The following is part of a TCP header dump (contents) in hexadecimal format. E293 0017 00000001 00000000 5002 07FF... Answer the following in Decimal The source port number is The destination port number is The sequence number is The length of the header is The window size is
Answers
a. The source port number is 58,003.
b. The destination port number is 23.
c. The sequence number is 1.
d. The acknowledgment number is 0.
e. The length of the header is 20.
f. The type of the segment is 000010, SYN.
g. The window size is 2047.
The TCP header is divided into several fields, each of which contains different information about the transmission. To extract specific values from the TCP header dump in hexadecimal format, we need to first understand the structure of a TCP header. The source port number and destination port number are 16-bit fields that identify the port numbers on the sender's and receiver's sides, respectively. The sequence number and acknowledgment number are 32-bit fields that are used to number each byte of data that is transmitted and acknowledge the receipt of data, respectively.
The length of the header is a 4-bit field that specifies the length of the TCP header in 32-bit words. In this case, the length of the header is 20, which means that the length of the header is 20 x 32 bits = 640 bits. The type of the segment is a 6-bit field that identifies the type of data contained in the segment. In this case, the type of the segment is given as 000010, which is the binary representation of the SYN flag. The SYN flag is used in the TCP three-way handshake process to establish a connection between two hosts. Therefore, we can conclude that the TCP segment is a SYN segment.
To extract the values from the given TCP header dump, we need to convert the hexadecimal values to their decimal equivalents. For example, the source port number is given as E293 in hexadecimal format. To convert this to decimal, we can use the following formula:
Decimal value = (\(16^3\) * E) + (\(16^2\) * 2) + (16 * 9) + 3
= (4096 * 14) + (256 * 2) + (16 * 9) + 3
= 58,003
Therefore, the source port number is 58,003 in decimal format. Similarly, we can extract the destination port number, sequence number, acknowledgment number, and window size from the header dump.
a. The source port number, E293 = 58003.
b. The destination port number, 0017 = 23.
c. The sequence number, 00000001 = 1.
d. The acknowledgment number, 00000000 = 0.
e. The length of the header, 0x05 = 5, 5 x 4 = 20 bytes.
f. The type of the segment, 0x02 = 000010, SYN.
g. The window size, 07FF = 20477.
The question was Incomplete, Find the full content below :
The following is part of a TCP header dump (contents) in hexadecimal format.
E293 0017 00000001 00000000 5002 07FF...
a. What is the source port number?
b. What is the destination port number?
c. What is the sequence number?
d. What is the acknowledgment number?
e. What is the length of the header?
f. What is the type of the segment?
g. What is the window size?
Know more about TCP header here :
https://brainly.com/question/31081458
#SPJ11
Related Questions
If your domain name is practicelabs. Com, then what would be the zone file name?
Answers
The zone file name for the domain name practicelabscom would be "practicelabscomzone".
The zone file nameZone files are used to map domain names to IP addresses and other resources. The zone file name is typically the domain name followed by the word "zone". So in this case, the zone file name would be "practicelabscomzone".
It is important to note that the zone file name may also include the top-level domain (TLD), such as "com", "net", or "org". This is to ensure that the zone file is unique and does not conflict with other zone files for different TLDs.
Learn more about TLDs:
brainly.com/question/28299644
#SPJ11
Rafi is developing an application to send urgent information about global health crises over the Internet to hospitals. He is worried about packets getting lost along the way and the effect that will have on the accuracy of the information. What is his best option for dealing with lost packets
Answers
Answer:
Rafi can use the Transmission Control Protocol for communication since TCP has ways to recover when packets are lost.
Explanation:
TCP is a data transport protocol that works on top of IP and includes mechanisms to handle lost packets, such as the retransmission of lost packets.
migrating a traditional database design to the web can require design modification, additional software, and some added expense. t or f
Answers
A standard database architecture may need to be modified for the web, which might include purchasing new software and costing more money.
What purposes serve databases?database, often termed online version, any collection pf data, or content, that is particularly arranged for quick searches and retrievals by a robot. To make it simple to save, retrieve, update, and delete the file while performing various data-processing functions, databases are built.
What is a database, exactly?In computing, a database is an organized set of data that is accessible and stored electronically. Large databases are housed on data centers or cloud storage, whilst small data can be kept on a file system. .
