if you use the javac command to compile a program that contains raw type, what would the compiler do?
Answers
When using the 'javac' command to compile a program that contains a raw type codebase, the compiler generates a warning message to indicate the usage of raw types. However, it still compiles the program, allowing it to run.
The warning message serves as a reminder that raw types should be avoided and replaced with parameterized types for type safety and better code quality. It is highly recommended to address these warnings by providing type arguments to the generic types used in the program. Failure to do so may result in potential type-related errors and reduced type safety. Although the compiler allows the compilation of programs with raw types, it is important to understand and address the underlying issues to ensure a more robust and maintainable codebase.
Learn more about codebase here: brainly.com/question/28582526
#SPJ11
Related Questions
A technician is working on a PC that utilizes a RAID array for operation. The user of the system has reported that random files are becoming corrupted on creation with no pattern to the activity. One drive in the array is likely failing and causing the read/write failures. Which of the following Types of RAID is MOST likely in use?
A. RAID 0
B. RAID 1
C. RAID 5
D. RAID 10
Answers
Answer:
RAID 0
I hope this helps you :D
Your _______ can help block inappropriate content online.
1. web browser
2. Password
Answers
Answer:
web browser.
Explanation:
yea let me go post my password to block content (sarcasm)
Sarah just purchased the newest album by her favorite band. Her friend Molly loves their music as well, so Sarah offers to make a copy for her. Can she do this?
Answers
Answer:
Sarah can use a usb stick to copy the files, abd give Molly the usb stick so she can export the files. OR Sarah can upload the files to the cloud and give Molly permission to download the files from the cloud.
List at least two questions you can use to help decide whether a website's information is trustworthy
Answers
Answer:
Questions (three) that can be used to decide whether a website's information is trustworthy are;
1) Who is or are the authors of the website
2) What type of information the website conveys
3) Why was the information published on a website
Explanation:
1) Who is or are the authors of the contents of the website including the authors credentials so as to ascertain whether the author is qualified with regards to the topic or topics written about on the website
2) What are the information presented on the website and the context the in which the information are presented
Are the articles in the website backed by a source, with hyperlinks, references or footnotes
3) Why was the on the website information created. Is the information to entertain, persuade, sell or inform
universal containers (uc) has product options in a bundle that must be displayed in the quote line editor to the user. however, uc does not want these product options to display on the quote document that is generated and presented to the customer. how should the admin set up the bundle to meet these requirements?
Answers
On any product that is a Product Option for the bundles, select the Component checkbox is the right choice.
What do universal containers consist of?Universal Containers is a rapidly expanding international supplier of container products. They come up with various scenarios by getting users to think about things from a business perspective. They also provide guidelines for which industries or scenarios we will face and how to solve the problem. From small mail containers to custom equipment packaging and large cargo shipping containers, the company makes all kinds of containers. In addition, Universal Containers creates and maintains its own proprietary software to ease container design.
A strong, moulded glass bottle with a diameter of one ounce and a height of 31/4 inches by 11/8 inches is known as a universal container or screw-capped bottle. 28 milliliters) capacity, a wide mouth, and a flat base. After being sterilized with a loose cap, it is fastened.
To learn more about universal containers visit :
https://brainly.com/question/28156747
#SPJ4
the advancement in speed of transportation is attributed to invention of this device
Answers
Steve wants to publish a portfolio online. He use Mozilla Firebug. What will it help him do?

Answers
Mozilla Firebug is a web development tool used to inspect, edit, and debug HTML, CSS, and JavaScript in real-time. It is an extension of the Mozilla Firefox web browser and allows users to analyze and modify web page content on the fly.
For Steve, Firebug can be an extremely useful tool in creating and publishing his portfolio online. By using Firebug, he can inspect the HTML and CSS of his portfolio website to identify any errors, bugs, or issues that may be affecting its functionality or appearance. Additionally, he can edit the code directly within Firebug to test out new changes and see how they affect the website in real-time.
Overall, Firebug is a powerful tool for web developers like Steve who want to ensure that their website is functioning optimally and delivering the best possible user experience.
