Define input device
Answers
Answer:
An input device is computer hardware which is used to enter data for processing.
Related Questions
What does the following line of code do? Assume the user enters 2.3.
answerA = input("Enter a number. ")
It stores an int in the variable.
It stores a string in the variable.
It stores a float in the variable.
This line of code causes an error.
Answers
Answer:
It stores an int in the variable.
Explanation:
Answer:
It will store an int (Integer) into the variable.
Explanation:
Edg 2021
love me love me say that u love me fool me fool me go on and fool me : ) answer the question thx

Answers
Answer:
fido
Explanation:
i think sorry if wrong

Answer:
fidooo
Explanation:
he Get_Winnings(m, s) function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Answers
The function "Get_Winnings(m, s)" takes a string for the number of gold medals and an integer for the sponsored dollar amount, returning the money won as an integer or "Invalid" if the amount is invalid.
The function "Get_Winnings(m, s)" takes two parameters: a string "m" representing the number of gold medals and an integer "s" representing the sponsored dollar amount. Here's a step-by-step explanation of the function.
Check if the input values are valid. If the "m" parameter is not a string or the "s" parameter is not an integer, return the string "Invalid".Convert the string "m" to an integer to calculate the total winnings based on the number of gold medals won.Calculate the money won by multiplying the number of gold medals with the sponsored dollar amount.Return the calculated winnings as an integer.If the input values are not valid or cannot be converted, the function will return the string "Invalid" to indicate an invalid amount. Otherwise, it will return the calculated money won as an integer.
For more such question on Integer
https://brainly.com/question/30030325
#SPJ8
Question 1
1 pts
(02.01 MC)
Jackie used the software development life cycle to create a new game. Jackie ran her code to make sure it
worked and had no errors.
Which stage of the software development life cycle is Jackie currently in?
o Coding
O Maintenance
O Planning & Analysis
Testing
Answers
Answer:
she is running a maintenance to make sure everything works
Explain how the ASCII and decimal versions are abstractions of the binary digits.
Answers
Answer:
A later version of ASCII called extended ASCII uses 8 digits long binary string giving it the ability to represent 256 different characters. ASCII includes, primarily, two types of characters, which are control characters (represented by 0-31 decimal and 127 decimal) and printable characters (represented by 32- 126 decimal).
Explanation:
If the value is set to equals to current entry then
a) the argument remains unchanged
b) the argument always changed
c) the argument will be deleted
d) the argument can be ignored
I will definitely mark you Brainliest for answering the correct answer!
Answers
Answer:
this is a fallacy
a is the answer
How can I incorporate a for loop with a list?

Answers
Answer:
You can call each element in a for loop using: for element in [list name]: ...
Explanation:
for element in vowels:
Hint = Hint.replace(element, "*")
Keep in mind, this is only for the part where you modify Hint with Hint.replace().
Difference between misinformation and disinformation.
Answers
Why computer is known as versatile and diligent device . Explain
Answers
A computer is known as a versatile machine because it has to perform specific functions without misleading or lagging its actual speed and accuracy for a long time.
What are the functions of the computer?A computer plays a series of functions in your daily life. It includes arithmetic and logic calculations, transferring data among devices, and easy human works of input, processing, and output. It also regulates the huge collection of data by storing them.
A computer is also known as a diligent device because it can be significantly utilized for all sorts of functions in your day-to-day life. Computers can also do numerous functions in different ways without affecting their integrity.
Therefore, the computer is known as a versatile and diligent device.
To learn more about Computers functions, refer to the link:
https://brainly.com/question/20476366
#SPJ9
the main work area of the computer is the
Answers
Answer:
Desktop
Explanation:
The desktop is the main work area of your computer, and will likely be the most visited area of your computer. Your desktop appears every time you log into your account, and contains icons and shortcuts to your most used programs and files.