To know more about Database visit :
https://brainly.com/question/13275751
#SPJ1
is a bi application that inputs data from one or more sources and applies reporting operations to that data to produce business intelligence. group of answer choices an olap application a trans enterprise application a classful application a reporting application a nosql application
Answers
A reporting application is a software application that receives data input from one or more sources and performs reporting operations on the data to provide business insight.
In data mining, what are OLTP and OLAP?Important DBMS phenomena include OLTP and OLAP. Each of them uses an online processing system. OLTP stands for online database editing, whereas OLAP stands for online analytical processing or online database query responding.
The definition of OLAP database designOnline Analytical Processing is the full name for this term. It is a system that interacts with users and offers them a variety of functions. Multi-dimensional data is a term used to describe data that can be modeled as dimension attributes and measure attributes.
To know more about reporting application visit :-
https://brainly.com/question/28545915
#SPJ4
to change the text wrap setting for clip art, click the _______ button.
Answers
To change the text wrap setting for clip art, click the "Wrap Text" button and select the desired option from the dropdown menu. This will allow you to adjust how the text flows around the clip art in your document. Please note that
To change the text wrap setting for clip art, click the "Wrap Text" button. Here's a step-by-step explanation:
1. Select the clip art image in your document.
2. Locate the "Wrap Text" button, usually found in the toolbar or under the Format or Layout tab, depending on the software you are using.
3. Click the "Wrap Text" button.
4. Choose the desired text wrap setting from the available options (e.g., inline, square, tight, top and bottom, etc.).
5. The text wrap setting will be applied to the clip art, allowing text to flow around the image according to your selection.
To know more about Wrap Text visit:-
https://brainly.com/question/31923423
#SPJ11
question 3 what is the term for programming code that is freely available and may be modified and shared by the people who use it?
Answers
The term for programming code that is freely available and may be modified and shared by the people who use it is "open source code." Open source code is code that is made available to the public, allowing anyone to use, modify, and distribute the code as they see fit. This is in contrast to proprietary code, which is owned and controlled by a specific company or individual, and is typically protected by copyright or other intellectual property laws.
Open source code is often developed collaboratively by a community of programmers, who contribute code improvements and bug fixes to a central repository. This approach allows for rapid development and iteration, as well as the creation of high-quality software that is accessible to a wider range of people. Additionally, open source code can be used in a variety of contexts, from personal projects to enterprise software, making it a versatile and powerful tool for software development.
To know more about programming code click this link -
brainly.com/question/30429605
#SPJ11
Complete the procedure for creating a contact group by selecting the correct term from each drop-down menu. 1. Click . 2. Enter a name. 3. Click Add Members and choose a source. 4. Select the member you want to add and click . 5. Repeat Step 4 as needed. 6. Click Save & Close.
Answers
Answer:
1: New Contact Group
2: Member
Explanation:
1. New Contact Group and 2: Member are correct term from each drop-down menu.
What is Contact group?A contact group is distinct from a Microsoft 365 group (formerly called a distribution list). An email message or meeting invitation can be sent to all recipients at once using a contact group, which is a collection of email addresses.
An email address suggestion appears when you enter a name. The group name is already in use and is marked as "not available," therefore you should try an alternative name. It should be noted that once a group name is selected, it cannot be modified.
Enter a description here if you'd want to clarify the goal of the group for others. When new members join, a description like this will be sent in the welcome email.
Therefore, The correct term from drop down menu are 1. New Contact Group and 2: Member are correct term from each drop-down menu.
To learn more about Drop down, refer to the link:
https://brainly.com/question/22696174
#SPJ2
What is a definition of a two-tier lan network design?
Answers
Which of the following are the three choices in the build-borrow-or-buy framework? (Check all that apply.)
internal development
acquisition of new resources
strategic alliances
Answers
The three choices in the build-borrow-or-buy framework are:Internal development: This refers to developing or building the required resources, capabilities, or solutions within the organization using its own internal workforce and expertise.
Acquisition of new resources: This involves acquiring or buying the necessary resources, capabilities, or solutions from external sources, such as other companies or vendors.Strategic alliances: This option involves forming partnerships or alliances with external entities, such as other companies or organizations, to access and share resources, capabilities, or solutions.internal development acquisition of new resources strategic alliances.