For more questions on HTML:
https://brainly.com/question/4056554
#SPJ11
Fill in the blanks to complete the “countdown” function. This function should begin at the “start” variable, which is an integer that is passed to the function, and count down to 0. Complete the code so that a function call like “countdown(2)” will return the numbers “2,1,0”.
Answers
Answer:
Check the code down below
Explanation:
You can use this code:
for i in range(5,-1,-1):
print(i)
This will print:
5
4
3
2
1
0
5 is changeable by the way!
The complete the “countdown” function. This function should begin at the “start” variable, which is an integer that is passed to the function, and count down to 0 is in the explanation part.
What is programming?The process of creating a set of instructions that tells a computer how to perform a task is known as programming.
Computer programming languages such as JavaScript, Python, and C++ can be used to create programs.
Here is the code to complete the “countdown” function:
def countdown(start):
for i in range(start, -1, -1):
print(i, end=",")
The countdown function takes an integer start as an argument and counts down from start to 0 using a for loop.
The range function is used to generate an integer sequence from start to 0, with a step size of -1. (i.e., counting backwards).
Thus, each integer in the sequence, separated by commas, is printed using the print function.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ2
Compare the performance of two cache designs for a byte-addressed memory system. The first cache
design is a direct-mapped cache (DM) with four blocks, each block holding one four-byte word. The
second cache has the same capacity and block size but is fully associative (FA) with a least-recently
used replacement policy
For the following sequences of memory read accesses to the cache, compare the relative performance of the
two caches. Assume that all blocks are invalid initially, and that each address sequence is repeated a large
number of times. Ignore compulsory misses when calculating miss rates. All addresses are given in decimal.
Fully associative: allow a given block to go in any cache entry
Compulsory miss: This occurs when a process starts, or restarts, or touches new data
Least-recently used: Choose the one unused for the longest time
i. (2 points) Memory Accesses: 0, 4, 0, 4, (repeats). The Miss Rate is:
DM Miss Rate FA Miss Rate
(a) 0% 0%
(b) 0% 100%
(c) 100% 0%
(d) 100% 50%
(e) 100% 100%
ii. (2 points) Memory Accesses: 0, 4, 8, 12, 16, 0, 4, 8, 12, 16, (repeats) The Miss Rate is:
DM Miss Rate FA Miss Rate
(a) 20% 0%
(b) 40% 0%
(c) 20% 20%
(d) 40% 100%
(e) 100% 100%
iii. (2 points) Memory Accesses: 0, 4, 8, 12, 16, 12, 8, 4, 0, 4, 8, 12, 16, 12, 8, 4, The Miss Rate is:
DM Miss Rate FA Miss Rate
(a) 25% 0%
(b) 25% 25%
(c) 50% 0%
(d) 50% 100%
(e) 100% 100%
Answers
i,The DM cache has a miss rate of 100%, while the FA cache has a miss rate of 50%. ii, The DM cache has a miss rate of 40%, while the FA cache has a miss rate of 0%. iii, The DM cache has a miss rate of 50%, while the FA cache has a miss rate of 100%.
Cache designs play an important role in the performance of a byte-addressed memory system. In this case, we are comparing the performance of a direct-mapped (DM) cache with a fully associative (FA) cache, both with the same capacity and block size. The main difference between the two designs is the way they handle memory accesses. The DM cache maps each memory block to a specific cache block, while the FA cache allows a given block to go in any cache entry.
For the given memory access sequences, the miss rates were calculated for both cache designs. In sequence i, the DM cache has a miss rate of 100%, while the FA cache has a miss rate of 50%. This is because the DM cache has a higher probability of having a conflict miss due to its mapping method, while the FA cache has more flexibility in its block placement.
In sequence ii, the DM cache has a miss rate of 40%, while the FA cache has a miss rate of 0%. This is because the DM cache has a limited number of blocks and can only store a subset of the accessed memory blocks, resulting in more misses. On the other hand, the FA cache can store any block in any cache entry, reducing the number of misses.
In sequence iii, the DM cache has a miss rate of 50%, while the FA cache has a miss rate of 100%. This is because the DM cache suffers from a high rate of conflict misses due to its fixed block mapping, while the FA cache has to use a least-recently used replacement policy, which can result in more misses.
