A void function is one that:_____.
A. does nothing useful.
B. has an empty function body.
C. has no parameters.
D. returns a zero or null character.
E. returns no value.
Answers
A void function is one that returns no value. The correct answer is E. A void function is used when we want a function to perform a task or action without returning any value.
It does not mean that the function does nothing useful (A), has an empty function body (B), has no parameters (C), or returns a zero or null character (D). Instead, a void function simply does not have a return statement and does not return any value after completing its task.
This is commonly used when we only need the function to perform some actions or modify variables, without needing to retrieve a value.
To know more about value visit:
https://brainly.com/question/30145972
#SPJ11
Related Questions
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
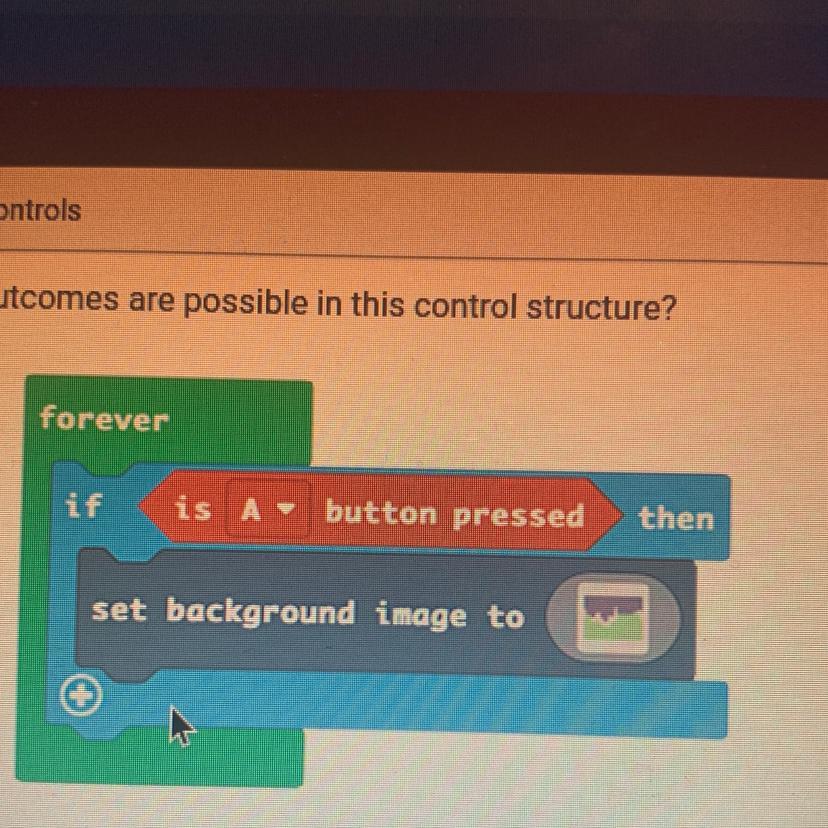
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
Write a C program to declare two integers and one float variables then initialize them to 10, 15, and 12.6. It then prints these values on the screen
Answers
Answer:
pretty simple, notice, I used '1f' so the float would print only 1 significant number after. Sure you can modify it to make it more readable and not just numbers on the screen, it's up to you
Explanation:
#include <stdio.h>
int main()
{
int n1 = 10;
int n2 = 15;
float f1 = 12.6;
printf("%d %d %.1f", n1, n2, f1);
return 0;
}
Consider an embedded computer system with 16-bit byte addressable main memory and 64 Bytes direct-mapped cache memory. The cache block size is 8 bytes. Assume that the cache is initially empty. (i) Show how the cache controller will split the memory address into different fields in order to access the cache memory. (ii) Draw a diagram of the cache organization and label the different fields in the cache memory. (iii) The CPU access the following memory locations, in that order: c88H, 774H, 79cH, COOH, 784H, c80H, 718H, c97H, 770H, 774H. All addresses are byte addresses. For each memory reference, indicate the outcome of the reference, either "hit" or "miss". (iv) What are the final contents of the cache? That is, for each cache set and each frame within a set, indicate if the frame is empty or occupied, and if occupied, indicate the tag of the main memory block that is currently present. (v) If the address 774H is currently mapped to a cache frame, what other addresses are also currently mapped to that frame?
Answers
(i) The cache controller splits the memory address into different fields: tag, index, and offset to access the cache memory.
