: Question 33 5 pts [4.b] Write the Python statements for each of the items 1-4 shown below. a 1. Import the math module 2. Assign a value of 4.5 to a variable named a 3. Assign a value of 4 to a variable named b 4. Convert the following math formula to a python statement using the variables above and the sqrt() and pow() functions. C = a3 + 2a + 62
Answers
Here are the Python statements for each of the items 1-4:
Import the math module:
python
Copy code
import math
Assign a value of 4.5 to a variable named a:
python
Copy code
a = 4.5
Assign a value of 4 to a variable named b:
python
Copy code
b = 4
Convert the following math formula to a Python statement using the variables above and the sqrt() and pow() functions. C = a^3 + 2a + 6^2:
python
Copy code
C = pow(a, 3) + 2 * a + pow(6, 2)
Note: The pow() function is used to raise a number to a given power, and the sqrt() function is used to calculate the square root of a number.
Learn more about Python from
https://brainly.com/question/26497128
#SPJ11
Related Questions
For questions 2-4, consider the following code:
if month == 7:
if day <= 15:
print("First half of the month")
else:
print("Second half of the month")
else:
print("Not in July")
What is the output if month = 7 and day = 14?
Group of answer choices
Nothing is output
Not in July
First half of the month
Second half of the month
Answers
Answer:
First half of the month
Explanation:
first if statement is true; nested if statement is true so the statement print("First half of the month") is executed
Kris is the project manager for a large software company. Which part of project management describes the overall project in detail? Analysis report Resources document Scope Scope creep
Answers
Answer:
The given option "Resource document" is the correct answer.
Explanation:
Whenever it applies to chronology as either the documentation a resource records collection of specific documents should indeed be regarded as a component of this kind of record. The resource component encompasses a series of proclamations provided by the researcher including its memorandum, and therefore is willing to take responsibility for each other by the very same body is nonetheless accountable again for the file.The remaining three options do not apply to something like the specified scenario. And the latter is the correct one.
Answer:
Resource document
Explanation:
Look at the color key below the map that shows the overall performance range. What is the range for 1 Year Performance? How does it compare to the 1 Day Performance range?
Answers
A performance range simply means the threshold and maximum percentage of shares that may become earned.
What is a performance range?Your information is incomplete. Therefore, an overview will be given. A performance range is the maximum percentage if shares that may become earned shares due to the attainment of the requirements of the performance.
It should be noted that in this case, the opportunity to incentivize performance will be associated with the relative performance.
Learn more about performance on:
https://brainly.com/question/26256535
What is a primary role of the physical layer in transmitting data on the network?.
Answers
Create the media signals that correspond to the bits in each frame. Explanation: The network media can be traversed by the bits that make up a frame thanks to the OSI physical layer.
What is the purpose of the OSI physical?Create the media signals that correspond to the bits in each frame. Explanation: The network media can be traversed by the bits that make up a frame thanks to the OSI physical layer.The copper wires, optical fiber, and wireless network devices are connected by the OSI Physical layer, which is responsible for encoding binary digits that represent Data Link layer frames into signals and transmitting and receiving those signals.The main goal of the physical layer is to specify the functional requirements for connections between end systems and the data-carrying electrical, optical, and radio signals. Other layers' responsibilities include media access, path selection, and dependability.To learn more about : OSI Physical layer
Ref : https://brainly.com/question/26500666
#SPJ4
Which of the following is an application layer protocol? Select all that apply A) POP3 B) ARP C) SMTP D) DNS E) IPv6 F) HTTP G) TCP H) Vale 1) DHCP
Answers
An application layer protocol is a communication protocol that is used for communication between software applications on different networked computer systems. The following are application layer protocols:SMTP, HTTP, DHCP, and POP3.
SMTP (Simple Mail Transfer Protocol) is an application layer protocol that is used for sending and receiving email messages. SMTP is used to send email messages from a client email application to a mail server or from one mail server to another.
HTTP (Hypertext Transfer Protocol) is an application layer protocol that is used for accessing the World Wide Web. HTTP is used for retrieving web pages from web servers and for transmitting data from web servers to web clients.
DHCP (Dynamic Host Configuration Protocol) is an application layer protocol that is used for automatically assigning IP addresses to network devices. DHCP is used to assign IP addresses to computers, printers, and other network devices.
Therefore, the application layer protocols among the given options are SMTP, HTTP, DHCP, and POP3.
To know more about protocol visit:
https://brainly.com/question/28782148
#SPJ11
A government authority or license excluding others from making, using, or
selling an invention without the creator's permission is called a
O A. patent
OB. Copyright
O c. trademark
OD. trade secret
Answers
Answer:
A. Patent
Explanation:
in this program, you will create functions that use lists to create, shuffle, and deal cards to a number up to 4 "hands". the standard deck of playing cards
Answers
In this program, you will create functions that use lists to manage a standard deck of playing cards. The first step involves generating the deck, which consists of 52 cards with 13 ranks (Ace to King) in each of the four suits (hearts, diamonds, clubs, and spades).