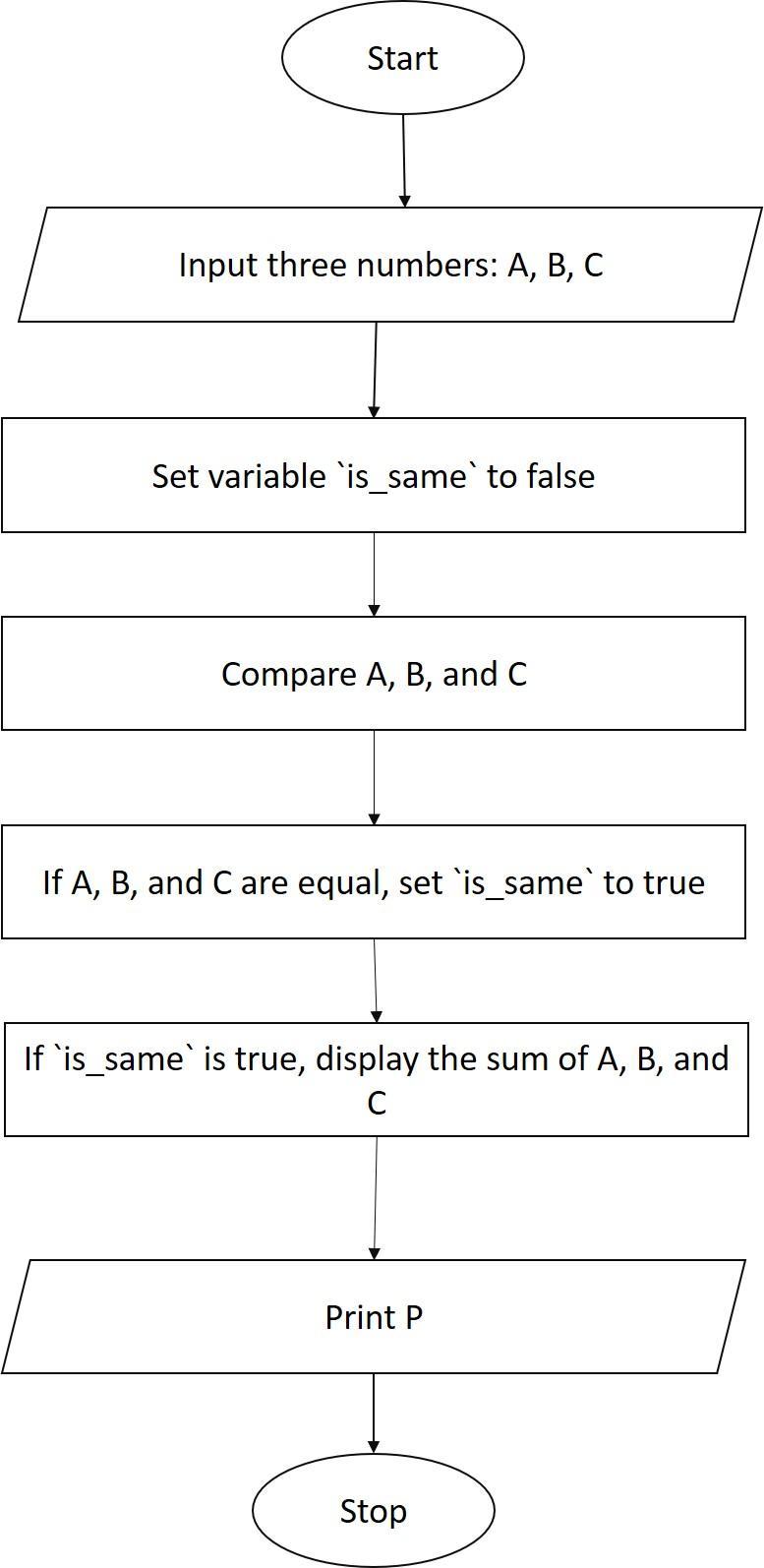
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
Should the government encourage people to own their own homes, even if they have to go into debt to do that?
Answers
Answer:
Yes yes yes yes yes yes yes yes yes tes
Discuss the Autonomous Robots and Additive Manufacturing contribution to Smart Systems. Why are these two technologies are important for the Smart Systems? Explain the technologies with an example.
Answers
Additive manufacturing, also known as 3D printing, revolutionizes traditional manufacturing methods by constructing objects layer by layer. It enables rapid prototyping, customization, and on-demand production. For instance, in a smart healthcare system, additive manufacturing can be employed to produce personalized medical implants, such as customized prosthetics or dental implants, based on patient-specific requirements, resulting in improved patient outcomes and reduced lead times. Both technologies contribute to the advancement of Smart Systems by optimizing processes, enhancing productivity, and enabling customization in various industries.