To know more about development click the link below:
brainly.com/question/31619654
#SPJ11
!! please help!!
What technique is used in this code to repeat the process for each value in the array?
a. pause blocks
b. a repeat loop
c. a for loop
d. an array block

Answers
Answer:
C: A for loop.
Explanation:
The for loop is used to repeat a section of code known number of times.
Which similar computer network components connect multiple devices?
A and are similar computer network components that connect multiple devices in a computer network. Please helppp
Answers
Answer: A network switch and/or a network hub its one of those two im not quite sure though
Explanation:
Explain What Peer to Peer Networking is.
Answers
Answer:
peer to peer networking is like when joining together works
the default comparison condition for the subtype discriminator attribute is the comparison. a.less than b.greater than c.equality d.nonequality
Answers
Additionally, disjoint subtypes are subtypes that contain unique subsets of the supertype entity set, not nonunique subsets. The other options mentioned in the query, such as less than, greater than, and nonequality, do not apply to the subtype discriminator attribute comparison.
It is important to note that the subtype discriminator can be null, and each supertype occurrence can be a member of at least one subtype. Overall, the subtype discriminator attribute is an essential feature that enables the entity supertype to inherit the attributes and relationships of the subtype. It allows for a more efficient and structured approach to database design, particularly when dealing with complex data models.
Find out more about disjoint subtypes
brainly.com/question/31102888
#SPJ4
Your data center features a retina scanner for added security. What type of area is this?
a.
OSHA
b.
SLA
c.
HVAC
d.
Biometric
Answers
The type of area that is featured with a retina scanner for added security in a data center is a Restricted Area. A restricted area refers to a physical space or geographical area that is considered highly confidential, and strict access control policies are put in place to ensure the security of the location.
These areas are normally found in sensitive places such as military installations, government buildings, research facilities, or data centers. In most cases, authorized personnel who work in a restricted area must undergo a security clearance to be granted permission to access the area.Restricted areas typically contain critical infrastructure, sensitive data, or classified information, hence requiring additional security measures to protect them from unauthorized access, tampering, or theft. The use of a retina scanner for added security is common in data centers to prevent unauthorized access to servers and other computing equipment in the facility.
Know more about retina scanner, here:
https://brainly.com/question/32402915
#SPJ11
A firm has prepared the following binary integer program to evaluate a number of potential locations for new warehouses. The firm's goal is to maximize the net present value of their decision while not spending more than their currently available capital.
Max 35x₁+25x₂+15x₃+15x₄
s.t. 4x₁+12x₂+6x₃+7x₄ ≤16 [Constraint 1)
x₁+x₂+x₃+x₄ ≥2 [Constraint 2]
x₁+x₂≤1 (Constraint 3 )
x₁+x₃≥1 (Constraint 4 )
x₂=x₄ (Constraint 5 )
xj={1, if location j is selected 0, otherwise
Solve this problem to optimality and answer the following questions.
Answer what will happen to each four locations:
a. Location 1
b. Location 2
c. Location 3
d. Location 4
Answers
The binary integer program provided aims to maximize the net present value of warehouse locations while considering capital constraints and various other constraints.
By solving the problem, we can determine the optimal solution and understand the impact on each location (1, 2, 3, and 4).
To provide a more detailed analysis, it is necessary to solve the program and evaluate the results. Unfortunately, the specific values and coefficients for the objective function and constraints are not provided in the query. Without this information, it is not possible to provide a specific answer regarding the impact on each location.
To determine the outcome for each location, the binary variables x₁, x₂, x₃, and x₄ need to be assigned values of 0 or 1 based on the optimal solution obtained from solving the binary integer program. The values of these variables will indicate whether each location is selected (assigned a value of 1) or not (assigned a value of 0), indicating their status and impact in the solution.
To obtain the optimal solution and assess the impact on each location, the provided binary integer program needs to be solved using appropriate optimization techniques and software. Once the solution is obtained, the values of the variables x₁, x₂, x₃, and x₄ can be analyzed to understand the outcomes for each location.