In conclusion, the performance of a cache design is heavily dependent on the memory access patterns and the mapping strategy used. While the DM cache has a simpler mapping method, it can suffer from higher miss rates compared to the more flexible FA cache. However, the FA cache requires more hardware complexity and can suffer from higher miss rates due to its replacement policy.
To know more about Memory Accesses visit :
https://brainly.com/question/31163940
#SPJ11
sensory detection happens when our_______ detect and process sensory information from the environment.
Answers
Sensory detection happens when our "sensory receptors" detect and process sensory information from the environment.
Sensory detection refers to the initial stage of sensory processing, where sensory receptors in our body detect stimuli from the environment. These sensory receptors are specialized cells that are sensitive to specific types of sensory information, such as light, sound, touch, taste, and smell. They convert the physical energy of stimuli into electrical signals that can be processed by the nervous system.
Sensory receptors are located in various parts of the body, such as the eyes, ears, skin, taste buds, and olfactory receptors in the nose. They are responsible for detecting and transmitting sensory information to the brain for further processing and interpretation. Sensory detection plays a crucial role in our perception of the world around us and helps us make sense of our environment.
Learn more about world around here:
https://brainly.com/question/32236494
#SPJ11
I copied my friend's homework... give me some excuses to get out of it!!
Answers
Answer:
Tell the teacher that you will pee in her coffee cup if they don't forget about what you did
Explanation:
Answer:
Explanation:
Depends on the homework, but
"We worked together on it and came to similar conclusions."
"We checked answers with each other when we finished to make sure we got the problems correct and did the problems correctly."
13.
_______allows you to organize and summarize selected columns and rows of data
in a spreadsheet to obtain a desired report:
A.Pivot chart
B.Rotate table
C.Pivot date
D.Pivot table
Answers
Answer:
D. Pivot table
Explanation:
Microsoft Excel is a software application or program designed and developed by Microsoft Inc., for analyzing and visualizing spreadsheet documents.
A spreadsheet can be defined as a file or document which comprises of cells in a tabulated format (rows and columns) typically used for formatting, arranging, analyzing, storing, calculating and sorting data on computer systems.
Generally, it is extremely difficult and considered to be a herculean task to understand, analyze and summarize data when they are raw and unorganized.
In order to overcome this challenge or hurdle, Microsoft inc. designed and developed Pivot tables and charts to avail end users the ability to visualize, understand, analyze and summarize data in its raw form.
Hence, Pivot table allows you to organize and summarize selected columns and rows of data in a spreadsheet to obtain a desired report. It is an in-built feature of the Microsoft Excel software application or program.
you have been using snmp on your network for monitoring and management, but you're concerned about the security of this configuration. what should you do to increase security in this situation?
Answers
Increase security in this situation by doing the following: Change SNMP versions from version 1 and 2 to version 3, use SNMP to read-only, apply access control lists (ACLs) to your SNMP traffic, limit SNMP access to trusted devices, use firewalls to restrict SNMP traffic between devices and network segments, and use SNMPv3 security features such as user authentication and encryption.
SNMPv3 is used to improve SNMP security by providing user authentication and encryption. SNMPv3 uses a User-based Security Model (USM) that includes authentication and encryption mechanisms. SNMPv3 can use encryption and decryption keys that are exclusive to the user, as well as a time-based one-time password (OTP) that is generated by the USM itself. When sending SNMPv3 messages, users can authenticate and encrypt them using one of the following mechanisms: HMAC-MD5, HMAC-SHA-1, or CBC-DES.
Learn more about SNMP: https://brainly.com/question/27961167
#SPJ11
One way to initiate a file download from a web page is to
Select one:
a. click a hyperlink.
b. press Ctrl + D.
c. type download in the Address bar.
d. click the View Download button
Answers
Answer:
the answer is A
Explanation:
Some clues left on a drive that might indicate steganography include which of the following?
a. Graphics files with the same name but different file sizes
b. Multiple copies of a graphics file
c. Steganography programs in the suspect's All Programs list
D. All of the above
Answers
Some clues left on a drive that might indicate steganography include option D: All of the above.
a. Graphics files with the same name but different file sizes.
b. Multiple copies of a graphics file.
c. Steganography programs in the suspect's All Programs list.