Select the correct teamwork characteristic from the drop-down menu.
A characteristic that denotes integrity and truthfulness, along with the absence of lying, cheating,
or theft
An act of working together for a common purpose or benefit
A characteristic of being able to complete a required task at a previously designated time
You can demonstrate cooperation by
.
Answers
A characteristic that denotes integrity and truthfulness, along with the absence of lying, cheating, or theft is honesty.
What is honesty?The term honesty is known to be a word that connote honor, integrity, probity and also a sense of uprightness in regards to character or action.
Note that the characteristic is one that shows or denotes positive, virtuous attributes e.g. integrity, truthfulness, and straightforwardness and it is one that is made up of the absence of lying, cheating, or any form of theft.
Hence, A characteristic that denotes integrity and truthfulness, along with the absence of lying, cheating, or theft is honesty.
Learn more about integrity from
https://brainly.com/question/14342720
#SPJ1
code the function, reversetop, which is passed a list and returns a reversed list of the high-level entries. do not use the built-in reverse function
Answers
Let's reverse the list without using reverse function.
\(\tt def reversetop():\)
\(\qquad\tt global\:L\)
\(\qquad\tt L2=L[::-1]\)
\(\qquad\tt return\:L2\)
\(\tt L=eval(input("Enter\:a\:list"))\)
\(\tt print("reversed\:list=", reversetop())\)
Write a python code using tracy turtle to draw the following shape

Answers
Answer:
import turtle
t = turtle.Turtle()
R = 20
N = 8
def rect(x,y,w):
t.penup()
t.setpos(x,y)
t.pendown()
for _ in range(4):
t.left(90)
t.forward(w)
rect(0,0,R*N)
rect(R*N,0,R*N)
rect(0,-R*N,R*N)
rect(R*N,-R*N,R*N)
for x in range(1,N+1):
t.penup()
t.setpos(0,-R*x)
t.pendown()
t.circle(R*x)
Explanation:
Not a turtle expert, but this seems to do the job.
To improve readability, what color background should I use
with dark purple text.
Answers
Answer:
umm probably white or any light color
Explanation:
cuz if you put similar colors whether color or the darkness it will be hard to read cuz its similar. ofc if you do a dark color for text you can use a much lighter shade of that color
Which of the following are exclusively associated with copyright protection? (Select three.)
Right to reproduce small excerpts of a work
Right to apply for a patent
Right for anyone to display a work
Right to lend a work
Right to use a trademark
Right to make derivatives of a work
Right to reproduce a work
Answers
Answer:
Right to make derivatives of a work.
Right to reproduce a work.
Right to lend a work.
Explanation:
Just took the quiz on testout.
The rights which are exclusively associated with copyright protection are:
F. Right to make derivatives of a work. G. Right to reproduce a work. D. Right to lend a work.Copyright protection has to do with an intellectual property law which makes it illegal for a person to copy the work of another, without approval, or adequate reference
As a result of this, we can see that the rights which are exclusively associated with copyright protection are the rights to make derivatives of a work, reproduce a work and to lend a work because they are the intellectual property of the author.
Therefore, the correct answers are options F, G, and D
Read more here:
https://brainly.com/question/23385572
All of the following are good ways to reduce distractions when studying except.
A) Turning off the tv
B) sitting in a quiet place
C) sitting away form the window
Last by not least
D) Listening to music
Answers
Answer:
D
Explanation:
Music puts us in a better mood, which makes us better at studying, but it also distracts us, which makes us worse at studying.
Explanation: some types of music are very distracting
state 5 different between mouse and keyboard
Answers
Answer:
*here you go *
Explanation:
While the main purpose of a mouse is to guide the cursor on the computer monitor, a keyboard is a typewriter like device with some additional functions that allow human interaction with computer. ... While mouse is considered to be a pointing device, keyboard is the input device for a computer.
(Keyboard vs Mouse
Keyboard and mouse are integral parts of a computer system and one cannot even think of interacting with the computer or monitor with the use of these two devices. In a sense, these two devices are the user interface that allows working on a computer system, and without them it is not possible to do anything on a computer. While the main purpose of a mouse is to guide the cursor on the computer monitor, a keyboard is a typewriter like device with some additional functions that allow human interaction with computer. In fact, a keyboard is the only source of providing the input to the computer and it performs the functions we ask it only with the help of this device.