(ii) Here is a diagram of the cache organization, with labeled fields: [diagram]
How does the cache controller access cache memory by splitting the memory address?To access the cache memory, the cache controller splits the memory address into different fields: tag, index, and offset. The tag represents the most significant bits of the memory address and helps identify which block of main memory is stored in the cache.
The index determines which cache set is being accessed, and the offset represents the position within the cache block. By dividing the memory address in this way, the cache controller can efficiently locate the desired data in the cache memory.
Cache memory plays a crucial role in improving the performance of computer systems by storing frequently accessed data closer to the processor. In this scenario, the cache is a direct-mapped cache with a block size of 8 bytes and a total capacity of 64 Bytes. The cache controller utilizes a split addressing scheme to access the cache memory.
The memory address is divided into different fields, including the tag, index, and offset. These fields allow the cache controller to determine the cache set and block within the set where the requested data may be stored. By using this approach, the cache controller can quickly determine if a memory reference results in a cache hit or miss, and efficiently retrieve data from the cache if it is available.
Learn more about cache memory
brainly.com/question/12782279
#SPJ11
An authoritative Domain Name System (DNS) server for a zone creates a Resource Records Set (RRSet) signed with a zone signing key. What is the result of this action
Answers
There are different types of systems. The result of the action above is DNS Security Extensions.
What is the reason for DNSSEC?DNS Security Extensions is known to empower the authentication in DNS through the use of digital signatures that is as a result of public key cryptography.
Through the use of DNSSEC , it is not DNS queries and responses that are said to be cryptographically signed, but instead it is the DNS data that is signed by the person who has the data.
learn more about DNS Security Extensions from
https://brainly.com/question/1139046
Recall that a floating-point number can be expressed as (−1)s(1+f)2e where s,f and e are binary numbers. Recall that s is the sign indicator, f the mantissa (or fractional part), and e the (signed) exponent. Suppose the sign is 1 bit long, the mantissa 24 bits long, and the exponent has 9 bits. What are the largest and smallest positive numbers in this computer system? Provide the theoretical expressions for the decimal version of the largest and smallest numbers, and also use Matlab to evaluate the expressions.
Answers
The largest positive number is 3.4028 x \(10^{38\) and the smallest positive number is 1.1755 x \(10^{-38\).
A floating-point number can be expressed as (-1)^s * (1+f) * 2^e, where s, f and e are binary numbers. Here, s is the sign indicator, f is the mantissa (or fractional part), and e is the (signed) exponent. If the sign is 1 bit long, the mantissa is 24 bits long, and the exponent has 9 bits, then the largest and smallest positive numbers in this computer system are as follows:Largest positive number: When all the bits are used for the mantissa and exponent, the value of f and e will be 2^24-1 and 2^9-1 respectively. This will give us the largest possible number in this computer system, which can be expressed as: (theoretical expression). Using Matlab, the expression can be evaluated as follows:>>ans = 3.4028e+38Smallest positive number: When all the bits are used for the mantissa and exponent, the value of f will be 1 and e will be -126 (the smallest possible exponent value). This will give us the smallest possible number in this computer system, which can be expressed as: (theoretical expression). Using Matlab, the expression can be evaluated as follows:>>ans = 1.1755e-38
Therefore, The largest positive number is 3.4028 x \(10^{38\) and the smallest positive number is 1.1755 x \(10^{-38\).
Learn more about Matlab :
https://brainly.com/question/33325703
#SPJ11
the d:\ drive in your computer has been formatted with ntfs. the rachel user account has been assigned the following permissions: allow full control for the d:\reports folder. deny full control for the d:\sales folder. deny full control for the d:\reports\2010reports.doc file. allow full control for the d:\sales\2010sales.doc file. which of the following best describes the effective permissions rachel will have for both files?
Answers
Deny Full Control to D:\Reports\2010reports.doc; Allow Full Control to D:\Sales\2010sales.doc
What is d drive?A common PC drive letter for a CD-ROM or other disc drive is D:. The CD-ROM drive or another disc drive is automatically designated as the D: drive on computers with a single hard drive and partition. This drive, however, can have any drive letter; nonetheless, it is frequently given the final physical drive letter.The D: drive is typically a second hard drive that is installed inside of a computer. It is frequently used to store the restore partition or to add more disc storage. Because the computer is going to be used by another employee in your office or to make some space, you can decide to delete the files on the D: drive.To learn more about d:\drive, refer to
https://brainly.com/question/21304868
#SPJ4
Enlist the main Component of each generation of computer
Answers
Answer:
First Generation - 1940 – 1956 - Vacuum Tubes.