Learn more about binary integer programming here:
https://brainly.com/question/14697018
#SPJ11
Does somebody know how to this. This is what I got so far
import java.io.*;
import java.util.Scanner;
public class Lab33bst
{
public static void main (String args[]) throws IOException
{
Scanner input = new Scanner(System.in);
System.out.print("Enter the degree of the polynomial --> ");
int degree = input.nextInt();
System.out.println();
PolyNode p = null;
PolyNode temp = null;
PolyNode front = null;
System.out.print("Enter the coefficent x^" + degree + " if no term exist, enter 0 --> ");
int coefficent = input.nextInt();
front = new PolyNode(coefficent,degree,null);
temp = front;
int tempDegree = degree;
//System.out.println(front.getCoeff() + " " + front.getDegree());
for (int k = 1; k <= degree; k++)
{
tempDegree--;
System.out.print("Enter the coefficent x^" + tempDegree + " if no term exist, enter 0 --> ");
coefficent = input.nextInt();
p = new PolyNode(coefficent,tempDegree,null);
temp.setNext(p);
temp = p;
}
System.out.println();
p = front;
while (p != null)
{
System.out.println(p.getCoeff() + "^" + p.getDegree() + "+" );
p = p.getNext();
}
System.out.println();
}
}
class PolyNode
{
private int coeff; // coefficient of each term
private int degree; // degree of each term
private PolyNode next; // link to the next term node
public PolyNode (int c, int d, PolyNode initNext)
{
coeff = c;
degree = d;
next = initNext;
}
public int getCoeff()
{
return coeff;
}
public int getDegree()
{
return degree;
}
public PolyNode getNext()
{
return next;
}
public void setCoeff (int newCoeff)
{
coeff = newCoeff;
}
public void setDegree (int newDegree)
{
degree = newDegree;
}
public void setNext (PolyNode newNext)
{
next = newNext;
}
}
This is the instructions for the lab. Somebody please help. I need to complete this or I'm going fail the class please help me.
Write a program that will evaluate polynomial functions of the following type:
Y = a1Xn + a2Xn-1 + a3Xn-2 + . . . an-1X2 + anX1 + a0X0 where X, the coefficients ai, and n are to be given.
This program has to be written, such that each term of the polynomial is stored in a linked list node.
You are expected to create nodes for each polynomial term and store the term information. These nodes need to be linked to each previously created node. The result is that the linked list will access in a LIFO sequence. When you display the polynomial, it will be displayed in reverse order from the keyboard entry sequence.
Make the display follow mathematical conventions and do not display terms with zero coefficients, nor powers of 1 or 0. For example the polynomial Y = 1X^0 + 0X^1 + 0X^2 + 1X^3 is not concerned with normal mathematical appearance, don’t display it like that. It is shown again as it should appear. Y = 1 + X^3
Normal polynomials should work with real number coefficients. For the sake of this program, assume that you are strictly dealing with integers and that the result of the polynomial is an integer as well. You will be provided with a special PolyNode class. The PolyNode class is very similar to the ListNode class that you learned about in chapter 33 and in class. The ListNode class is more general and works with object data members. Such a class is very practical for many different situations. For this assignment, early in your linked list learning, a class has been created strictly for working with a linked list that will store the coefficient and the degree of each term in the polynomial.
class PolyNode
{
private int coeff; // coefficient of each term
private int degree; // degree of each term
private PolyNode next; // link to the next term node
public PolyNode (int c, int d, PolyNode initNext)
{
coeff = c;
degree = d;
next = initNext;
}
public int getCoeff()
{
return coeff;
}
public int getDegree()
{
return degree;
}
public PolyNode getNext()
{
return next;
}
public void setCoeff (int newCoeff)
{
coeff = newCoeff;
}
public void setDegree (int newDegree)
{
degree = newDegree;
}
public void setNext (PolyNode newNext)
{
next = newNext;
}
}
You are expected to add various methods that are not provided in the student version. The sample execution will indicate which methods you need to write. Everything could be finished in the main method of the program, but hopefully you realize by now that such an approach is rather poor program design.
Answers
I have a solution for you but Brainly doesn't let me paste code in here.
the speed of motion presented on-screen depends on
Answers
The speed of motion presented on-screen depends on the playback frame rate of the footage. The playback frame rate refers to the speed at which the video plays in frames per second (fps).