What is steganography?Steganography is a technique for concealing sensitive information within a regular, non-sensitive file or message so as to avoid detection; the sensitive information is then extracted at its intended location. To further conceal or protect data, steganography can be used in conjunction with encryption.
Hence, Steganography is the practice of enclosing openly available information inside of something that seems normal. Steganography is a technique used by cybercriminals to conceal malicious code or stolen data in media like images and audio files.
Learn more about Steganography from
https://brainly.com/question/13089179
#SPJ1
How does a film establish the setting?
Answers
Answer:
Establishing Shots are critical in a film. They clue the viewer where this next scene is about to take place. Each time the location of a scene shifts, a new establishing shot does exactly; what its name implies: it establishes where the story will now continue, and fiction writers need to do the same thing.
Explanation:
As we learned in this lesson, a byte is about the same amount of memory as a character, such as the letter 't'. There are approximately 7 million characters in all of the Harry Potter novels combined. How many bytes of memory would all of the Harry Potter novels take up? How many copies of the Harry Potter novels would fit on a 7 Gigabyte flash drive. (Remember 1 Gigabyte is 1 billion bytes.)
Answers
Answer:
Give an example of a special purpose computer that you are familiar with and briefly describe its hardware and its software.
One example of a special purpose computer is a microwave because the programs on a microwave (like the "Popcorn" program) can't be changed. The hardware of a microwave include its buttons, the door, the light bulb, the transformer, the waveguide, the magnetron, and the control circuit. The software of a microwave is all of the programs that make the microwave run. These include the "Popcorn" program that is supposed to perfectly make your popcorn, the "Sensor" program that senses for a certain type of food/drink and adjusts the temperature accordingly, or a "Defrost" program which can be used to defrost meat.
2. Explain in your own words the difference between running your app by "Connecting to the Companion" and running your app by "Packaging" it.
When running the app by "Connecting to the Companion", the MIT companion app transfers the software (blocks) to the phone and then interprets them for the Android operating system. The Android OS takes the software and interprets it for the phone's processor so the app can run. Because of the way "Connecting to the Companion" works, the code can be re-interpreted every time a change is made. This process is known as interpretation because the code is constantly being re-interpreted.
When running the app by "Packaging" it, a program changes the software (blocks) on the computer into binary code and then packages it in an .apk file. Using a barcode scanner or another piece of software, the .apk file can be loaded onto the phone so the Android OS can interpret the code for the phone's processor. This process is called compilation since all of the source code is changed into binary.
3. As we learned in this lesson, a byte is about the same amount of memory as a character, such as the letter 't'. There are approximately 7 million characters in all of the Harry Potter novels combined. How many bytes of memory would all of the Harry Potter novels take up? How many copies of the Harry Potter novels would fit on a 7 Gigabyte flash drive. (Remember 1 Gigabyte is 1 billion bytes.)
The Harry Potter novels would take up approximately 7 million bytes. This means that 1,000 copies of the Harry Potter novels could fit on a 7 Gigabyte flash drive!
Carlos had 194 seeds and 11 flower pots he put the same number of seeds in each flower pot which is the best estimate for the number of seeds in each flower pot
Answers
Answer: in solution.
Explanation:
It is basically 194 divided by 11 since we are evenly grouping 194 seeds into 11 pots. This gives 17.636363…
This means that the best estimate is around that number.
.input devices are pieces of equipment that are used to put data into the computer true or false
Answers
Answer:
true
Explanation:
output devices do the opposite
Which jobs are most likely to be replaced by robots and what effect will this have
Answers
Answer:
Here we go. Generally the robots are designed in order to do the work which has very much risk and Humans find it too laborious or hard to do. The robots will be used for the army, or as laborers. In my country Nepal, there's a restaurant where robots are used as waiters. They take order from you and provide you the food. The robots can be used for various purposes but I don't think they will be appointed for the job of higher authority. The use of robots will have massive effect in human life. The use of robots and appointing them in various jobs will cause the problem of unemployment. The poor will be affected and their existence may get into problem. This is one effect but there can be many effects from the use of robots. Using robot in army can reduce human deaths but also people get unemployed. There is both advantage and disadvantage from their use.
