere.
To know more about efficient visit:
https://brainly.com/question/30861596
#SPJ11
Which type of data storage allows computers to read and write to the memory while the computer is powered on?
Hard drive
RAM
ROM
Virtual memory
Answers
Answer:
RAM
Explanation:
RAM is Random Access Memory, which means you can access whenever as long as it is powered on.
The user is told to guess a number between one and 10.
Which responses from the user could cause the program to halt with an error statement? Choose two options.
two
2.5
12
-3
0
Answers
Answer:
0 and -3
Explanation:
These two options do not fall within 1 and 10.
Answer:
2.5 and two
are the answers
Read the code snippet below and determine which markup language it is:
Sound Card
Creative Labs
Sound Blaster Live
80.00
The code is an example of the (Blank) markup language.
Answers
Answer:
Sound Card
Explanation:
which is an example of an operating system with only command line interface? a. UNIX b. DOSO c. Mac OSO d. windows
Answers
An example of an operating system with only a command-line interface is UNIX. UNIX is a popular operating system that has been widely used since the 1970s, particularly in academic and research settings.
UNIX is known for its powerful command-line interface, which allows users to interact with the system using text-based commands rather than a graphical user interface. This interface provides users with a high degree of flexibility and control over the system, allowing them to perform a wide range of tasks quickly and efficiently. Other operating systems, such as DOS, also feature a command-line interface, but UNIX is particularly well-known for its advanced command-line capabilities and its popularity among developers and power users.
Find out more about the operating system
at brainly.com/question/5430004
#SPJ4
Type the correct answer in the box. Spell all words correctly.
Which software is used to play, create, and modify audio and video files?
_______software is used to play, create, and modify audio and video files.

Answers
Answer:
Adobe Premire pro
Explanation:
Answer:
video editing
Explanation:
insert a function in cell h18 to calculate the total number of orders based on entries in column a.
Answers
=COUNTA(A5:A13). Get the number of entries in a number field that is part of a range or array of numbers by using the COUNT function.
How can the text from cell A8 be displayed using a formula in cell B8?To display the text from cell A8 in all uppercase letters, enter a formula in cell B8. Click the Text button under the Function Library group on the Formulas tab. From the list, choose UPPER. In the Text box, enter "A8," then press OK.
What is the cell count formula?The number of cells in your suspension can be determined using the formula below: Total number of cells equals (total cells counted)/(4 squares counted)*10-4*initial volume*dilution factor; Observe.
To know more about array visit:-
https://brainly.com/question/19570024
#SPJ1
A company transports many chemical Products from one location to another on behalf of a registered Customer. Each transport operation is called a Job, which involves picking up one or more Loads of the same product from a customer's requested start location and delivers it to a customer's requested destination. A
unique number is given for each Job and for each Load when they are created. A Load is transported using a particular Transport Unit, which consists of a lorry, a driver, a container (for carrying the product) and occasionally specialist loading equipment (such as Jacks and Pumps). A container is fixed to a trailer so it needs to be coupled to a lorry at the start of a Job. Transport operations are run from 5 regional Depots. Jobs are allocated to individual depots to service. Depots are usually located near to pick up points such as chemical plants. Depots hold, manage and maintain their own transport units which are permanently allocated to them to
service Jobs. A container, and sometimes associated loading equipment, may on occasions be left at destinations or pick-ups after a Job is finished. But normally transport units are held at the base Depot they belong.
1. draw an ER diagram for the described database.
2.Map the logical data model for the ER diagram you drew in
1 above. Show the resultant relations at each Normal Form up to 3NF
3. Present the physical data model.
Answers
In addition to having precise data types, constraints, and indexes for each attribute in the tables, the physical data model is a reflection of the logical data model.
In programming, a data types defines the type of data that can be stored and manipulated in a program. Common data types include integers, floating-point numbers, characters, strings, and Boolean values. Each data type has a range of possible values and operations that can be performed on those values. For example, integers can be added, subtracted, multiplied, and divided, while strings can be concatenated and searched. Choosing the appropriate data type for a variable is important to ensure that it can store the necessary information and that the program runs efficiently. In addition to built-in data types, many programming languages allow for the creation of custom data types, such as structs and classes, which can be used to represent complex data structures.
Learn more about Data types here:
https://brainly.com/question/18033010
#SPJ11
What is the process that creates a shortcut on your taskbar?
pinning
O saving
sharing
O tying
Answers
Answer:
A. Pinning
Explanation:
I just took the test.