To shuffle the deck, you can use a randomization algorithm, such as the Fisher-Yates shuffle, to ensure that the cards are distributed randomly and fairly. Next, you will deal the cards to a specified number of "hands," up to a maximum of four.
To accomplish this, you will create a function that accepts the number of hands and the shuffled deck as its parameters. Then, the function will iterate through the deck, distributing the cards equally among the hands. Finally, each hand will be returned as a separate list, allowing the players to interact with their cards during gameplay. This approach ensures a clear and efficient way to manage a deck of playing cards using lists and functions.
Know more about Playing cards here;
https://brainly.com/question/11456986
#SPJ11
In Outlook 2016, what happens when users begin to type in the To field the name of an email recipient to whom they frequently send messages? The recipient’s full email address appears in the field. The recipient’s full contact information appears in a window. The address book appears and presents names to choose from. The address book appears and presents addresses to choose from.
Answers
Answer:
The recipent's full email address appears in the field.
Explanation:
Answer:
The recipent's full email address appears in the field.
Explanation:
EDGE 2023
What do you hope that people see in your digital footprint 5 years from now?
Answers
Answer:
I hope they see me playing with my dog (who died a few months ago) Malikeye
Explanation:
none :)
Which name is a default library name in Windows 7?
Answers
Answer:
In Windows 7, there are four default libraries: Documents, Music, Pictures, and Videos. All the default libraries include two standard folders: the user folder specific to each library and the public folder specific to it.
Explanation:
Using 2 bytes, how many different characters can Unicode represent?
A.
2^8
B.
2
C.
2^2
D.
2^16
E.
2^10
Answers
Answer:
The anwser is 2^16
Explanation:
How many modifier / mutator methods are there in class Check?
public class Check
{
private int one, two, total;
public void setNums(int n1, int n2)
{
one = n1;
two = n2;
}
public void add()
{
total = one + two;
}
public int getTotal()
{
return total;
}
}
ANSWERS:
0
4
3
1
2
Answers
There are two modifier/mutator methods in the class Check: setNums(int n1, int n2), and add (). One other accessor method is getTotal().
What does a mutator method's header look like?Before the method name in its header is the keyword void. A void method that modifies the values of instance variables or static variables is called a mutator method.
What actions constitute "mutators"?In computer science, a mutator method is a mechanism for controlling changes to a variable. They're also known as setter methods quite a bit. Frequently coming after a setter, a getter (also known as an accessor) returns the value of the private member variable.
To know more about methods visit:-
https://brainly.com/question/30026107
#SPJ1
List 10 different products made from timber
Answers
Answer:
Bath towels.
Toothpaste.
Nail polish.
Makeup.
Disinfecting wipes.
Medications.
Paints.
LCD screens.
Houses
Buildings
Explanation:
a sandbox of size 8 words is created starting at address 0011 last address of the sandbox is the bit string used to determine if an address lies outside of the sandbox is 00001100 0000---- ..
Answers
In computer programming, a sandbox is a restricted environment that allows developers to test their code without affecting the overall system.
In this particular scenario, a sandbox of size 8 words has been created starting at address 0011. This means that the sandbox occupies a total of 8 words in memory, with the first word being located at address 0011.
The last address of the sandbox is the bit string used to determine if an address lies outside of the sandbox. In this case, the bit string is 00001100 0000----. This means that any address that has the same bit string up to the 12th bit is considered to be within the sandbox, while any address that has a different bit string beyond the 12th bit is considered to be outside of the sandbox.
It is important to use a sandbox when testing code because it provides a controlled environment that limits the potential impact of errors or bugs. By restricting the code to a specific area of memory, developers can prevent unintended consequences from affecting the rest of the system. This can help to improve the overall stability and reliability of the software being developed.
Learn more about bit string here:
brainly.com/question/31602952
#SPJ11
2. Which pattern microphone should Jennifer take to the press conference? Jennifer is a journalist with one of the leading newspapers in LA. She has been assigned the coverage of a press conference for the launch of a latest phone. She placed her microphone right in front of the speaker. Her boss had asked her to take a ______ microphone.