For instance, a video played at 24fps will play 24 frames in a second, whereas a video played at 60fps will play 60 frames per second. This means that the higher the playback frame rate of the video, the smoother and more fluid it appears.
On the other hand, a video with a lower playback frame rate may appear jittery or choppy.The frame rate of a video is determined by the recording device. Most digital cameras record video at a frame rate of 30fps or 60fps, while traditional film cameras use 24fps. It's worth noting that the frame rate of a video can be changed during post-production.
In conclusion, the speed of motion presented on-screen depends on the playback frame rate of the video. A higher playback frame rate results in smoother and more fluid motion, while a lower playback frame rate may result in jittery or choppy motion.
Know more about the digital cameras
https://brainly.com/question/11213213
#SPJ11
please help me find the highest Fibonacci number your machine can generate, using the sample fibo() function provided in c++. Also, please help me convert this fibo() function to Java and Python.
C++ sample codes:
#include
using namespace std;
long fib(int position)
{
if (position == 0)
return 0;
else if (position == 1)
return 1;
else
return fib(position-1) + fib(position-2);
}
// complexity = exponential, or 2^n,n =linear
int main()
{
int n;
for (n=0;n<50;n++)
cout << fib(n) << " ";
return 0;
}
Answers
The highest Fibonacci number a machine can generate using the sample `fibo()` function provided in C++ can vary depending on the architecture and available memory of the machine. However, in most machines, the highest Fibonacci number that can be generated using the `fibo()` function is 1836311903.
The function can be converted into Java and Python as follows:
Java:
```java
public static long fib(long n) {
if (n == 0)
return 0;
else if (n == 1)
return 1;
else
return fib(n-1) + fib(n-2);
}
```
Python:
```python
def fib(n):
if n == 0:
return 0
elif n == 1:
return 1
else:
return fib(n-1) + fib(n-2)
```
The highest Fibonacci number that can be generated using these functions in Java and Python is also dependent on the architecture and available memory of the machine.
However, it is typically the same as the C++ implementation, which is 1836311903. The function `fibo()` has an exponential complexity of O(2^n), which is not efficient for large values of n.
To know more abut highest visit;