Second Generation- 1956 – 1963- Transistors.
Third Generation - 1964 – 1971 - Integrated Circuits.
Fourth Generation- - 1972 – 2010 - Microprocessors.
Fifth Generation - 2010- present - Artificial Intelligence.
A computer is known to be an electronic machine. The main components of the computer generations are:
First Generation: This is known to have existed from 1940 – 1956. It component is that of Vacuum Tubes.Second Generation: this is known to have existed from 1956 – 1963- It man features is that of Transistors.Third Generation: Is known to be created and existed from 1964 – 1971. Its component is made up of Integrated Circuits.Fourth Generation was known to have existed between 1972 – 2010. It components is that of Microprocessors.Fifth Generation is known to be created in 2010 and it is still exiting. It component is that of Artificial Intelligence.There is the Generations of Computer that have been created by man. Due to new technologies, a lot of generation (5) have existed till date.
Learn more about Computers from
https://brainly.com/question/24540334
The Link Layer in the TCP/IP Model corresponds to the and Layers of the OSI Reference Model. A) Transport; Physical. B) Physical; Data Link.
Answers
The link layer in the TCP/IP Model corresponds to the Transport and Physical layer of the OSI Model.
What is link layer?The Internet protocol suite, or IOS, is the networking architecture of the Internet, and the link layer is the lowest layer in computer networking. The set of procedures and communication standards specific to the link to which a host is actually connected is known as the link layer.
The link is the logical and physical network component that connects hosts or nodes in the network, and a link protocol is a set of guidelines and rules that only apply to the next-to-next network nodes in a network segment.
The link layer is sometimes described as a combination of the OSI's data link layer (layer 2) and physical layer, despite the fact that the Internet protocol suite and OSI model have different definitions of layering (layer 1).
Learn more about link layer
https://brainly.com/question/29486384
#SPJ4
who can establish standard user accounts that allow alterations to security settings?
Answers
Answer: Administrators
Explanation:
Answer: Administrators
Explanation:
how do I fix this tech problem I'm having when I press ctrl it mute my sound and when I press the windows key on my keyboard it turns the pc off how to fix this issue
this was not happening yesterday please help me
Answers
Answer:
You can try reinstalling your keyboard drivers.
You can do this by right clicking the windows icon in the bottom left and click on Device Manager, find the keyboard tab and expand it, right click on your keyboard driver (it will be the same name as your keyboard, or it might have a generic name), then right click it, and press uninstall, then restart your computer to see if it worked.
If that didn't work, you can try reinstalling the USB controller drivers.
You go into device manager just like before, but find the 'Universal Serial Bus controllers' tab and uninstall the devices there, then restart.
If neither of those work, you sadly might have to get another keyboard.
Hope this helps
Unit 3 Critical thinking questions (Game Design)
3. We usually think of conflict as bad or something to be avoided. How can conflict be used to a game’s advantage in game design? Include an example.
Answers
Although conflict is frequently thought of negatively, it may also be employed to develop captivating and immersive gameplay experiences. Conflict can be utilised in game design to create tension and test players.
Conflict in video games: What is it?These are the numerous conflict kinds, along with some instances from video games. Each poses a challenge for the player to resolve. Two or more people who support opposing viewpoints. If the environment makes it impossible for a person to be in the location or state they desire.
What kind of conflict does a video game often feature?Yet, disagreements can also be caused by fear, particularly the fear of losing something—either what you already have or an opportunity.
To know more about game design visit:-
https://brainly.com/question/28753527
#SPJ1
Page orientation is determined in Microsoft Word from the __________ tab
Answers
Answer:
Page orientation is determined in Microsoft Word from the Page Layout tab.
Explanation:
The Page Layout Tab holds all the options that allow you to arrange your document pages just the way you want them. You can set margins, apply themes, control of page orientation and size, add sections and line breaks, display line numbers, and set paragraph indentation and lines.
Exercise 6.8.6: Totals of Lots of Rolls 5 points
Use the previous program that rolls a 6-sided die 100 times.