While mouse is considered to be a pointing device, keyboard is the input device for a computer. Despite touch screen having been developed that allows one to use virtual keyboard onscreen, physical keyboard remains first choice of most of the individuals. There are keys with symbols printed on them in a keyboard and with the lightest of touches; the numeral or alphabet gets written on the screen of the monitor using a keyboard. There are some instructions for which one has to press a key and holding it pressed, another key has to be pressed. There are many shortcuts also used with the help of a keyboard that help save time and effort. Many computer commands are the results of these shortcuts. The major function of a keyboard is when one is using a word processor or a text editor.
A mouse is a pointing device and consists of a right and left clicks with a wheel in between that allows on to scroll up and down on a web page. The major function of a mouse is to control the cursor on the monitor of the screen. Today there are wireless mouse available that work through infrared rays.)
A measuring cylinder is used to measure the volume of an irregular
solid object.
Answers
Answer:
Yes it is used for measuring the volume of irregular solid objects for example a peice of stone, rubber etc.
Explanation:
antivirus programs are an example of which type of software
Answers
Antivirus programs are an example of security software.
Antivirus programs are a kind of software that aims to safeguard a computer against malware. This software is used to detect, prevent, and eliminate malware from a computer. Antivirus programs are used to protect computers from worms, viruses, Trojan horses, adware, spyware, and other malware. Antivirus programs are critical for maintaining a computer's security and privacy. They also safeguard data stored on a computer, preventing it from being compromised.
Antivirus programs are a critical type of security software that are used to protect computers from a wide range of malware. These programs can detect, prevent, and eliminate malware from a computer, making them an essential tool for maintaining a computer's security and privacy. With the help of antivirus programs, computers can be protected from a wide range of threats, which is critical for ensuring that data stored on the computer remains secure.
To know more about programs visit,
https://brainly.com/question/28224061
#SPJ11
Replace the nulls values of the column salary with the mean salary.
Answers
When data is combined across lengthy time periods from various sources to address real-world issues, missing values are frequently present, and accurate machine learning modeling necessitates careful treatment of missing data.
What is Column salary?
One tactic is to impute the missing data. A wide range of algorithms, including simple interpolation (mean, median, mode), matrix factorization techniques like SVD, statistical models like Kalman filters, and deep learning techniques.
Machine learning models can learn from partial data with the aid of approaches like replacement or imputation for missing values. Mean, median, and mode are the three basic missing value imputation strategies.
The median is the middle number in a set of numbers sorted by size, the mode is the most prevalent numerical value for, and the mean is the average of all the values in a set.
Thus, When data is combined across lengthy time periods from various sources to address real-world issues, missing values are frequently present, and accurate machine learning modeling necessitates careful treatment of missing data.
Learn more about Data, refer to the link:
https://brainly.com/question/10980404
#SPJ4
Which of these are examples of centralized management? check all that apply.
a. Role-based access control
b. Centralized configuration management
c. Copying configurations to various systems
d. Local aunthentication
Answers
Role-based access control and Centralized configuration management are examples of centralized management.
What is meant by role-based access control?RBAC, commonly referred to as role-based security, is an access control technique that grants end users access depending on their roles inside your business. Role-based access control offers fine-grained control and is less error-prone than manually granting rights. It also offers a straightforward, controlled method to access management.
The ability to set access privileges at several levels, such as the DNS server, DNS zone, and DNS resource record levels, is provided by role-based access control.
To know more about role-based access control, check out:
https://brainly.com/question/27961288
#SPJ1
Count how many words in a list have length 5. modified as follows. Instead of counting the
number of words of length 5, finish the function count_words(a_list, a_length) so it builds and returns a list of all the
words in a_list that have a length equal to the passed argument a_length. Copy your build_list function from the previous
problem into this problem's code, then complete the main() method so it calls build_list() to build and return a list of strings
the_list, then read an int the_length from the user, and finally call count_words(the_list, the_length) and
print out the returned list.
Answers
Here's the code that fulfills the given requirements:
The Codedef build_list():
word_list = []
while True:
word = input("Enter a word (or just press Enter to stop): ")
if word == "":
break
word_list.append(word)
return word_list
def count_words(a_list, a_length):
return [word for word in a_list if len(word) == a_length]
def main():
the_list = build_list()
the_length = int(input("Enter a word length: "))
result = count_words(the_list, the_length)
print(result)
if __name__ == '__main__':
main()
Here's how the code works:
The build_list() function asks the user to enter words until they press Enter without typing anything. It then returns a list of the entered words.