brainly.com/question/29829770
#SPJ11
The half-life of a decaying radioactive isotope is the time it takes for half of the original mass of the isotope to decay. If the mass (in grams) of a particular radioactive sample is given by M(t)=30e^(-0. 05t) where t is in years, what is the half-life of that isotope?
Round your answer to 2 decimal places. Do not include units
Answers
Answer:
Explanation:
The half-life of 20F is 11.0 s. If a sample initially contains 5.00 g of 20F, how much 20F remains after 44.0 s?
Solution
If we compare the time that has passed to the isotope’s half-life, we note that 44.0 s is exactly 4 half-lives, so we can use Equation ???
with n=4
. Substituting and solving results in the following:
amountremaining=5.00g×(12)4=5.00g×116=0.313g
Less than one-third of a gram of 20F remains.
What security concept states a user should only be given the minimum set of permissions required to perform necessary tasks
Answers
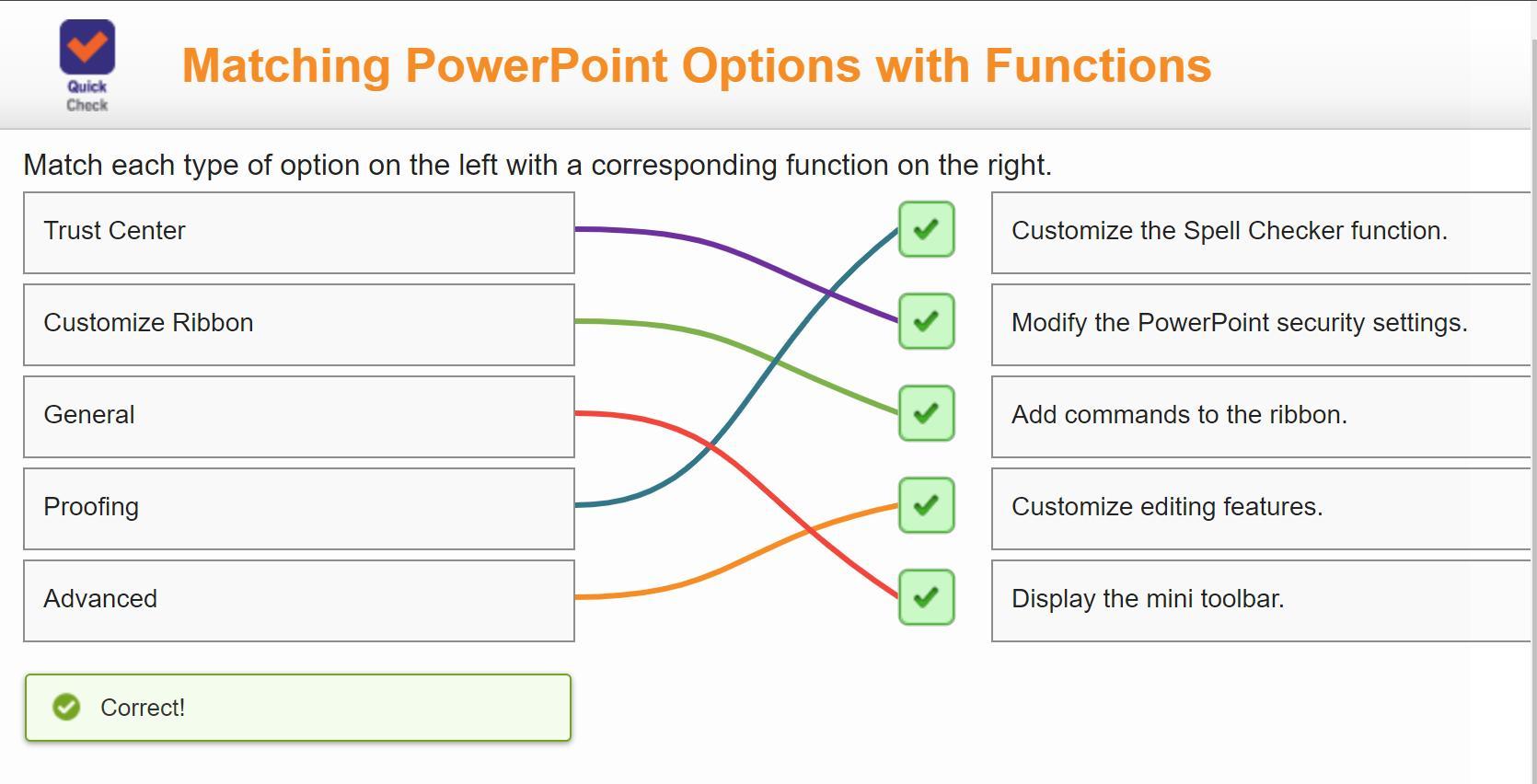
Match each type of option on the left with a corresponding function on the right.
Answers
Answer:
yes. the above is correct
Explanation: q posted
Answer: Anwer is correctly shown!!!!!!!!
Explanation:
HOPE IT HELPS Y'ALL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!

Create a paper of at least 1,800 words describing the situation you selected and explaining the logic that would support an array.
Answers
Answer:
I dont know about 1800 words but I sure can tell you abit about array
Explanation: Array in simple sense refers to a collection of similar data. It holds data which is homogeneous in nature, meaning they are all alike. The use of array provide a lot of advantages in the fields of computer programming. When you declare a variable for an array, you can store as much data as you wish in the same variable without having to declare many variables. A 2X2 dimensional array can also be used in programming which represents matrices as well. The search process in an array too is really convenient and time saving. Also in an array, accessing an element is very easy by using the index number.
what is an operating system that controls some aspects of the computer?
(not very well phrased, ik, it's coming from a crossword for one of my classes assigned as a snow day thing. looking for a seven letter word)
Answers
central processing unit (CPU), computer memory, file storage, input/output (I/O) devices, and network connections.