This time, instead of printing out the result of EACH roll, only print out the sum of the rolls for each number.
For example:
You rolled 24 ones.
You rolled 15 twos.
etc.
Write down the summary from one of the simulations to use in the next exercise.
Help plz
Answers
Answer: good luck
Explanation:
A modem converts original ________ signals to ________ signals that can travel down the telephone system.
Answers
A modem converts original analog signals to digital signals that can travel down the telephone system.
A modem (modulator-demodulator) is a device that transforms digital signals into analog signals. It enables data transmission via analog telephone lines, which were designed for voice communications, by transforming data from computers or other digital devices into analog signals that can be transmitted over these lines. A modem then transforms the received analog signals back into digital signals, which can then be processed by the computer. Modems are used by both personal and corporate users to connect to the internet, as well as for remote access to systems and services. They are used for many purposes, including high-speed broadband internet access, remote device control, file transfers, and online gaming.
The primary purpose of a modem is to convert digital signals into analog signals so that they can be transmitted over the phone line. This is accomplished by modulating a carrier signal to represent digital bits. A modem is also in charge of demodulating received analog signals back into digital bits. This enables a computer to communicate with another computer via a telephone line.
Learn more about modem here
https://brainly.com/question/7320816
#SPJ11
A is a necessary tool when working on a computer
Answers
When using a computer, you must have a mouse.
What makes using a computer so versatile?The most significant application that runs on your computer is the operating system. It enables the hardware and software of the computer to cooperate. Application programs carry out a wide range of tasks.
How are television signals delivered?The TV signal is wired to an antenna, which is frequently on a tall mountain or structure. An electromagnetic wave carrying the signal is sent across the atmosphere. Although these waves can move through the air at the speed of light, they can't cover very far.
To know more about computer visit:-
https://brainly.com/question/15707178
#SPJ1
A document intended for World Wide Web distribution is commonly referred to as
A. optical
B. magnetic
C. volume
D. pages
Answers
correct option is D. Web page. A document or resource on a Web site, transported over the Internet, created using the established standards, and made viewable to a user through a program called a browser.
A document intended for World Wide Web distribution is commonly referred to as a page. Thus, the correct option for this question is D.
What is a document on a world wide web called?A web page (also written as a webpage) is a document that is suitable for the World Wide Web and web browsers. It is a type of document which can be displayed in a web browser such as Firefox, Chrome, Opera, Microsoft Internet Explorer or Edge, or Apple's Safari.
According to the context of this question, a web browser takes you anywhere on the internet. It significantly retrieves information from other parts of the web and displays it on your desktop or mobile device. The information is transferred using the Hypertext Transfer Protocol, which defines how text, images, and video are transmitted on the web.
Therefore, a document intended for World Wide Web distribution is commonly referred to as a page. Thus, the correct option for this question is D.
To learn more about Web pages, refer to the link;
https://brainly.com/question/28431103
#SPJ2
Which material rendering mode uses black in the alpha channel to define where a material is NOT appearing?
Answers
The material rendering mode that uses black in the alpha channel to define where a material is NOT appearing is called "Mask" or "Masking".
In the "Mask" or "Masking" rendering mode, the alpha channel of the material defines where the material is visible or invisible. A black alpha channel means that the material is not visible in those areas.
This technique is often used in post-production compositing to selectively apply effects or adjustments to certain parts of an image based on the alpha channel.
By masking out parts of the material, you can reveal the layers underneath, creating a composite image. Masking can be done manually, or with software tools like Photoshop or After Effects.
For more questions like Mask click the link below:
https://brainly.com/question/6583003
#SPJ11
the tthe type of cable that is most likely to be used for medium-powered, network-powered broadband communication in a vertical shaft space is?ype of cable that is most likely to be used for medium-powered, network-powered broadband communication in a vertical shaft space is?
Answers
Powered broadband communication in a vertical shaft space is BMR.
What is vertical shaft?
A shaft that is lowered directly downward or at a 90-degree angle with the horizon in order to reach the planet's center.
What is BMR?
An average man has a BMR of around 7,100 kJ per day, while an average woman has a BMR of around 5,900 kJ per day. Energy expenditure is continuous, but the rate varies throughout the day. The rate of energy expenditure is usually lowest in the early morning.