Answer:
a
Explanation:
Why should even small-sized companies be vigilant about security?
Answers
Answer:businesses systems and data are constantly in danger from hackers,malware,rogue employees, system failure and much more
Explanation:
Wanda is taking photos using a lens that sees and records a very narrow view with a focal length longer than 60mm. When her friend asks what type of lens she is using for their photography outing,
Answers
Answer:
a telephoto lensExplanation: It's on Quizlet lolAnd I got it correct on the test...
It provides an instant 2x optical zoom and has a focal length that is twice that of the primary lens. Additionally, it has a limited field of view, which causes distant things to resemble those that are nearby.
What role of telephoto lens in taking photos?Simply put, a telephoto lens deceives the eye into thinking a topic is closer than it actually is. This may be the best option for photographers who are physically unable to go close to their subjects or who are concerned for their safety.
With a telephoto lens, the background elements appear larger and nearer to the foreground elements. The converse is true with wide-angle lenses, which make background elements appear smaller and farther away from the camera.
Therefore, a telephoto lens Wanda uses a lens longer than 60 mm in focal length to capture images with a very small field of view. When her friend inquires about the lens she will be using on their photographic excursion.
Learn more about telephoto lens here:
https://brainly.com/question/15599633
#SPJ2
Janice’s grandmother stayed at home and took care of her family while her grandfather worked. Today Janice lives on her own and has a full time job. What factor that affects the labor market is represented in this situation? a. Population shift b. Social change c. World event d. Government action
Answers
Answer:
Social change
Explanation:
The factor that affects the labor market as represented in this situation is Social change.
What is social change?Social change is known to be the way that which people often use in interaction with others. It is also known as the way that relationships changes cultural and social institutions in course of time.
Conclusively, social changes do have long‐term effects such as industrial revolution and it is the factor that influence the labor market as shown in this situation above.
Learn more about Social change from
https://brainly.com/question/13391889
you need to find all files in the /home/gshant directory that are larger than 300k. you change your directory to /home/gshant. what would you enter at the command prompt to find these files?
Answers
You can search for a file or directory on your file system with the locate command. Matches, which can be files, directories, symbolic links, system devices, etc., can be found and immediately processed within the same command by using the -exec flag (find -exec).
What does locate command mean?A UNIX command line tool for traversing a file hierarchy is the find command. It can be used to look for files and folders and then operate on them in the future. It allows for searching by name, creation date, modification date, owner, and permissions for files and folders.Using the criteria you specify, the find command searches and locates the list of files and directories for files that match the inputs. Use the find command to locate files according to a number of criteria, including permissions, users, groups, file kinds, dates, and sizes.You can search for a file or directory on your file system with the locate command. Matches, which can be files, directories, symbolic links, system devices, etc., can be found and immediately processed within the same command by using the -exec flag (find -exec).To learn more about UNIX command line tool refer to:
https://brainly.com/question/9362230
#SPJ4
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
Which range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE?
A. 10.120.160.0 to 10.120.168.0
B. 10.120.160.0 to 10.127.255.255
C. 10.120.160.0 to 10.120.191.255
D. 10.120.160.0 to 10.120.167.255
Answers
10.120.160.0 to 10.120.167.255 is the range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE.
Thus option D is correct.
What is IP addresses?An Internet Protocol address (IP address) is a numerical label such as 192.0.2.1 that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification and location addressing.
Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s.
IP addresses are written and displayed in human-readable notations, such as 192.0.2.1 in IPv4, and 2001:db8:0:1234:0:567:8:1 in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., 192.0.2.1/24, which is equivalent to the historically used subnet mask 255.255.255.0.
Learn more about IP addresses
https://brainly.com/question/16011753
#SPJ4
Takes a 3-letter String parameter. Returns true if the second and
third characters are “ix”
Python and using function
Answers
Answer:
def ix(s):
return s[1:3]=="ix"
Explanation:
in this assignment, you will have as reference one c program called arithmetic sum.c and its corresponding object file arithmetic sum.c declares and initializes five variables and calculate the sum of these variables. its corresponding object file is called arithmetic sum.o. we are given two mysterious object codes: one.o and two.o (stored inside the test folder). one.o is generated from one.c. two.o is generated from two.c. the syntax structures of one.c and two.c are extremely similar to arithmetic sum.c.