Answers
Answer:
dynamic
Explanation:
The answer to this problem
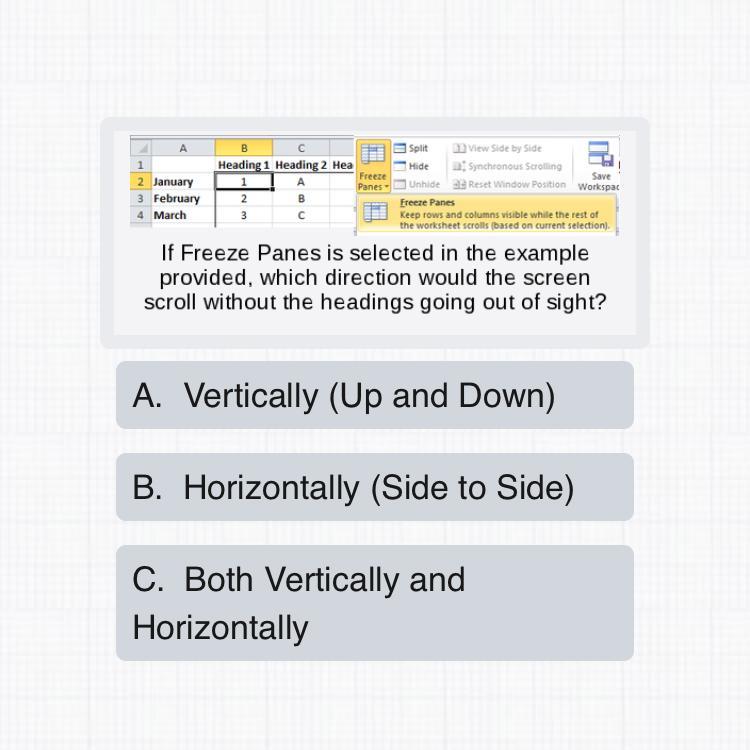
Answers
On which of the following computers should a Windows Defender Application Control default policy be created?
the referencecomputer
Answers
A Windows Defender Application Control default policy should be created on the reference computer.
Windows Defender Application Control (WDAC) is a security feature in Windows that helps protect against malicious software by restricting the types of applications that can run on a computer. A default policy is a set of rules that determine which applications are allowed to run on a system.
Creating a default policy on the reference computer is important because the reference computer serves as a baseline for other computers in the organization. By configuring WDAC on the reference computer, you establish a standard set of rules that can be applied to other computers, ensuring consistency and security across the network.
The reference computer is typically a clean and well-protected system that represents the desired security state for the organization. By creating the default policy on the reference computer, you capture the necessary rules and settings that align with the organization's security requirements. This policy can then be easily exported and deployed to other computers, reducing the time and effort required to configure WDAC individually on each machine.
Learn more about Windows Defender
brainly.com/question/29352945
#SPJ11
c# collection was modified after the enumerator was instantiated
Answers
This error occurs when you try to modify a collection (e.g., add or remove elements) while iterating through it using an enumerator. Enumerators do not support modifications to the collection during the enumeration process, as it may lead to unexpected results.
To fix this error, follow these steps:
1. Identify the collection and enumerator causing the issue in your code.
2. Instead of modifying the collection directly while iterating, create a temporary list to store the elements you want to add or remove.
3. After completing the iteration, apply the modifications from the temporary list to the original collection.
For example, if you have a list of integers and you want to remove all even numbers:
```csharp
List numbers = new List { 1, 2, 3, 4, 5, 6 };
List numbersToRemove = new List();
// Step 1: Identify the enumerator causing the issue
foreach (int number in numbers)
{
if (number % 2 == 0)
{
// Step 2: Add the even numbers to the temporary list
numbersToRemove.Add(number);
}
}
// Step 3: Apply the modifications from the temporary list to the original collection
foreach (int number in numbersToRemove)
{
numbers.Remove(number);
}
```
By following these steps, you can avoid the error "C# collection was modified after the enumerator was instantiated" and ensure that your code works as expected.
To know more about Enumerators visit:-
https://brainly.com/question/12905727
#SPJ11
Which of the following statements are true of software engineers? Check all of the boxes that apply. They are responsible for writing programming code. They are usually strong problem-solvers. They spend most of their work hours running experiments in a laboratory. They must hold advanced degrees in computer science.
Answers
Answer:
First two statements: yes. Last two: not so much.
But many of the better ones do have advanced degrees, but some don't.
The laboratory statement is silly; they sit behind a set of screens figuring out stuff and writing code.
It should be noted that statements are true about software engineers are;
They are responsible for writing programming code. They are usually strong problem-solvers.Software engineering can be regarded as branch of computer science which is responsible for the development as well as the building of computer softwares, these could be applications software or system software.
The engineers that carry out this process is referred to as software engineers and they are responsible for responsible for writing programming code.
We can conclude that software engineers are strong problem-solvers.
Learn more about software engineer at:https://brainly.com/question/25757629
Which technologies are used with ADSL? a. OFDM, TDD (time division duplexing) b. OFDM, M’ary modulation c. M’ary modulation, WDM d. WDM, WLL
Answers
OFDM, M'ary modulation technologies are used with ADSL.