Broadband, which is used in fast internet connections, is wide bandwidth data transmission that carries multiple signals at a variety of frequencies and Internet traffic types. This allows messages to be sent simultaneously. The media can be twisted pair, satellite, wireless Internet (radio), optical fiber, coaxial cable, or optical fiber.
Many computer networks employ a straightforward line code to send one kind of signal throughout the entire baseband bandwidth of the channel (from zero through the highest frequency needed). Most iterations of the widely used Ethernet family have names to denote this, such as the original from the 1980s.
Broadband refers to the wide range of frequencies that may support both many data users and conventional television channels on the same cable in networks that employ cable modems on normal cable television infrastructure. For each band in a broadband system, a distinct radio frequency modulated by the data signal is often used.
Learn more about broadband cable click here:
https://brainly.com/question/19538224
#SPJ4
reagan's firm has not had to make large investments in computer or networking hardware or in personnel to maintain the hardware because they use public cloud computing. reagan recognizes that this demonstrates which key benefit of public cloud computing? group of answer choices decreased redundancy reduced costs increased redundancy flexible capacity
Answers
Since Reagan's firm has not had to make large investments in computer or networking hardware, the key benefit of public cloud computing is option B: reduced costs.
What equipment is employed for networking?There are different kinds of equipment for networks. Hardware for networking is required for computers to communicate with one another. Bridges, hubs, as well as switches, and routers are all networking devices with slightly varied functions.
Therefore, In a public cloud, resources are made available by a third party provider through the internet and shared by businesses and individuals who want to use or buy them and low cost is a good advantage.
Learn more about cloud computing from
https://brainly.com/question/19057393
#SPJ1
Design grammars for the following languages:
a) The set of all strings of 0s and 1s such that every 0 is immediately followed by at least one 1.
b) The set of all strings of 0s and 1s that are palindromes; that is, the string reads the same backward as forward.
c) The set of all strings of 0s and 1s with an equal number of 0s and 1s.
d) The set of all strings of 0s and 1s with an unequal number of 0s and 1s.
e) The set of all strings of 0s and 1s in which 011 does not appear as a substring.
f ) The set of all strings of 0s and 1s of the form x does not equal y, where x 6= y and x and y are of the same length.
Answers
a) The grammar for the set of all strings of 0s and 1s such that every 0 is immediately followed by at least one 1 can be defined using a recursive rule. The starting symbol S generates either 1 or the string 01S.
b) Palindromic strings are those that read the same backward as forward. To generate such strings, we can use a recursive rule where the starting symbol S generates either the empty string ε, a single 0 or 1, or a string of the form 0S0 or 1S1.
c) For the set of all strings of 0s and 1s with an equal number of 0s and 1s, we can again use a recursive rule where the starting symbol S generates either the empty string ε, a 0 followed by an S and then a 1, or a 1 followed by an S and then a 0.
d) To generate strings of the set of all strings of 0s and 1s with an unequal number of 0s and 1s, we can use a rule where the starting symbol S generates either 0S1, 1S0, 0 or 1.
e) To avoid generating any substring of the form 011, we can use a recursive rule where the starting symbol S generates either the empty string ε, 0S, 1S, 00S1, 10S1 or 11S.
f ) Finally, to generate strings of the form x does not equal y, where x 6= y and x and y are of the same length, we can use a rule where the starting symbol S generates strings such as 0S1, 1S0, 01S0, 10S1, 001S, 010S, 011S, 100S, 101S or 110S.
Learn more about string here:
https://brainly.com/question/14528583
#SPJ11
Hello Everyone,
Please I have been have problems answering this question. I do not know if anyone could be of help to me.
Describe the difference between objects and values using the terms “equivalent” and “identical”. Illustrate the difference using your own examples with Python lists and the “is” operator.
Describe the relationship between objects, references, and aliasing. Again, create your own examples with Python lists.
Finally, create your own example of a function that modifies a list passed in as an argument. Describe what your function does in terms of arguments, parameters, objects, and references.
Create your own unique examples for this assignment. Do not copy them from the textbook or any other source
Answers
Objects are nothing but instance of a class. To know two objects are identical are not, use the is operator.
Is operator: The is operator is used to compare the two objects that are identical or not. The is operator returns true, if the variables on either side of the operator point to same object. If the variables on either side of the operator point to different object then it can also return true.
Value: Value is also an object that assign to a variable. Comparing to objects through === operator.