Answers
To answer this question, you need to analyze the two mysterious object codes (one.o and two.o) and compare them to the object code for arithmetic sum.o.
What is arithmetic?
Mathematical arithmetic is the study of the properties of the standard operations on numbers, such as addition, subtraction, multiplication, schism, exponentiation, and root extraction. With the Peano axioms, an Italian mathematician from the 19th century who is still influential in the modern field of mathematical logic, Giuseppe Peano formalised arithmetic. There are only a few ancient artefacts that can be used to date the invention of addition and subtraction. The best-known of these is the disputedly interpreted Ishango bone from central Africa, which dates to between 20,000 and 18,000 BC.
By doing this, you will be able to determine the differences between the two files, and from there, you can make educated guesses as to what the two mysterious object codes do. For example, if one.o is larger than arithmetic sum.o, it is likely that one.c is doing something more complex or has more lines of code than arithmetic sum.c.
To learn more about arithmetic
https://brainly.com/question/22495842
#SPJ1
Test: Unit 1
Highlight both variables in the following code.
1 name =
input("What is your name?")
2 print("Hello
+ name)
3
Click and drag to highlight. Hold down the Cmd key (Mac) or Ctrl key (Windows) for multip!
Answers
The words in bold are the variables.
1 name = input("What if your name?");
2 print("Hello" + name)
does compliance with the nec always result in an electrical installation that is adequate, safe, and efficient? why?
Answers
Compliance with them and appropriate maintenance lead to an installation that is generally risk-free but may not be effective, practical, or sufficient for good service or future growth of electrical consumption.
What does NEC intend to achieve?A widely used model code for the installation of electrical parts and systems is the NEC (NFPA 70 of the National Fire Protection Association).
What phrase does the NEC employ to describe an approach that is permitted but not necessary?The permissive rules of this Code are those that specify acts that are permitted but not necessary, are typically employed to explain options or alternate procedures, and are identified by the use of the terms shall be permitted or shall not be required.
To know more about installation visit:-
https://brainly.com/question/14356368
#SPJ4
when encountering an ipv4-only router, an ipv6 datagram is
Answers
Base header (40 bytes) and payload (up to 65,536 bytes) are the two parts of an IPv6 datagram. Payload also comprises an extension header that is optional.
Explain about the ipv6 datagram?By containing only the information required for forwarding the IP datagram, IPv6 has a significantly simpler packet header than IPv4 does. A fixed length header for IPv4 is 40 bytes in size. The routers can handle IPv6 datagram packets more quickly thanks to fixed length IPv6 headers.
An upper-layer protocol data unit, one or more IPv6 extension headers, and an IPv6 basic header make up an IPv6 packet (PDU). Its payload, which might be an ICMPv6 packet, a TCP packet, or a UDP packet, plus the upper-layer protocol header make up an upper-layer PDU. A datagram is a self-contained message that is mostly used for wireless communication. Its source and destination addresses are listed in the header.
To learn more about ipv6 datagram refer to:
https://brainly.com/question/15733937
#SPJ4
What is displayed when you run the following program?
print("30 + 10")
print(5 +8)
Answers
Answer:
print("30 + 10") will print 30 + 10 print(5+8) will print 13
Explanation:
This is in python the "print" will simply print text.
Write a public static method diagSum, which takes a 2d array of int values as a parameter, and returns the sum of the elements in the lead diagonal as an int value. The lead diagonal is defined as the diagonal line of values starting in the top left corner and proceeding one step right and down for each value until either the bottom or right edge of the array is reached. For example, in the array represented below, the numbers in red make up the lead diagonal
Answers
A 2d array (i.e. 2 dimensional array) represents its elements in rows and columns
The program in JavaThe method in Java, where comments are used to explain each line is as follows
//This defines the method
public static int diagSum(int[][] myArray) {
//This initializes sum to 0
int sum = 0;
//This iterates through each row of the array
for (int i = 0; i < myArray.length; i++) {
//This calculates the sum of the diagonals
sum+=myArray[i][i];
}
//This returns the sum
return sum;
}
Read more about methods at:
https://brainly.com/question/15969952
Select the correct answer. crystal detected a problem in a computer network, due to which she could not send or receive data within the network. she pings computers from the administrator computer. which problem is she trying to detect?
a. incorrect password
b. same ip address of two computers
c. faulty network interface card (nic)
d. erroneous changes in the configuration settings
Answers
Faulty network interface card (nic). A network interface card (NIC) is a piece of hardware required for network connectivity on a computer.