Consider the following code segment: ArrayList list = new ArrayList(); list.add("One");
list.add("Two");
list.add("Three");
list.add("Four");
list.add("Five");
list.add("Six");
for (int i= 0; i < list.size(); i++)
{
list.remove(i);
}
System.out.println(list.toString()); What is printed when the code segment is executed?
[]
["Two", "Four]
["Two", "Four", "Six"]
["Four", "Five", "Six"]
["Six"]
Answers
["Two", "Four", "Six"]
The reason is that the for loop removes the elements from the list one by one, starting with index 0. On the first iteration of the loop, "One" is removed, causing all the elements to shift down by one index. On the second iteration, "Three" is removed, and so on. However, when the loop reaches index 3, "Four" is removed, causing "Five" to shift down to index 3, but the loop variable i is incremented to 4 on the next iteration. As a result, "Five" is not removed, and the loop terminates when i becomes equal to the size of the list. Therefore, after the loop has finished, the list contains the elements "Two", "Four", and "Six". This is confirmed by the output of the call to list.toString().
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
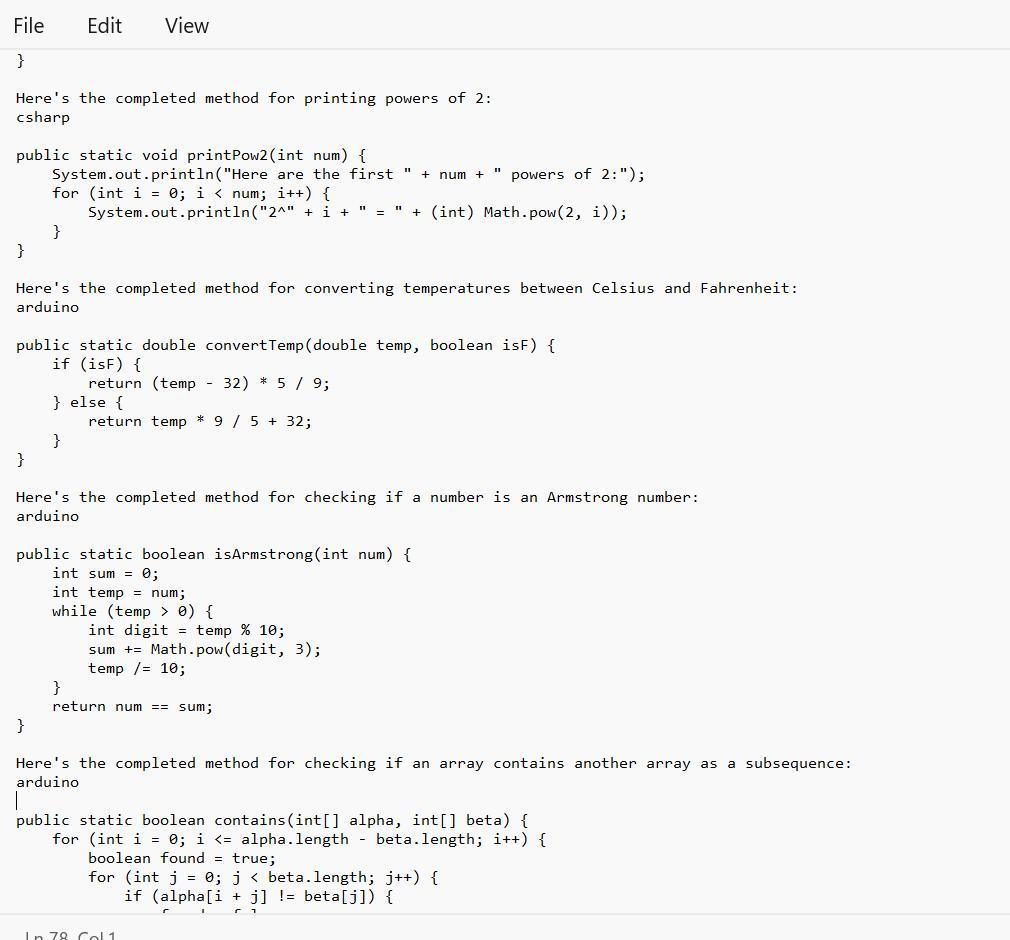
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


A programmer is developing software for a social media platform. The programmer is planning to use compression when users send attachments to other users. Which of the following is a true statement about the use of compression?