The term equivalent means.... is used to when the two operators are equal or not , if equal condition returns true.
Tasks in the ________ phase of the systems development life cycle (SDLC) are to build and test system components, and to convert users to the new system. (1pts) Question 14 - Tasks in the ________ phase of the systems development life cycle (SDLC) are to build and test system components, and to convert users to the new system. system definition component design system maintenance system implementation
Answers
Answer:
system implementation
Explanation:
breast cancer screening and health behaviors among african american and caribbean women in new york city.
Answers
A telephone-based survey regarding breast cancer screening (in terms of insurance status, marital status, and educational attainment) among 300 African American and Caribbean women in New York City aged 40 and over, it was found that they were no more likely to have had a mammogram than the foreign-born women.
Women with a provider referral were eight times more likely to have ever had a mammogram, after adjusting for insurance status and the source of care (AOR 8.01, 95%CI: 3.74-17.14). Compared to 77% of American-born women, just 52% of Caribbean women who were born abroad and have lived in the country for less than half their life had a provider ever recommend a mammogram.
The results support prior research on the significance of physician referral in increasing mammography screening among urban Black women, and they suggest that efforts to communicate breast cancer screening messages to Caribbean-born women should place a strong emphasis on the significance of providers.
Learn more about breast cancer:
https://brainly.com/question/2036981
#SPJ4
Anyone know how to take a screen shot with keyboard or keyboard shortcut on Apple iPad?
Will mark the brainliest.
Thx.

Answers
Answer: Command-Shift-3
Explanation:
Command-Shift-3 for screenshot. u can also do Command-Shift-4 if u want to edit the screenshot right away
Describe in 2-4 sentences how you would select a function.
Answers
Explanation:
You would call the capacity from the primary. At that point execute your own factors to it. When the capacity is in the cell, you can copy and after that paste it into another cell to do a similar capacity for that diverse scope of cells.
why is it recommended to disable symbolic links in mysql
Answers
MySQL is a Relational Database Management System (RDBMS) that is widely used to manage data on the web. However, there are security risks when using the MySQL database that can be mitigated by disabling symbolic links.
In most cases, MySQL symbolic links have been used to link tables to databases. By default, the MySQL database engine allows symbolic links to work in the database system. Symbolic links may create security vulnerabilities in the database system, which is why it is recommended to disable them.
Disabling symbolic links in MySQL helps prevent a hacker from exploiting symbolic links to gain access to databases on your server. The symbolic links can be exploited by hackers by first identifying the location of the MySQL configuration files, such as my.cnf and others.
In conclusion, disabling symbolic links in MySQL is essential to safeguard your data and protect your server against potential security threats. When you disable symbolic links, you are eliminating a potential security loophole that could be exploited by hackers to gain unauthorized access to your data.
Know more about the (RDBMS)
https://brainly.com/question/33356180
#SPJ11
In four to six sentences, describe how a network designer designs a plan for a network.
Answers
Answer:
Network planning and design is an iterative process, encompassing topological design, network-synthesis, and network-realization, and is aimed at ensuring that a new telecommunications network or service meets the needs of the subscriber and operator.
This could help maybe
public class BSTmn, V> { public K key; public V data; public BSTmn left, right, next, prev; public BSTmn (K key, V data) { this.key = key; this.data data; left = right right = next = prev = } null; } public class BSTm, V>{ public BSTmn root; // Return the size of the map. public int size) { } // Update the data of the key k if it exists and return true. If k does not exist, the method returns false. public boolean update (K k, v e) { } // Return true if the map is full. public boolean full(){ return false; }
Answers
The size method returns the number of nodes in the binary search tree. The update method updates the data associated with a given key if it exists in the tree. The full method checks whether the binary search tree is full (i.e., every node either has two children or no children).
Here's the complete code with missing parts filled in:
java
Copy code
public class BSTmn<K, V> {
public K key;
public V data;
public BSTmn<K, V> left, right, next, prev;
public BSTmn(K key, V data) {
this.key = key;
this.data = data;
left = right = next = prev = null;
}
}
public class BSTm<K, V> {
public BSTmn<K, V> root;
// Return the size of the map.
public int size() {
return getSize(root);
}
private int getSize(BSTmn<K, V> node) {
if (node == null)
return 0;
return 1 + getSize(node.left) + getSize(node.right);
}
// Update the data of the key k if it exists and return true.