Answer: Windows
Explanation:
examples of operating systems include
windows
mac
linux
windows has seven letters
On October 1, 2021, Caitlin Fields launched a computer services company called Fields Initiatives, which provides consulting services, computer system installations, and custom program development. Fields adopts the calendar year for reporting purposes and expects to prepare the company's first set of financial statements on December 31,2021 . Using the following transactions, record joumal entries, create financial statements, and assess the impact of each transaction on the financial statements. October I c. Fields invested $108,690 cash, a $22,100 computer system, and $16,960 of office equipment in the company in exchange for common stock. October 2 The company paid $3,300 cash for four months' rent. (The company's policy is to record prepaid expenses in balance sheet accounts.) October 3 The company purchased $2,800 of computer supplies on credit from Sanchez office Products. october 5 the company paid $2,80θ cash for one year's premium on a property and liability insurance policy. (The company's policy is to record prepaid expenses in balance sheet accounts.) October 6 The company billed Fox Leasing $6,900 for services performed in installing a new web server. October 8 The company paid $2,86 a cash for the computer supplies purchased from Sanchez office. Products on October 3. October 10 The company hired Michelle Fields as a part-time assistant. october 12 The company billed Fox Leasing another $5,600 for services performed. October 15 The company received \$6,990 cash from. Fox Leasing as partial payment on its account. october 17 The company paid $1,86 cash to repair computer equipment that was damaged when moving it. october 20 The company paid $1,960 cash for advertisements published in the local newspaper. 0ctober 22 The company received $5,600 cash from Fox Leasing on its account. october 28 The company billed obL Company $5,400 for services performed. october 31 The company paid $1,460 cash for Michelle Fields's wages for seven days' work. October 31 The company paid a $8,960 cash dividend. November 1 the company paid $326 cash for mileage expenses. November 2 The company received $4,800 cash from Porter Corporation for computer services performed. November 5 The company purchased computer supplies for $2,160 cash from Sanchez office Products. November 8 The company billed Masters Company $2,290 for services performed. November 13 The company agreed to perform future services for Jones Engineering Company No work has yet been performed. November 18 The company received $3,206 cash from OBL Company as partial payment of the October 28 bill. November 22 The company paid $300 cash for miscellaneous expenses. Hint: Debit Miscellaneous Expense for $360. November 24 The company completed work for Jones Engineering Company and sent it a bill for \$6,6e0. November 25 The company sent another bill to obL Company for the past-due amount of $2,200. November 28 The company paid $384 cash for mileage expenses. November 39 The company paid $2,800 cash for Michelle fields's wages for 14 days' work. November 39 the company paid a $3,100 cash dividend. Using the dropdown buttons, select the financial statement elements and account titles to be included on the income statement. The account balances will automatically populate.
Answers
The income statement elements and account titles to be included on the income statement are:
Revenue: Service Revenue
Expenses: Rent Expense, Insurance Expense, Supplies Expense, Repair Expense, Advertisement Expense, Wage Expense, Miscellaneous Expense, Dividend Expense
To prepare the income statement, we need to consider the revenue and expenses incurred during the specified period. Based on the given transactions, the revenue account title to be included is "Service Revenue" as the company earned income from providing services to Fox Leasing, OBL Company, Porter Corporation, Masters Company, and Jones Engineering Company.
For expenses, we have several account titles to include:
Rent Expense: This represents the cost of renting the company's office space and is recorded when the company paid $3,300 cash for four months' rent.
Insurance Expense: This represents the cost of the property and liability insurance policy and is recorded when the company paid $2,800 cash for one year's premium.
Supplies Expense: This represents the cost of computer supplies and is recorded when the company paid $2,860 cash to Sanchez Office Products for the supplies purchased.
Repair Expense: This represents the cost of repairing damaged computer equipment and is recorded when the company paid $1,860 cash for the repairs.
Advertisement Expense: This represents the cost of advertising in the local newspaper and is recorded when the company paid $1,960 cash for the advertisements published.
Wage Expense: This represents the cost of wages paid to Michelle Fields and is recorded when the company paid $1,460 cash for her wages for seven days' work and $2,800 cash for her wages for 14 days' work.
Miscellaneous Expense: This represents various miscellaneous expenses and is recorded when the company paid $300 cash for miscellaneous expenses and $384 cash for mileage expenses.
Dividend Expense: This represents the payment of dividends to shareholders and is recorded when the company paid a $3,100 cash dividend and an $8,960 cash dividend.
Learn more about Insurance here:
https://brainly.com/question/989103
#SPJ11
how would a system administrator add an additional layer of login security to a user's aws management console?
Answers
To add an additional layer of login security to a user's AWS Management Console, enable multi-factor authentication.