The count_words(a_list, a_length) function takes two arguments: a_list is the list of words to search, and a_length is the length of the words to search for. It then returns a list of words from a_list that have a length of a_length.
The main() function calls build_list() to get a list of words from the user, then asks the user for a word length to search for. It then calls count_words(the_list, the_length) to get a list of words of the desired length, and finally prints out the resulting list.
You can run the code and test it out yourself to see how it works.
Read more about python here:
https://brainly.com/question/28675211
#SPJ1
A SaaS provider such as Oracle or SAP manages service levels and availability . This is advantageous because _____.
Answers
A SaaS provider managing service levels and availability is advantageous because it relieves the burden of managing and maintaining the underlying infrastructure and software from the end-user.
What is Oracle?Oracle is a multinational computer technology corporation that specializes in developing and marketing database software, cloud engineered systems, and enterprise software products. It is best known for its flagship product, the Oracle Database, which is widely used in many large corporations and organizations. Oracle also provides other software and services, including cloud-based infrastructure and platform services, enterprise resource planning (ERP) software, customer relationship management (CRM) software, and more.
Here,
This means that the end-user can focus on using the software to run their business rather than worrying about the technical aspects of the software. Additionally, SaaS providers often have more resources and expertise in managing infrastructure and software, which can lead to better service levels and availability compared to what the end-user could achieve on their own.
To know more about Oracle,
https://brainly.com/question/26420772
#SPJ4
A Microsoft Excel spreadsheet is laid out in a grid of columns and rows. The columns are labeled with letters: A,B,C… while rows are labeled with numbers: 1,2,3… and so on. A cell is where a column and row intersect. For example, where column B intersects with row 4 , the cell is labeled B4. You can think of a cell as an address on a map. The data has been collected in the Microsoft Excel Online file below. Open the spreadsheet and perform the required analysis to answer the questions below. Relative Cell References One of the most powerful features in Excel is the ability to place a formula in one cell and then drag the contents of that cell down or across to repeat that same formula on other values. For example, let's say you have this following simple layout in Excel: We can tell from this table that there are 8 orders for the MP3 album and that value is in cell C2. Next, we would like to calculate the Total Cost for all MP3 orders. To do that we would multiply the Order Quantity by the Unit Cost; 8∗ 11.99. That can be done in cell E2. Finally, we can select cell E2, grab the drag handle, and then drag down to E4 to obtain the other two Total Cost values. This technique uses relative cell references, meaning the values can change as you drag downward. In the given spreadsheet, three investments are listed in rows 4-6. Column B contains the expected growth rate for each investment as a percentage. Calculate the expected value of Investment A in cell D4 by multiplying its value in Year 0 by the quantity ( 1+ Growth rate). Then drag cell D4 down to D6 to get the other two investment values after one year given different growth rates and place those values below: Investment A: \$ (to the nearest dollar) Investment B: \$ (to the nearest dollar) Investment C:$ (to the nearest dollar) Absolute Cell References By placing a dollar sign (\$) in front of the row and/or column of a cell you can "lock down" either the row, column, or both so no change occurs when you drag to fill other cells. In row 13 , we would like to calculate the value of Investment A over a period of ten years assuming the constant growth rate in cell B13. First, calculate the value in Year 1 (D13) using the same technique in Part A. If you try to drag D13 to the right to fill in the remaining years, you will get some very strange numbers! That is because the growth rate cell B13 is changing as you drag. However, you need that cell to say fixed in place for all the formulas as you drag to fill E13 through M13. The way to fix cell B13 in place is using an absolute cell reference. Instead of B13 in the formula change it to $B$13 and then drag to the right to fill Year 2 through Year 10. Enter those values below (to the nearest dollar). Do not use a dollar sign (\$), just the value. Fixed Column / Relative Row Cell References Now you would like to track the value of all three investments over the same 10-year period in rows 22, 23, and 24. Start by creating a formula in D22 that is like the formula in D13. However, there is one change to make. Knowing that you will want to drag the entire 10-year span in row 22 down to rows 23 and 24 , the row reference in the (1+ growth rate) calculation must be able to change as you drag. That is done by removing the dollar sign (\$) in front of the row number in the growth calculation. Make sure that is done in cell D22, then drag across to M22 to obtain the values for Investment A. Finally, select all cells from D22 to M22, and then drag down to fill the next two rows. Now you have the values for Investment B and Investment C. Notice the format of the formulas in cells D22:M24. What is the value of each investment in year 10? Investment A:$ (to the nearest dollar) Investment B:$ (to the nearest dollar) Investment C:$ (to the nearest dollar) "Start in column D, then move across, and multiply the preceding value by its growth rate in cell $B22 (Which is 1 plus the percentage expected growth) to get the cL "By changing the growth rate cell from $B$22, etc. to $B22, the row of the growth rate is allowed to change yet remain in column B while filling down to the other two to change yet remain in column B while filling down to the other two Investments."