ADSL (Asymmetric Digital Subscriber Line) is a technology used for transmitting digital data over existing telephone lines. It combines Orthogonal Frequency Division Multiplexing (OFDM), which is a modulation technique that divides the available bandwidth into multiple subcarriers, and M'ary modulation, which is a form of digital modulation that allows multiple bits to be transmitted simultaneously. This combination allows for efficient and high-speed data transmission over the existing telephone infrastructure. The other options mentioned (a. OFDM, TDD; c. M'ary modulation, WDM; d. WDM, WLL) are not typically associated with ADSL technology.
To know more about modulation technologies,
https://brainly.com/question/29601951
#SPJ11
What do you like most about coding in Phyton?
Answers
Which user has access to the voided deleted transactions tool?
a. Primary admin user
b. standard user
c. accountant admin user
d. company admin user
Answers
Answer: The answer is an Accountant admin user
Hope this helps
Answer:
Accountant admin user
Explanation:
I got it in the test
What two factors make up the skills of a good typist
Answers
Answer:
I feel to be a good typist one would have to have a good grasp of reading, grammar, and the ability to make errors to a lesser degree than more so. I can type, myself, 120-150 wpm with an error rate of 0-2. I also have the ability of not having to look at the keyboard as I type, and have a good eye on catching errors.
Explanation:
FILL IN THE BLANK. amazon bought the video game streaming service twitch for almost $1 billion because ______.
Answers
Amazon bought the video game streaming service Twitch for almost $1 billion because of the potential revenue and growth opportunities that the platform offered.
Twitch, which was founded in 2011, quickly became a popular platform for gamers to share their gameplay and interact with fans. The platform also offered opportunities for advertisers and sponsors to reach a highly engaged audience. Amazon recognized the potential for Twitch to become a major player in the streaming industry, as well as a valuable asset to their existing services.
With Amazon's resources and infrastructure, Twitch could further expand its reach and improve its user experience. Additionally, Amazon saw the opportunity to integrate Twitch with their own services such as Prime Video and Prime Gaming, offering more value to their customers. Furthermore, Amazon was also interested in Twitch's potential as a platform for life-streaming other events beyond gaming, such as concerts, sports, and news.
The acquisition allowed Amazon to diversify its offerings and increase its presence in the streaming market. Overall, Amazon's decision to acquire Twitch was based on the platform's potential for revenue growth, expansion, and integration with existing services.
know more about Amazon's resources here:
https://brainly.com/question/18003234
#SPJ11
what is i.a folder ii.file
Answers
Answer
Folder A digital folder has the same purpose as a physical folder – to store documents.
To identify the effect in a text, you can ask yourself which question?
A. What happened?
B. Why did this happen?
C. How did the person feel?
D. Where did this happen?
Answers
Answer:
why did this happen?
Explanation:
effect means what caused it so You should ask why did this happen or (what caused it)
Help please this is my last assignment of the year

Answers
Answer:
the answer is in the website that are there
list and explain three computing devices from the 20th century
Answers
Answer:
Calculating Machine
Graphic tablet.
Touchscreen
Explanation:
Hope this helps.
Brain-List?
Answer:
1. The First Calculating Machine (Pascaline)
2. Jacquard's Loom
3. The First Pocket Calculator
Explanation:
1. Pascaline was the first calculator or adding machine to be produced in any quantity and actually used. It was deigned at about 1642-1644.
2. Jacquard Loom is an attachment for powered fabric looms
3. The first truly pocket-sized electronic calculator was the Busicom LE-120A "HANDY" It was marketed in 1971.
to help ensure that an html document renders well in many different web browsers
Answers
Answer:
Doctype Declaration
Explanation:
In order to make sure that it renders correctly in a wide range of browsers, a Doctype Declaration needs to be added to the top of the HTML code. This declaration basically makes sure that the web browser knows how the code was written so that it can correctly read it. This is used because many web browsers use different default settings for reading code and can sometimes not display code that was not designed specifically for that web browser unless otherwise specified.
Answer:
I think it is:
B. a doctype declarationExplanation:
Before a URL is added to listOfPendingURLs, line 25 tests whether it has been traversed. Is it possible that listOfPendingURLs contains duplicate URLs? If so, give an example.
Answers
If the program adds each URL to listOfPendingURLs as it encounters them, then the list would contain duplicate entries for https://example.com/page1.
When the program attempts to process the duplicate URL, it would first check whether the URL has already been traversed by calling listOfProcessedURLs.contains(s). If the URL has been processed, the program would skip it and move on to the next URL. However, if the URL has not yet been processed, the program would add it to the list of pending URLs by calling listOfPendingURLs.add(s).Therefore, the program may encounter duplicate URLs in listOfPendingURLs, and it is important to handle these duplicates appropriately to avoid unnecessary processing or other issues.
To learn more about program click the link below:
brainly.com/question/13445413
#SPJ11