An extensive array of service consoles for managing AWS resources are included in and referred to by the AWS Management Console, a web application.
You see the console home page when you first log in. You can access each service console from the home page, which also offers a single location to access the data you need to carry out tasks related to AWS. By adding, deleting, and rearrangeing widgets like Recently visited, AWS Health, Trusted Advisor, and others, you can further personalize the Console Home experience.
Additionally, there is an Android and iOS app for the AWS Management Console. This app offers mobile-optimized tasks that work well with the full web experience. For instance, managing your current Amazon EC2 environment is simple.
To know more about login security here
https://brainly.com/question/25720881
#SPJ4
Consider the following code segment.
ArrayList myList = new ArrayList();
for (int i = 0; i < 4; i++)
{
myList.add(i + 1);
}
for (int i = 0; i < 4; i++)
{
if (i % 2 == 0)
{
System.out.print(myList.get(i) + " ");
}
}
What output is produced as a result of executing the code segment?
Answers
The output produced by executing the code segment would be: 1 3.output is produced as a result of executing the code segment
This is because the code creates an ArrayList called "myList" and adds the integers 1, 2, 3, and 4 to it in a for loop. Then, another for loop is used to iterate through the ArrayList and print out the values at the even-numbered indices (0 and 2). This results in the output "1 3" being printed to the console.
To learn more about code click the link below:
brainly.com/question/29993929
#SPJ11
the manager of a digital forensics lab is responsible for which of the following? ensuring that staff members have enough training to do the job making necessary changes in lab procedures and software knowing the lab objectives all of the above
Answers
That staff members have received sufficient training to complete their duties, including understanding the lab's goals and making necessary software and procedure changes.
A manager of a digital forensics lab is responsible for which of the following?The primary responsibilities of the role holders will be to manage staffing and resources, monitor performance, increase efficiency, motivate staff, and oversee professional development. In order to incorporate laboratory policy documents and procedures into the quality management system, they will write them.
What is needed in a lab for digital forensics?A cyber-forensic lab needs the best software and hardware to function properly; In addition, we require devices that are forensically equipped for specialized digital forensics, data transmission facilities and accessories, and related services.
To know more about software visit :-
https://brainly.com/question/985406
#SPJ4
mike wants to stop vehicles from traveling toward the entrance of his building. what physical security control should be implemented?
Answers
Bollards are actual physical security measures that stop cars from approaching or slamming doors or other areas.
What is meant by Bollards?In addition to serving as security obstacles, bollards are also used to control traffic, issue warnings about impending threats, and improve the overall appearance of a building or site. To avoid collisions, bollards can be used to restrict access to sidewalks, bike lanes, and alleys.A bollard is a small post that is used to define a boundary for protection or architectural purposes.They direct traffic and designate limits when used mainly as a visual guide. They are available in a wide range of shapes and styles as architectural components to draw attention to or enhance their surroundings.Physical and visible barriers are created by security bollards. They come in a variety of forms, sizes, and patterns.To learn more about Bollards, refer to:
https://brainly.com/question/28435578
#SPJ4
HTML documents can only end with the following extensions: .html .htm
Answers
That is correct. In general, HTML documents should be saved with the file extension ".html" or ".htm" to be recognized as HTML documents by web browsers.
What is HTML?HTML stands for HyperText Markup Language. It is a markup language used for creating web pages and other information that can be displayed in a web browser. HTML provides a structure for web pages by using a combination of tags, attributes, and text to define the layout, content, and functionality of a web page.
HTML allows you to add headings, paragraphs, images, videos, links, forms, and other elements to a web page. The language uses tags to specify how content should be displayed on a page. For example, the <h1> tag is used to create a heading, the <p> tag is used to create a paragraph, and the <img> tag is used to display an image.
Web browsers interpret the HTML code and render it into a web page that users can view and interact with. HTML is often used in combination with other web technologies such as Cascading Style Sheets (CSS) and JavaScript to create dynamic and interactive web pages.
To know more about HTML ,visit:
https://brainly.com/question/30688099
#SPJ1
Which tab in the AutoCorrect dialog box enables you to specify that the corrections will automatically take place only when you attempt to change the respective errors in the document?
Answers
Answer:
the options tab
Explanation:
Answer:
options tab
Explanation:
plato