Answers
The given task involves performing calculations and data analysis in a Microsoft Excel spreadsheet. It demonstrates the use of relative and absolute cell references to efficiently perform calculations and drag formulas across different cells.
The task includes calculating the expected value of investments over a period of one year and ten years, considering growth rates. The results are obtained by dragging formulas across rows and columns while appropriately fixing or changing cell references. The final step involves determining the value of each investment in year 10 by following the provided formula pattern.
In the provided Excel spreadsheet, various calculations are performed using relative and absolute cell references. In the first part, the expected value of Investment A is calculated for one year by multiplying its initial value with the growth rate. The formula is then dragged down to calculate the values for Investments B and C. The next step involves calculating the value of Investment A over ten years by using an absolute cell reference for the growth rate. The formula is filled across the years by dragging, ensuring that the growth rate remains fixed. Similarly, the values for Investments B and C are calculated by using relative row references to allow for changes while dragging.
Finally, the values of each investment in year 10 are obtained by following the provided formula pattern. By employing relative, absolute, and mixed cell references, the calculations are performed accurately and efficiently in the Excel spreadsheet.
Learn more about Excel here: https://brainly.com/question/29786912
#SPJ11
difference between nintendo switch and switch lite
Answers
Answer:
thank you sa point labyu stay safe
Answer: The switch lite is the one you can't dock onto your tv and is mostly used for handheld purposes, also you can't take off the controllers.
Explanation:
Create a flowchart that if followed will sing your favourite song
Answers
Start by taking a deep breath and getting into the rhythm of the song.
Begin with the first verse, which starts with the lyrics "The club isn't the best place to find a lover."
Sing the chorus, which goes "I'm in love with the shape of you, we push and pull like a magnet do."
Move on to the second verse, which begins with "I'm in love with your body."
Sing the chorus again.
Next is the bridge, which starts with "One week in we let the story begin."
Sing the chorus one more time.
End the song with the final verse, which begins with "Come on be my baby, come on."
Finish with the chorus one last time and let the final notes trail off.
Congratulations! You've successfully sung "Shape of You" by Ed Sheeran!
Text-based flowchart that will help you sing Ed Sheeran's song "Shape of You".
What is Flowchart?Take a few deep breaths and start moving to the music. Start with the opening line of the first stanza, "The club isn't the best place to find a lover."
The chorus is, "I'm in love with the shape of you, we push and pull like a magnet do." Sing it. Next, read the second verse, which starts with the phrase.
The bridge follows, and it opens with the phrase "One week in we let the story begin." Repeat the chorus in your singing. Start the song's final verse, "Come on be," to close it.
Therefore, Text-based flowchart that will help you sing Ed Sheeran's song "Shape of You.
To learn more about Flowchart, refer to the link:
https://brainly.com/question/29833160
#SPJ2
Multiple TCP streams can distinguished on a given machine using.
Select one:
a. network interface cards
b. All of the mentioned ,t. c. Ports
0 d. DNS addresses
Answers
The correct answer is option c. Ports.
Multiple TCP streams can be distinguished on a given machine using ports. In TCP/IP networking, ports are used to identify specific applications or services running on a device. Each TCP stream is associated with a unique combination of source and destination ports, allowing the system to differentiate between multiple concurrent connections.By using different port numbers for each TCP stream, the operating system can correctly route incoming packets to the corresponding application or service, ensuring that the data is delivered to the correct destination.
Learn more about TCP here:
https://brainly.com/question/27975075
#SPJ11