// If k does not exist, the method returns false.
public boolean update(K k, V e) {
BSTmn<K, V> node = search(root, k);
if (node != null) {
node.data = e;
return true;
}
return false;
}
private BSTmn<K, V> search(BSTmn<K, V> node, K k) {
if (node == null || node.key.equals(k))
return node;
if (k.compareTo(node.key) < 0)
return search(node.left, k);
return search(node.right, k);
}
// Return true if the map is full.
public boolean full() {
return isFull(root);
}
private boolean isFull(BSTmn<K, V> node) {
if (node == null)
return true;
if ((node.left == null && node.right != null) || (node.left != null && node.right == null))
return false;
return isFull(node.left) && isFull(node.right);
}
}
This code defines two classes: BSTmn (representing a node in the binary search tree) and BSTm (representing the binary search tree itself). The methods size, update, and full are implemented within the BSTm class.
Know more about codehere;
https://brainly.com/question/15301012
#SPJ11
Assignment details: For this assignment, students are required to investigate the following: 1. Learn more about IoT through secondary research over the internet. a. Write only 1 paragraph about what IoT is. 2. Research the internet about IoT applications in the Agriculture field. a. Write 2 paragraphs about how IoT helped Agritech industries. b. Write about 2 innovative ideas using IoT is Agritech (1 paragraph each) 3. Suggest new applications of IoT in any field.
Answers
The Internet of Things (IoT) is a network of interconnected devices that collect and exchange data through the Internet, enabling automation, monitoring, and control of various systems.
IoT has found significant applications in the agriculture sector, revolutionizing Agritech industries by enhancing efficiency, productivity, and sustainability. Additionally, there are innovative ideas using IoT in Agritech, such as precision agriculture and smart irrigation systems. Furthermore, IoT has the potential to be applied in various other fields, including healthcare, transportation, and smart cities.
IoT is a concept that refers to a network of interconnected devices, sensors, and systems that can communicate and exchange data with each other through the Internet. These devices can range from everyday objects to complex machinery and infrastructure. The data collected by IoT devices can be analyzed and used to automate processes, improve decision-making, and optimize efficiency in various domains.
In the agriculture field, IoT has significantly impacted Agritech industries. IoT applications have enabled smart farming practices, providing real-time monitoring and control of farming operations. Farmers can utilize IoT devices to monitor soil conditions, weather patterns, crop growth, and livestock health. This data-driven approach helps optimize resource usage, enhance crop yields, and reduce environmental impact. IoT has also facilitated precision agriculture techniques, such as targeted irrigation, fertilization, and pest management, leading to better crop quality and reduced costs.
Furthermore, innovative ideas using IoT in Agritech include precision agriculture and smart irrigation systems. Precision agriculture utilizes IoT sensors and data analytics to monitor and manage crops on a precise and individualized level. This enables farmers to optimize resource allocation, minimize waste, and maximize crop yield. Smart irrigation systems utilize IoT devices to monitor soil moisture levels and weather conditions, allowing for automated and efficient irrigation management. These systems ensure that crops receive the right amount of water, reducing water usage and minimizing water wastage.
Besides the agriculture field, IoT can be applied to various other domains. In healthcare, IoT can enable remote patient monitoring, smart medical devices, and real-time health data analysis. In transportation, IoT can be used for intelligent traffic management, vehicle tracking, and autonomous vehicle systems. In smart cities, IoT can facilitate efficient energy management, waste management, and infrastructure monitoring. The potential applications of IoT are vast and can revolutionize numerous industries by improving efficiency, sustainability, and quality of life.
Learn more about Internet of Things here:
https://brainly.com/question/29767247
#SPJ11
Tech A says that when disconnecting the battery, remove the positive terminal from the battery first. Tech B says that it is often easier to disconnect main wire harnesses at their central connector instead of at the end of each branch. Who is correct
Answers
There are a lot of mechanic engineers. From the above scenario, Neither A or B is correct.
What should you remove first?In the act of disconnecting the cables from any old battery, it is better to disconnect the negative first, then later on the positive.
When connecting the new battery in a kind of reverse order, the positive one comes first and then the negative one. When a person is replacing their car battery, It is not easy to known the order in which to disconnect the terminals but always known the negative before positive one.
Learn more about Battery terminal from
https://brainly.com/question/14883923