What is network interface card ?A computer's connection to a computer network is made possible by a network interface controller, a piece of hardware. Expansion cards that hooked into a computer bus were frequently used to create early network interface controllers.A dedicated, permanent connection to a network is provided by a NIC for a computer. It puts into practise the physical layer hardware required for interacting with a data link layer standard, like Ethernet or Wi-Fi. Each card serves as a device and has the ability to prepare, transmit, and manage data flow on the network.An unstable network connection should be one of the first signs that NIC problems are about to start. You probably have a NIC problem if you find that your connection constantly dropping out for lengths of time that can range from a few seconds to hours.To learn more about NIC refer :
https://brainly.com/question/20689912
#SPJ4
Which of the following statements about version control are true? Select 3 options.
Early version control systems needed to use locks to keep files synchronized, but newer version control systems do not use locks at all.
With distributed version control, multiple copies of the entire project are maintained on the developers’ computers.
Version control systems can only be used by teams of developers, rather than individuals.
Git and Mercurial are examples of distributed version control systems.
In a centralized version control system, the project files are stored in a repository or database on a server
Answers
Answer:
In a centralized version control system, the project files are stored in a repository or database on a server
Git and Mercurial are examples of distributed version control systems.
With distributed version control, multiple copies of the entire project are maintained on the developers’ computers.
Explanation:
Your Welcome!
The statements about version control that are true include the following:
B. With distributed version control, multiple copies of the entire project are maintained on the developers’ computers.
D. Git and Mercurial are examples of distributed version control systems.
E. In a centralized version control system, the project files are stored in a repository or database on a server.
Version control is also referred to as source control and it can be defined as a process through which changes to a file, set of files and software codes over time, are tracked, recorded and managed, especially for easy recall and modification of specific versions in the future. A common example of a version control system that is used by software developers across the world is Git.
In Computer science, there are two main types of version control system and these include:
I. Distributed version control system.
II. Centralized version control system.
Basically, the statements about version control that are true include the following:
Multiple copies of an entire project can be maintained on a developer's computers through the use of distributed version control.Git and Mercurial are common examples of distributed version control systems.Project files are stored in a repository or database on a server in a centralized version control system.Read more on version control here: https://brainly.com/question/14213984
Write a BASIC program to calculate the area of a rectangle
Answers
'#include stdio.h' printf ("Area of the rectangle=%d",area); int main() int width=5, int height=10, and int area=width times height.
How do you express a rectangle's area in Python?By utilising the formula Area = width * height, we can determine the area of a rectangle by passing these values as parameters to the function. Next, we use the equation 2 * (width + height) to determine a rectangle's perimeter.
What does a C program's structure entail?Documentation, Link, Definition, Global Declaration, Main() Function, and Subprograms are the six sections that make up a C programme. The main component of the C programme must be included, while the other sections are optional.
To know more about int main visit:-
https://brainly.com/question/18723502
#SPJ1
What is the output of the following? *
public class output1
{
public static void main(String str[])
{
int a=1,b=2, c=3;
boolean f1, f2;
f1=a<=b++;
f2=C+9>b++;
System.out.println(f1 + " " + f2);
}
}
a false true
b true false
c 8
d 6
Answers
Answer:
A
Explanation:
well there are numbers and time
T/F In Mac OS X, Sharing Only accounts can log on to the local Mac computer and access shared files and printers on other computers.
Answers
False: In Mac OS X, Sharing Only accounts can log on to the local Mac computer and access shared files and printers on other computers.
The given statement, "In Mac OS X, Sharing Only accounts can log on to the local Mac computer and access shared files and printers on other computers," is a bit tricky, but it is a false statement.
There is no sharing-only user account type in Mac OS X. A sharing-only account is a user account that has been configured to allow other users to access shared resources on the local machine. These accounts cannot be used to log in to the computer and do not have any privileges beyond those required to access shared resources. Only user accounts with login access can log on to the local computer.
For example, an administrator might create a sharing-only account for a user who needs access to a shared printer or folder on the local computer. The user would not be able to log on to the computer, but could access the shared resource using the sharing-only account credentials.
For more such questions on personal computer visit:
brainly.com/question/13626205
#SPJ11