A. Lossy compression of an image file generally provides a greater reduction in transmission time than lossless compression does.
B. Lossless compression of an image file will generally result in a file that is equal in size to the original file.
C. Sound clips compressed with lossy compression for storage on the platform can be restored to their original quality when they are played.
D. Lossless compression of video files will generally save more space than lossy compression of video files.
Answers
A true statement about the use of compression is Lossy compression of an image file generally provides a greater reduction in transmission time than lossless compression does.
What is Compression?This refers to the process of modifying, encoding or converting the bits structure of data to use less space.
Hence, we can see that A true statement about the use of compression is Lossy compression of an image file generally provides a greater reduction in transmission time than lossless compression does.
Read more about data compression here:
https://brainly.com/question/17266589
#SPJ1
What is CPU
and it's functions
Answers
Answer:
CPU is considered as the brain of the computer. CPU performs all types of data processing operations. It stores data, intermediate results, and instructions (program). It controls the operation of all parts of the computer
Explanation:
hope it is helpful to you

the scan scheduling algorithm . a) services the request with the minimum seek time b) services the request next to the current head position in the direction of the head movement c) chooses to service the request furthest from the current head position d) services the request next to the current head position in the opposite direction of the head movement
Answers
The scan scheduling algorithm is services the request with the minimum seek time
What is meant by Scan scheduling algorithm ?A disc scheduling method called the scan responds to requests made by the memory management unit. An elevator algorithm is another name for it. This algorithm requires the read and write heads to travel in unison while completing all requests up until they reach the disk's edge.
Elevator algorithm is another name for the SCAN disc scheduling technique. This allows the head or pointer to move in either direction, with the disc arm moving from one end of the disc to the other and handling all requests along the way.
The Elevator Algorithm is another name for it. The disc arm in this method moves in a specific direction till the very end.
To learn more about Scan scheduling algorithm refer to :
https://brainly.com/question/13013797
#SPJ4
Besides a backup technician, who else would have encrypted backup passwords?
CEO
IT administrator
Data analyst
programmer
Answers
Answer:
CEO
Explanation:
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
Can someone tell me why I turn my mix on everyday and today I turned my computer on, put my headphones on and my mix started playing...
Answers
Answer:
LOL FELT THAT
Explanation:
Answer:
must have been a lucky day
Explanation
Imagine that you have just been given a super high-tech, life-sized robot that can communicate with you and accomplish tasks. Describe how this robot is a computer system using the five parts we discussed in the unit. Be sure to give specific examples.
Answers
Answer:
The robot has several inputs for speech recognition and sight like a microphone (as its ears) and cameras for sight. The robot has neural networks of programmed instructions in its processor which is used to process data received from the input devices and the result comes out as a response (like the robot speaking with a speaker as its mouth). This clearly defines the robot as a computer system.
Explanation:
A computer system is an electronic device that accepts input from a user or its surrounding, processes the data received and returns the output of the processed data.
The robot is able to receive data, process the data with its processor and responds or sends feedback to the user.
T/F: multithreading improves database searches because data is retrieved faster when the system has several threads of execution searching an array simultaneously, especially if each thread has its own cpu
Answers
False. Multithreading does not inherently improve database searches. While it is true that using multiple threads can potentially enhance performance in certain scenarios, such as parallelizing independent tasks,
It does not guarantee faster data retrieval in the context of database searches. Database searches primarily depend on the efficiency of the underlying database system, indexing strategies, query optimization, and disk I/O operations. Multithreading alone cannot compensate for suboptimal database design or slow disk access. Additionally, the effectiveness of multithreading for database searches depends on the nature of the workload and the database system's ability to handle concurrent queries. Therefore, multithreading may or may not improve database search performance, and other factors play a crucial role in determining the overall efficiency of the search process.
know more about Database :brainly.com/question/30163202
#SPJ11
T/F: multithreading improves database searches because data is retrieved faster when the system has several threads of execution searching an array simultaneously, especially if each thread has its own cpu.